¼ø¶È»ñÎÁ/09
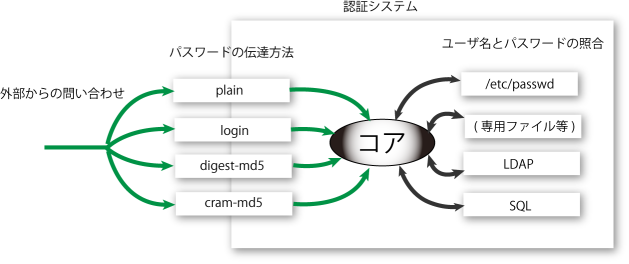
ǧ¾Ú¥·¥¹¥Æ¥à¤Ë¤Ä¤¤¤Æ°ìÈÌŪ¤ÊÏà †
unix ¥µ¡¼¥Ð¤Ë¸Â¤é¤º¡¤¥³¥ó¥Ô¥å¡¼¥¿°ìÈ̤ˡÖǧ¾Ú¡×¤È¤¤¤¦»ÅÁȤߤÏÉԲķç¤Ç¤¢¤ë.
´ðËÜŪ¤Ë¡¤´í¸±¤ÊÎΰè¤Ç¤¢¤ë¥¤¥ó¥¿¡¼¥Í¥Ã¥È¾å¤ò¥Ñ¥¹¥ï¡¼¥É¤ò¤É¤Î¤è¤¦¤Ë¤ä¤ê¤È¤ê¤¹¤ë¤«¡¤¥Ñ¥¹¥ï¡¼¥É¤È¥æ¡¼¥¶Ì¾¤Ê¤É¤Î¾È¹ç¤ò¤É¤Î¤è¤¦¤Ë¹Ô¤¦¤Î¤«¤ÎÆóÅÀ¤Ë¤Ä¤¤¤ÆÍÍ¡¹¤ÊÊýË¡¤¬¤¢¤ê¡¤¤³¤ì¤é¤ò½ÀÆð¤ËÁª¤Ù¤ë¤è¤¦¤Ë¤Ê¤Ã¤Æ¤¤¤ë¤â¤Î¤¬Â¿¤¤.
¤½¤Î¤¿¤á¤Ë½é³Ø¼Ô¤Ë¤Ïº®Í𤬤¢¤ë¤«¤È»×¤¦¤¬¡¤¼ÂºÝ¤Ï¤³¤ÎÆ󥫽ê¤ÎÁªÂò¤À¤È¤¤¤¦¹½¿Þ¤¬Ê¬¤«¤ì¤Ðʬ¤«¤ê¤ä¤¹¤¤¤À¤í¤¦.
¼ÂºÝ¡¤¤ª¤ª¤Þ¤«¤Ë¤Ï¡¤unix ¾å¤Ç¤Î¥½¥Õ¥È¥¦¥§¥¢¤ÏÄ̾ï¤Ï°Ê²¼¤Î¿Þ¤Î¤è¤¦¤Ê¹½Â¤¤ò¤·¤Æ¤¤¤ë¤Î¤Ç¡¤¤³¤Î¹½¿Þ¤òƬ¤Ë¤¤¤ì¤Æ°Ê²¼¤ÎÏäòÆɤá¤Ð¤ï¤«¤ë¤À¤í¤¦.
SMTP Auth ¤ò»È¤¦ †
SMTP Auth ¤ò»È¤¦½àÈ÷¡Ä¤Î½àÈ÷ †
¤è¤ê¼«Í³¤Ë MTA ¤ò»È¤¦¤¿¤á¤Ë SMTP Auth ¤òÍøÍѤ¹¤ë¤³¤È¤òÁÛÄꤷ¤è¤¦.
¤µ¤Æ¡¤¤Þ¤º¤Ï postfix ¤Î smtp auth ¤¬»È¤¦¤È¤µ¤ì¤Æ¤¤¤ë cyrus-sasl2 ¤Ç¤¢¤ë¤¬¡¤ºÇ½é¤«¤é¥¤¥ó¥¹¥È¡¼¥ë¤µ¤ì¤Æ¤¤¤ë¤â¤Î¤Ï¾¯¤·¤À¤±¸Å¤¤(2.3.1)¤¿¤á¥Ð¡¼¥¸¥ç¥ó¥¢¥Ã¥×¤·¤Æ¤ª¤³¤¦(2.3.1_1 ¤Ë¤Ê¤ë¤Ï¤º)¡¥
¤¤¤Ä¤â¤Î¤è¤¦¤Ë
portsnap fetch; portsnap update
¤Ç ports ¾ðÊó¤ò¹¹¿·¤·¤Æ¤ª¤¤¤Æ¤«¤é¡¤
portupgrade cyrus-sasl
¤È¤¹¤ì¤Ð¤è¤¤¡¥
¤µ¤Æ¡¤¤Þ¤º¤Ï¤³¤Î¥¤¥ó¥¹¥È¡¼¥ë¥í¥°¤òÄ´¤Ù¤è¤¦¡¥
/var/log/ports/security::cyrus-sasl2.log ¤¬¥¤¥ó¥¹¥È¡¼¥ë»þ¤Î¥í¥°¤Î¤Ï¤º¤Ê¤Î¤Ç¤³¤ì¤òÆɤà¤È¡¤
----------------------------------------------------------------------
Libraries have been installed in:
/usr/local/lib/sasl2
¡¡
If you ever happen to want to link against installed libraries
in a given directory, LIBDIR, you must either use libtool, and
specify the full pathname of the library, or use the `-LLIBDIR'
flag during linking and do at least one of the following:
- add LIBDIR to the `LD_LIBRARY_PATH' environment variable
during execution
- add LIBDIR to the `LD_RUN_PATH' environment variable
during linking
- use the `-Wl,-rpath -Wl,LIBDIR' linker flag
¡¡
See any operating system documentation about shared libraries for
more information, such as the ld(1) and ld.so(8) manual pages.
----------------------------------------------------------------------
¤È¤¤¤¦¥é¥¤¥Ö¥é¥ê¤Ë´Ø¤¹¤ë¤¤¤Ä¤â¤Îµ½Ò¤¬²¿²ó¤«¤¢¤Ã¤¿¸å¡¤
You can use sasldb2 for authentication, to add users use:
¡¡
saslpasswd2 -c username
¡¡
If you want to enable SMTP AUTH with the system Sendmail, read
Sendmail.README
¡¡
NOTE: This port has been compiled with a default pwcheck_method of
auxprop. If you want to authenticate your user by /etc/passwd,
PAM or LDAP, install ports/security/cyrus-sasl2-saslauthd and
set sasl_pwcheck_method to saslauthd after installing the
Cyrus-IMAPd 2.X port. You should also check the
/usr/local/lib/sasl2/*.conf files for the correct
pwcheck_method.
¤È¤¤¤¦¥á¥Ã¥»¡¼¥¸¤¬¸«¤Ä¤«¤ë¡¥
¤³¤ì¤Ï¡¤
- smtp auth ¤ò¤Ä¤«¤¦¤Ê¤é¤Ð¡¤¥æ¡¼¥¶¥Ñ¥¹¥ï¡¼¥É¤ò saslpasswd2 ¥³¥Þ¥ó¥É¤ÇÄɲ令è
- ¤³¤Î port ¤Ï¥Ñ¥¹¥ï¡¼¥É¾È¹ç¤È¤·¤Æ pwcheck_method (ÀìÍÑ¥Õ¥¡¥¤¥ë¤Ë¤è¤ë¾È¹ç)µ¡Ç½¤òÄ󶡤¹¤ë¤¬¡¤Â¾¤Î¾È¹çÊýË¡¤ò»È¤¤¤¿¤±¤ì¤Ð¤½¤ì¤ËÂбþ¤¹¤ë port ¤â¥¤¥ó¥¹¥È¡¼¥ë¤»¤è.
- cyrus sasl ¤ÎÀßÄê¥Õ¥¡¥¤¥ë¤Ï /usr/local/lib/sasl2/ °Ê²¼¤Ë¤¢¤ë(¤È¤¤¤¦¼¨º¶)
¤Ê¤É¤Î¤³¤È¤¬½ñ¤¤¤Æ¤¢¤ë¡¥
¤¿¤À¡¤¤³¤ì¤Ç¤ÏÍͻҤ¬¤Þ¤ÀÄϤá¤Ê¤¤¤Î¤Ç¡¤¾ðÊó¤ò¤µ¤é¤ËÄ´¤Ù¤è¤¦¡¥
¤Þ¤º¤Ï°ì¼¡¾ðÊ󸻤Ȥ¤¤¦¤³¤È¤Ç¡¤ËÜ²È http://www.postfix.org/ ¤Ç³Îǧ¤·¤¿¤¤¡¥
Documentation ¤ò¸«¤ë¤È¡¤³ºÅö¤·¤½¤¦¤Ê¤â¤Î¤¬¤¹¤°¸«¤Ä¤«¤ë.
¶ñÂÎŪ¤Ë¤Ï http://www.postfix.org/SASL_README.html ¤ò¥Á¥§¥Ã¥¯¤¹¤ë¤³¤È¤Ë¤Ê¤ë.
![]() ¤Ê¤ª¡¤¤³¤Î web ¤Ï°ìÈ̸þ¤±¤Ë½ñ¤¤¤Æ¤¢¤ë¤Î¤Ç FreeBSD ¤Î¾ì¹ç¤Ï /etc ¤Ï¤½¤Î¤Þ¤Þ¤« /usr/local/etc ¤ËÆɤßÂؤ¨¡¤/usr/lib ¤Ï /usr/local/lib ¤ËÆɤßÂؤ¨¤ë¤³¤È¤Ë¤Ê¤ë¡¥Î±°Õ¤·¤è¤¦¡¥
¤Ê¤ª¡¤¤³¤Î web ¤Ï°ìÈ̸þ¤±¤Ë½ñ¤¤¤Æ¤¢¤ë¤Î¤Ç FreeBSD ¤Î¾ì¹ç¤Ï /etc ¤Ï¤½¤Î¤Þ¤Þ¤« /usr/local/etc ¤ËÆɤßÂؤ¨¡¤/usr/lib ¤Ï /usr/local/lib ¤ËÆɤßÂؤ¨¤ë¤³¤È¤Ë¤Ê¤ë¡¥Î±°Õ¤·¤è¤¦¡¥
¤¹¤ë¤È¡¤¤Þ¤º¤Ï¥¤¥ó¥È¥í¥À¥¯¥·¥ç¥ó¤È¤·¤Æ¡¤
How Postfix uses SASL authentication
¡¡
SMTP servers need to decide whether an SMTP client is authorized to send mail to remote destinations, or only to destinations that the server itself is responsible for. Usually, SMTP servers allow mail to remote destinations when the client's IP address is in the "same network" as the server's IP address.
¡¡
SMTP clients outside the SMTP server's network need a different way to get "same network" privileges. To address this need, Postfix supports SASL authentication (RFC 4954, formerly RFC 2554). With this a remote SMTP client can authenticate to the Postfix SMTP server, and the Postfix SMTP client can authenticate to a remote SMTP server. Once a client is authenticated, a server can give it "same network" privileges.
¡¡
Postfix does not implement SASL itself, but instead uses existing implementations as building blocks. This means that some SASL-related configuration files will belong to Postfix, while other configuration files belong to the specific SASL implementation that Postfix will use. This document covers both the Postfix and non-Postfix configuration.
¡¡
You can read more about the following topics:
¡¡
* Configuring SASL authentication in the Postfix SMTP server
* Configuring SASL authentication in the Postfix SMTP/LMTP client
* Building Postfix with SASL support
* Using Cyrus SASL version 1.5.x
* Credits
¤È¤¢¤ë¡¥¤È¤ê¤¢¤¨¤ººÇ½é¤Î
* Configuring SASL authentication in the Postfix SMTP server
¤À¤±Æɤá¤Ð¤è¤µ¤½¤¦¤À¤È¤ï¤«¤ë¡¥
¤½¤³¤Ç¤½¤³¤òÆɤ߻Ϥá¤è¤¦¡¥¤¹¤ë¤È¡¤
Configuring SASL authentication in the Postfix SMTP server
¡¡
As mentioned earlier, SASL is implemented separately from Postfix. For this reason, configuring SASL authentication in the Postfix SMTP server involves two different steps:
¡¡
* Configuring the SASL implementation to offer a list of mechanisms that are suitable for SASL authentication and, depending on the SASL implementation used, configuring authentication backends that verify the remote SMTP client's authentication data against the system password file or some other database.
* Configuring the Postfix SMTP server to enable SASL authentication, and to authorize clients to relay mail or to control what envelope sender addresses the client may use.
¡¡
Successful authentication in the Postfix SMTP server requires a functional SASL framework. Configuring SASL should therefore always be the first step.
¤È¤¢¤ê¡¤ÆóÃʳ¬(cyrus sasl¤È postfix)¤ÎÀßÄ꤬ɬÍפǡ¤cyrus sasl ¤ÎÀßÄê¤òÀè¤Ë¤·¤í¤È¸À¤Ã¤Æ¤¤¤ë¡¥
¤½¤·¤Æ¡¤¾ÜºÙ¤Ê¹àÌܤϰʲ¼¤ÎÄ̤ꡥ
You can read more about the following topics:
¡¡
* Which SASL Implementations are supported?
* Configuring Dovecot SASL
o Postfix to Dovecot SASL communication
* Configuring Cyrus SASL
o Cyrus SASL configuration file name
o Cyrus SASL configuration file location
o Postfix to Cyrus SASL communication
* Enabling SASL authentication and authorization in the Postfix SMTP server
o Enabling SASL authentication in the Postfix SMTP server
o Postfix SMTP Server policy - SASL mechanism properties
o Enabling SASL authorization in the Postfix SMTP server
o Additional SMTP Server SASL options
* Testing SASL authentication in the Postfix SMTP server
Cyrus SASL ¤ÎÀßÄê †
¤³¤³¤«¤é¤·¤Ð¤é¤¯¤Ï Cyrus sasl ¤ÎÀßÄê¤È¤Ê¤ë¡¥½ç¤ËÆɤ߿ʤá¤è¤¦¡¥¤Þ¤º¤Ï¤É¤ó¤Ê¥½¥Õ¥È¥¦¥§¥¢¤¬ saslÍѤ˻Ȥ¨¤ë¤Î¤«¤È¤¤¤¦¤È¡¤
Which SASL Implementations are supported?
¡¡
Currently the Postfix SMTP server supports the Cyrus SASL and Dovecot SASL implementations.
¡¡
Note
¡¡
Before Postfix version 2.3, Postfix had support only for Cyrus SASL. Current Postfix versions have a plug-in architecture that can support multiple SASL implementations.
¡¡
To find out what SASL implementations are compiled into Postfix, use the following commands:
¡¡
% postconf -a (SASL support in the SMTP server)
% postconf -A (SASL support in the SMTP+LMTP client)
¡¡
These commands are available only with Postfix version 2.3 and later.
¤È¤¢¤ë¡¥¼ÂºÝ¤Ë postconf -a ¤È¤·¤Æ¤ß¤ë¤È(º£²ó¤Ï¥µ¡¼¥Ð¤ÎÏäʤΤǤ³¤Á¤é¤Î¤ß¹Í¤¨¤Æ)¡¤
cyrus
dovecot
¤È½ÐÎϤµ¤ì¤ë¤Î¤Ç¡¤postfix ¥µ¡¼¥Ð¤¬ cyrus-sasl ¤È dovecot-sasl ¤ÎξÊý¤ËÂбþ¤·¤Æ¤¤¤ë¤³¤È¤¬¤ï¤«¤ë¡¥
![]() ³Îǧ¤·¤Æ¤ª¤³¤¦¡¥
³Îǧ¤·¤Æ¤ª¤³¤¦¡¥
¼¡¤Ë¡¤º£²ó´Ø·¸¤¹¤ë cyrus-sasl ¤ÎÀßÄê¹àÌܤޤǤ¹¤¹¤á¤ÆÆɤà¤È¡¤
Configuring Cyrus SASL
¡¡
The Cyrus SASL framework supports a wide variety of applications (POP, IMAP, SMTP, etc.). Different applications may require different configurations. As a consequence each application may have its own configuration file.
¡¡
The first step configuring Cyrus SASL is to determine name and location of a configuration file that describes how the Postfix SMTP server will use the SASL framework.
¤È¤¢¤Ã¤Æ¡¤cyrus sasl ¤Ï¤¤¤í¤ó¤Ê¥¢¥×¥ê¥±¡¼¥·¥ç¥ó¤«¤é»È¤ï¤ì¤ë¤«¤é¡¤³Æ¥¢¥×¥ê¥±¡¼¥·¥ç¥ó¸þ¤±¤ÎÀßÄê¥Õ¥¡¥¤¥ë¤¬É¬ÍפÀ¡¤¤À¤«¤é¡¤¤Þ¤º¤Ï postfix ¸þ¤±¤ÎÀßÄê¥Õ¥¡¥¤¥ë¤Î̾Á°¤È¾ì½ê¤òÀßÄꤷ¤í¤è¤È¸À¤Ã¤Æ¤¤¤ë¡¥
¤½¤·¤Æ¡¤¤½¤Î¾ÜºÙ¤Ë¤Ä¤¤¤Æ¤Ï°Ê²¼¤Î¤È¤ª¤ê¡¥
¤Þ¤ºÌ¾Á°¤Ë¤Ä¤¤¤Æ¤Ï
Cyrus SASL configuration file name
¡¡
The name of the configuration file (default: smtpd.conf) is configurable. It is a concatenation from a value that the Postfix SMTP server sends to the Cyrus SASL library, and the suffix .conf, added by Cyrus SASL.
¡¡
The value sent by Postfix is the name of the server component that will use Cyrus SASL. It defaults to smtpd and is configured with one of the following variables:
¡¡
/etc/postfix/main.cf:
# Postfix 2.3 and later
smtpd_sasl_path = smtpd
¡¡
# Postfix < 2.3
smtpd_sasl_application_name = smtpd
postfix ¸þ¤±¤Î̾Á°¤Ï¥Ç¥Õ¥©¥ë¥È¤Ç¤Ï smtpd.conf ¤À¤È¸À¤Ã¤Æ¤¤¤ë¡¥
¾Ü¤·¤¯¤Ï postfix ¥µ¡¼¥Ð¡¼¤¬ cyrus sasl ¥é¥¤¥Ö¥é¥ê¤ËÄÌÃΤ¹¤ë¡Ö̾Á°¡×¤Ë .conf ¤È¤¤¤¦³ÈÄ¥»Ò¤ò¤Ä¤±¤¿¤â¤Î¤Ç¤¢¤ê¡¤¤³¤Î¡Ö̾Á°¡×¤Ï /usr/local/etc/postfix/main.cf (¤â¤·¤¯¤Ï¥Ç¥Õ¥©¥ë¥È¤Ç)¤ÇÀßÄꤵ¤ì¤Æ¤¤¤ë¡¥
ÆäËÊѤ¨¤ëɬÍפϤʤ¤¤À¤í¤¦¤«¤é¤³¤ì¤Ï¥Ç¥Õ¥©¥ë¥È¤Î¤Þ¤Þ¤Ç¤¤¤³¤¦¡¥
¼¡¤Ë¤³¤Î¥Õ¥¡¥¤¥ë smtpd.conf ¤ÎÃÖ¤¤¤Æ¤¢¤ë¾ì½ê¤Ë¤Ä¤¤¤Æ¤Ï
Cyrus SASL configuration file location
¡¡
The location where Cyrus SASL searches for the named file depends on the Cyrus SASL version and the OS/distribution used.
¡¡
You can read more about the following topics:
¡¡
* Cyrus SASL version 2.x searches for the configuration file in /usr/lib/sasl2/.
* Cyrus SASL version 2.1.22 and newer additionally search in /etc/sasl2/.
* Some Postfix distributions are modified and look for the Cyrus SASL configuration file in /etc/postfix/sasl/, /var/lib/sasl2/ etc. See the distribution-specific documentation to determine the expected location.
¡¡
Note
¡¡
Cyrus SASL searches /usr/lib/sasl2/ first. If it finds the specified configuration file there, it will not examine other locations.
¤È¡¤¡Ö´Ä¶¤Ë¤è¤Ã¤Æ°ã¤¦¤è¡¥¤Þ¤¢°ìÈÌŪ¤Ë¤Ï¤³¤ó¤Ê¤³¤È¤¬Â¿¤¤¤±¤É¡×¤È¤¤¤¦Ï䬽ñ¤¤¤Æ¤¢¤ë¡¥
¤³¤ì¤Ë¤Ä¤¤¤Æ¤ÏÀè¤Î sasl2 ¥¤¥ó¥¹¥È¡¼¥ë¥í¥°¤ÎÏäȹç¤ï¤»¤Æ¡¤
/usr/local/lib/sasl2
¤¬ smtpd.conf ¤ÎÃÖ¤¾ì½ê¤À¤È¤¤¤¦¤³¤È¤¬¤ï¤«¤ë¡¥
¤½¤³¤Ç /usr/local/lib/sasl2 ¤òÇÁ¤¤¤Æ¤ß¤ë¤È¡¤smtpd.conf ¤È¤¤¤¦¥Õ¥¡¥¤¥ë¤Ï̵¤¤¤Î¤Ç¡¤¼«Ê¬¤Çºî¤é¤Ê¤¤¤È¤¤¤±¤Ê¤¤¤³¤È¤¬¤ï¤«¤ë¡¥
![]() º£ºî¤Ã¤Æ¤ª¤³¤¦¡¥¶õ¤Ã¤Ý¤Ç¤è¤±¤ì¤Ð¡¤¥Õ¥¡¥¤¥ë¤òºî¤ë°ìÈÖ´Êñ¤ÊÊýË¡¤Ï touch ¥³¥Þ¥ó¥É¤ò»È¤¦¤â¤Î¤À¡¥¤À¤«¤é
º£ºî¤Ã¤Æ¤ª¤³¤¦¡¥¶õ¤Ã¤Ý¤Ç¤è¤±¤ì¤Ð¡¤¥Õ¥¡¥¤¥ë¤òºî¤ë°ìÈÖ´Êñ¤ÊÊýË¡¤Ï touch ¥³¥Þ¥ó¥É¤ò»È¤¦¤â¤Î¤À¡¥¤À¤«¤é
cd /usr/local/lib/sasl2 touch smtpd.conf
¤È¤¹¤ì¤Ð¤è¤¤¡¥
¤µ¤Æ¡¤¼¡¤Î¹àÌܤؿʤ⤦¡¥
Postfix to Cyrus SASL communication
¡¡
As the Postfix SMTP server is linked with the Cyrus SASL library libsasl, communication between Postfix and Cyrus SASL takes place by calling functions in the SASL library.
¡¡
The SASL library may use an external password verification service, or an internal plugin to connect to authentication backends and verify the SMTP client's authentication data against the system password file or other databases.
¡¡
The following table shows typical combinations discussed in this document:
¡¡
authentication backend password verification service / plugin
/etc/shadow saslauthd
PAM saslauthd
IMAP server saslauthd
sasldb sasldb
MySQL, PostgreSQL, SQLite sql
LDAP ldapdb
¡¡
Note
¡¡
Read the Cyrus SASL documentation for other backends it can use.
¤È¤¢¤Ã¤Æ¡¤Ç§¾Ú¥·¥¹¥Æ¥à sasl ¤È¤·¤Æ¡¤¡Ö¥æ¡¼¥¶Ì¾¤È¥Ñ¥¹¥ï¡¼¥É¤Î¾È¹ç¤ò¤É¤¦¹Ô¤¦¤«¡×¤ÎÊýË¡¤Ë¤¤¤¯¤Ä¤«¼ïÎब¤¢¤ë¤È¤¤¤¦¤³¤È¤Ë¤Ä¤¤¤Æ½Ò¤Ù¤Æ¤¤¤ë¡¥
º£²ó¤Ï°ìÈÖ´Êñ¤Ê¡Ösasl ÀìÍѤΥѥ¹¥ï¡¼¥É³ÊǼ¥Õ¥¡¥¤¥ë¤òºî¤Ã¤Æ»È¤¦¡×ÊýË¡¤òºÎÍѤ¹¤ë¡¥
¤³¤ì¤Ï¾å¤Î sasldb ¤È¤¤¤¦ÊýË¡¤Ç¤¢¤ë(¤½¤Î¥×¥é¥°¥¤¥ó̾¤â sasldb ¤À¤Í)¡¥
¤³¤Î¤¢¤È¤Ïº£²ó¤Ï´Ø·¸¤Ê¤¤ saslauthd ¤ÎÀâÌÀ¤¬Â³¤¯¤Î¤Ç¥¹¥¥Ã¥×¤·¤Æ¡¤´Ø·¸¤·¤½¤¦¤Ê¹àÌܤØÆɤ߿ʤá¤è¤¦¡¥¤¹¤ë¤È¼¡¤Î¹àÌܤˤ椤¢¤¿¤ë¡¥
Cyrus SASL Plugins - auxiliary property plugins
¡¡
Cyrus SASL uses a plugin infrastructure (called auxprop) to expand libsasl's capabilities. Currently Cyrus SASL sources provide three authentication plugins.
¡¡
Plugin Description
sasldb Accounts are stored stored in a Cyrus SASL Berkeley DB database
sql Accounts are stored in a SQL database
ldapdb Accounts are stored stored in an LDAP database
¡¡
Important
¡¡
These three plugins support shared-secret mechanisms i.e. CRAM-MD5, DIGEST-MD5 and NTLM. These mechanisms send credentials encrypted but their verification process requires the password to be available in plaintext. Consequently passwords cannot (!) be stored in encrypted form.
¤É¤¦¤ä¤é¡¤sasldb, sql, ldapdb ¤Î3¤Ä¤Î¥×¥é¥°¥¤¥ó¤Ï auxprop ¤È¤¤¤¦»ÅÁȤߤǤµ¤é¤Ë«¤Í¤é¤ì¤Æ¤¤¤ë¤è¤¦¤À¡¥
![]() Important ¤È¤·¤Æ¤È¤Æ¤âÂç»ö¤ÊÃí°Õ½ñ¤¤¬½ñ¤¤¤Æ¤¢¤ë¤Î¤Ç¤¤Á¤ó¤ÈÆɤó¤Ç¤ª¤³¤¦¡¥
Important ¤È¤·¤Æ¤È¤Æ¤âÂç»ö¤ÊÃí°Õ½ñ¤¤¬½ñ¤¤¤Æ¤¢¤ë¤Î¤Ç¤¤Á¤ó¤ÈÆɤó¤Ç¤ª¤³¤¦¡¥
¤µ¤Æ¡¤¤ï¤ì¤ï¤ì¤¬»È¤¦ sasldb ¥×¥é¥°¥¤¥ó¤ÎÀâÌÀ¤¬¼¡¤Ë³¤¯¡¥
The sasldb plugin
¡¡
The sasldb auxprop plugin authenticates SASL clients against credentials that are stored in a Berkeley DB database. The database schema is specific to Cyrus SASL. The database is usually located at /etc/sasldb2.
¡¡
Note
¡¡
The sasldb2 file contains passwords in plaintext, and should have read+write access only to user postfix or a group that postfix is member of.
¤³¤Î¾ðÊó¤Ï½ÅÍפÀ¡¥
![]() ¥Ñ¥¹¥ï¡¼¥É³ÊǼ¥Õ¥¡¥¤¥ë¤¬¤É¤¦¤Ê¤Ã¤Æ¤¤¤ë¤«³Îǧ¤·¤Æ¤ª¤³¤¦¡¥
¥Ñ¥¹¥ï¡¼¥É³ÊǼ¥Õ¥¡¥¤¥ë¤¬¤É¤¦¤Ê¤Ã¤Æ¤¤¤ë¤«³Îǧ¤·¤Æ¤ª¤³¤¦¡¥
¤³¤Î¥Õ¥¡¥¤¥ë¤Ï´û¤Ëºî¤é¤ì¤Æ¤¢¤Ã¤Æ¡¤/usr/local/etc/sasldb2.db ¤È¤¤¤¦Ì¾Á°¤ÇÃÖ¤¤¤Æ¤¢¤ë¡¥¤½¤³¤Ç¤³¤ì¤Î¡Ö»ý¤Á¼ç¤È¥Ñ¡¼¥ß¥Ã¥·¥ç¥ó¡×¤ò
ls -lg /usr/local/etc/sasldb2.db
¤È¤·¤Æ³Îǧ¤¹¤ë¡¥¤¹¤ë¤È
-rw-r----- 1 cyrus mail 16384 11·î 29 21:59 /usr/local/etc/sasldb2.db
¤Ê¤É¤È¤Ê¤ê¡¤
- »ý¤Á¼ç: cyrus
- ¥°¥ë¡¼¥×: mail
¤Ç¡¤¥Ñ¡¼¥ß¥Ã¥·¥ç¥ó¤Ï
- »ý¤Á¼ç: Æɤ߽ñ¤²Ä
- ¥°¥ë¡¼¥×: Æɤ߲Ä
- ¾: Æɤ߽ñ¤Á´¤ÆÉÔ²Ä
¤È¤Ê¤Ã¤Æ¤¤¤ë¡¥
¤½¤·¤Æ /etc/group ¥Õ¥¡¥¤¥ë¤ò¸«¤ë¤È¤ï¤«¤ë¤¬¡¤mail ¥°¥ë¡¼¥×¤Ë¤Ï postfix ¤¬½ê°¤·¤Æ¤¤¤ë¤Î¤Ç¡¤postfix ¤Ï¤³¤Î¥Õ¥¡¥¤¥ë¤òÆɤá¤ë¤Î¤ÇÆ°ºî¤Ë¤Ï»Ù¾ã¤¬¤Ê¤¤¤³¤È¤¬¤ï¤«¤ë¡¥
¤Þ¤¿¡¤¤½¤ì°Ê³°¤Î¼Ô¤«¤é¤Ï¤³¤Î¥Õ¥¡¥¤¥ë¤òÆɤळ¤È¤¬¤Ç¤¤º¡¤¥Ñ¥¹¥ï¡¼¥Éϳ¤ì¤â¤Ê¤¤¤³¤È¤¬¤ï¤«¤ë¡¥
![]() ¤³¤Î¤è¤¦¤Ê»ý¤Á¼ç¤È¥Ñ¡¼¥ß¥Ã¥·¥ç¥ó¤Ë¤Ê¤Ã¤Æ¤¤¤Ê¤¤¾ì¹ç¤Ï½¤Àµ¤·¤Æ¤ª¤³¤¦¡¥»È¤¦¥³¥Þ¥ó¥É¤Ï chown ¤È chmod ¤À¡¥»È¤¤Êý¤òÃΤé¤Ê¤¤¿Í¤Ï web ¤ò¸¡º÷¤¹¤ë¤Ê¤É¤·¤ÆÄ´¤Ù¤è¤¦¡¥
¤³¤Î¤è¤¦¤Ê»ý¤Á¼ç¤È¥Ñ¡¼¥ß¥Ã¥·¥ç¥ó¤Ë¤Ê¤Ã¤Æ¤¤¤Ê¤¤¾ì¹ç¤Ï½¤Àµ¤·¤Æ¤ª¤³¤¦¡¥»È¤¦¥³¥Þ¥ó¥É¤Ï chown ¤È chmod ¤À¡¥»È¤¤Êý¤òÃΤé¤Ê¤¤¿Í¤Ï web ¤ò¸¡º÷¤¹¤ë¤Ê¤É¤·¤ÆÄ´¤Ù¤è¤¦¡¥
¤µ¤Æ¡¤¼¡¤Ë sasl ÍѤΥѥ¹¥ï¡¼¥É¤ÎÀßÄêÊýË¡¤¬½ñ¤¤¤Æ¤¢¤ë¡¥
The saslpasswd2 command-line utility creates and maintains the database:
¡¡
% saslpasswd2 -c -u example.com username
Password:
Again (for verification):
¡¡
This command creates an account username@example.com.
¡¡
Important
¡¡
users must specify username@example.com as login name, not username.
¡¡
Run the following command to reuse the Postfix mydomain parameter value as the login domain:
¡¡
% saslpasswd2 -c -u `postconf -h mydomain` username
Password:
Again (for verification):
¡¡
Note
¡¡
Run saslpasswd2 without any options for further help on how to use the command.
Ä̾ï¤Ï¥Ñ¥¹¥ï¡¼¥É¤Î realm ¤¬ mydomain ¤ËÁêÅö¤¹¤ë¤è¤Í¡¤¤À¤«¤é¤³¤¦¤·¤è¤¦¤Í¡¤¤È¸À¤Ã¤Æ¤¤¤ë¡¥
¤¿¤À¡¤¤³¤Î realm ¤Ïpostfix ¦¤Ç¤Ï¥Ç¥Õ¥©¥ë¥È¤Ç¤Ï¥Û¥¹¥È̾¤Ç¤¢¤ë¤Î¤Ç¡¤¤³¤Îʸ¾Ï¤Ï¾¯¤·óòó÷¤òÀ¸¤¸¤Æ¤¤¤ë¡¥
![]() ¥á¡¼¥ë¥µ¡¼¥Ð¤Ï¥É¥á¥¤¥ó¤Î¥á¡¼¥ë¤ò°·¤¦¤Î¤¬Ä̾ï¤Ç¤¢¤ë¤Î¤Ç¡¤¤³¤ì¤Ï¾å¤Îʸ¾Ï¤Î¤Û¤¦¤¬¼ÂÂ֤˶ᤤ¡¥
¥á¡¼¥ë¥µ¡¼¥Ð¤Ï¥É¥á¥¤¥ó¤Î¥á¡¼¥ë¤ò°·¤¦¤Î¤¬Ä̾ï¤Ç¤¢¤ë¤Î¤Ç¡¤¤³¤ì¤Ï¾å¤Îʸ¾Ï¤Î¤Û¤¦¤¬¼ÂÂ֤˶ᤤ¡¥
¤·¤«¤·¡¤postfix ¤Î¥Ç¥Õ¥©¥ë¥ÈÃͤϤª¤½¤é¤¯¡Ö´Ö°ã¤Ã¤ÆÀßÄꤷ¤Æ¤â¾¤Î¥Þ¥·¥ó¤ËÌÂÏǤò¤«¤±¤Ê¤¤¡×¤È¤¤¤¦°Õ¿Þ¤¬¤¢¤ë¤Î¤Ç¤³¤ì¤â¤·¤«¤¿¤Ï¤Ê¤¤¤À¤í¤¦¡¥
º£²ó¤Î¤³¤Î¼ø¶È¤Ç¤Ï¡¤³Æ¥Þ¥·¥ó¤Ç¥á¡¼¥ë¤ò°·¤¦¤Î¤Ç realm ¤Ï¥Û¥¹¥È̾(¥Ç¥Õ¥©¥ë¥È)¤Ë¤·¤Æ¤ª¤¯¤³¤È¤Ë¤·¤è¤¦¡¥
![]() ¤³¤³¤Ç¥æ¡¼¥¶¤È¥Ñ¥¹¥ï¡¼¥É¤òÀßÄꤷ¤Æ¤ª¤³¤¦¡¥
¤³¤³¤Ç¥æ¡¼¥¶¤È¥Ñ¥¹¥ï¡¼¥É¤òÀßÄꤷ¤Æ¤ª¤³¤¦¡¥
¤ï¤ì¤ï¤ì¤Ï¥Ñ¥¹¥ï¡¼¥É¤Î realm ¤ò¥Û¥¹¥È̾¤Ë¤¹¤ë¤Î¤Ç¡¤Î㤨¤Ð¥æ¡¼¥¶Ì¾ test¡¤¥Ñ¥¹¥ï¡¼¥É password ¤ÇÀßÄꤹ¤ë¤Ê¤é
saslpasswd2 -c -u `postconf -h myhostname` test
¤È¤¹¤ì¤Ð¤è¤¤¡¥¤¢¤È¤ÏÀßÄê¥Ñ¥¹¥ï¡¼¥É¤ÎÆþÎϤòÍ׵ᤵ¤ì¤ë¤Î¤Ç¤½¤³¤Ç¥Ñ¥¹¥ï¡¼¥É¤òÆþ¤ì¤ë¡¥
![]() mydomain ¤Ç¤Ï¤Ê¤¯ myhostname ¤òÍѤ¤¤Æ¤¤¤ë¤³¤È¤ËÃí°Õ¤»¤è¡¥
mydomain ¤Ç¤Ï¤Ê¤¯ myhostname ¤òÍѤ¤¤Æ¤¤¤ë¤³¤È¤ËÃí°Õ¤»¤è¡¥
¤Á¤Ê¤ß¤Ë¥æ¡¼¥¶ÅÐÏ¿¤¬¤¦¤Þ¤¯¤¤¤Ã¤¿¤«¤É¤¦¤«¤ò³Î¤«¤á¤ëÊýË¡¤Ë¤Ä¤¤¤Æ¤Ï¤¹¤°µ½Ò¤¬¤¢¤ê¡¤
The sasldblistusers2 command lists all existing users in the sasldb database:
¡¡
% sasldblistusers2
username1@example.com: password1
username2@example.com: password2
¤È½ñ¤«¤ì¤Æ¤¤¤ë¡¥
![]() Áá® sasldblistusers2 ¤ò¼Â¹Ô¤·¤Æ¤ß¤è¤¦¡¥Î㤨¤Ð
Áá® sasldblistusers2 ¤ò¼Â¹Ô¤·¤Æ¤ß¤è¤¦¡¥Î㤨¤Ð
ÅÐÏ¿¤·¤¿¥æ¡¼¥¶Ì¾@¥Û¥¹¥È̾ userPassword
¤È¤¤¤¦½ÐÎϤ¬½Ð¤ì¤Ð¡¤ÅÐÏ¿¤µ¤ì¤Æ¤¤¤ë¤³¤È¤¬³Îǧ¤Ç¤¤¿¤È¤¤¤¦¤³¤È¤Ë¤Ê¤ë.
¤µ¤Æ¡¤¤³¤¦¤·¤Æºî¤Ã¤¿¥æ¡¼¥¶Ì¾¤È¥Ñ¥¹¥ï¡¼¥É¤ò³ÊǼ¤·¤¿¥Õ¥¡¥¤¥ë¤À¤¬¡¤¤³¤ì¤ò»È¤¨¤Èsasl ¤Ë»Ø¼¨¤¹¤ëɬÍפ¬¤¢¤ë¡¥
¤½¤Î¤¿¤á¤Îµ½Ò¤¬¼¡¤Ë³¤¯¡¥
Configure libsasl to use sasldb with the following instructions:
¡¡
/etc/sasl2/smtpd.conf:
pwcheck_method: auxprop
auxprop_plugin: sasldb
mech_list: PLAIN LOGIN CRAM-MD5 DIGEST-MD5 NTLM
¡¡
Note
¡¡
In the above example adjust mech_list to the mechanisms that are applicable for your environment.
![]() Ãí°Õ½ñ¤¤Ë¤â¤¢¤ë¤è¤¦¤Ë¡¤Ç§¾Ú¥á¥«¥Ë¥º¥à¤È¤·¤Æ»È¤¦¤â¤Î¤À¤±¥ê¥¹¥È¤¹¤ë¤Ù¤¤Ê¤Î¤Ç¡¤NTLM (¸Å¤¤ Windows ÍѤÎǧ¾Ú¤ÎÊýË¡)¤Ï³°¤·¤Æ¡¤/usr/local/lib/sasl2/smtpd.conf ¤Ë¼¡¤Î¤è¤¦¤Ë½ñ¤¤³¤ó¤Ç¤ª¤³¤¦¡¥
Ãí°Õ½ñ¤¤Ë¤â¤¢¤ë¤è¤¦¤Ë¡¤Ç§¾Ú¥á¥«¥Ë¥º¥à¤È¤·¤Æ»È¤¦¤â¤Î¤À¤±¥ê¥¹¥È¤¹¤ë¤Ù¤¤Ê¤Î¤Ç¡¤NTLM (¸Å¤¤ Windows ÍѤÎǧ¾Ú¤ÎÊýË¡)¤Ï³°¤·¤Æ¡¤/usr/local/lib/sasl2/smtpd.conf ¤Ë¼¡¤Î¤è¤¦¤Ë½ñ¤¤³¤ó¤Ç¤ª¤³¤¦¡¥
pwcheck_method: auxprop
auxprop_plugin: sasldb
mech_list: PLAIN LOGIN CRAM-MD5 DIGEST-MD5
¤¢¤È¤Ï cyrus sasl ¤Ë¤Ä¤¤¤Æ¤Ï´Ø·¸¤Ê¤¤µ½Ò¤¬Â³¤¯¤Î¤Ç¡¤·ë¶É cyrus sasl ¦¤ÎÀßÄê¤Ï½ªÎ»¤À¡¥
(·ë¶É¡¤¥Õ¥¡¥¤¥ë¤ò¤Ò¤È¤Äºî¤Ã¤Æ3¹Ô½ñ¤¹þ¤àºî¶È¤È¡¤¥æ¡¼¥¶¤òÅÐÏ¿¤¹¤ëºî¶È¤Î¤ß¤À¤Ã¤¿)
Postfix ¤Ç smtp auth ¤ò»È¤¦¤¿¤á¤Î½àÈ÷ †
¼¡¤Ë¡¤postfix ¦¤ÎÀßÄ꤬ɬÍפÀ¡¥web ¤ò³¤±¤ÆÆɤà¤È¡¤
Enabling SASL authentication and authorization in the Postfix SMTP server
¡¡
By default the Postfix SMTP server uses the Cyrus SASL implementation. If the Dovecot SASL implementation should be used, specify an smtpd_sasl_type value of dovecot instead of cyrus:
¡¡
/etc/postfix/main.cf:
smtpd_sasl_type = dovecot
¡¡
Additionally set the path where the Postfix SMTP server can find the Dovecot SASL socket:
¡¡
/etc/postfix/main.cf:
smtpd_sasl_path = private/auth
¡¡
Note
¡¡
This example uses a pathname relative to the Postfix queue directory, so that it will work whether or not the Postfix SMTP server runs chrooted.
¤È¤¢¤ë¤¬¡¤º£²ó¤Ï¥Ç¥Õ¥©¥ë¥È¤Î cyrus sasl ¤ò»È¤¦¤Î¤Ç¤³¤ì¤Ï´Ø·¸¤Ê¤¤¡¥
¼¡¤Ë
Enabling SASL authentication in the Postfix SMTP server
¡¡
Regardless of the SASL implementation type, enabling SMTP authentication in the Postfix SMTP server always requires setting the smtpd_sasl_auth_enable option:
¡¡
/etc/postfix/main.cf:
smtpd_sasl_auth_enable = yes
¡¡
After a "postfix reload", SMTP clients will see the additional capability AUTH in an SMTP session, followed by a list of authentication mechanisms the server supports:
¡¡
% telnet server.example.com 25
...
220 server.example.com ESMTP Postfix
EHLO client.example.com
250-server.example.com
250-PIPELINING
250-SIZE 10240000
250-AUTH DIGEST-MD5 PLAIN CRAM-MD5
...
¡¡
However not all clients recognize the AUTH capability as defined by the SASL authentication RFC. Some historical implementations expect the server to send an "=" as separator between the AUTH verb and the list of mechanisms that follows it.
¡¡
The broken_sasl_auth_clients configuration option lets Postfix repeat the AUTH statement in a form that these broken clients understand:
¡¡
/etc/postfix/main.cf:
broken_sasl_auth_clients = yes
¡¡
Note
¡¡
Enable this option for Outlook up to and including version 2003 and Outlook Express up to version 6. This option does not hurt other clients.
¡¡
After "postfix reload", the Postfix SMTP server will propagate the AUTH capability twice - once for compliant and once for broken clients:
¡¡
% telnet server.example.com 25
...
220 server.example.com ESMTP Postfix
EHLO client.example.com
250-server.example.com
250-PIPELINING
250-SIZE 10240000
250-AUTH DIGEST-MD5 PLAIN CRAM-MD5
250-AUTH=DIGEST-MD5 PLAIN CRAM-MD5
¤È¤¢¤ë¡¥
¤³¤ì¤Ë¤è¤ë¤È¡¤smtpd_sasl_auth_enable ¤ò yes ¤Ë¤¹¤ë¤À¤±¤Ç»È¤¨¤ë¤è¤¦¤Ë¤Ê¤ë¤¬¡¤Ë¿¥Þ¥¤¥¯¥í¥½¥Õ¥È¤Î¥á¡¼¥é¡¼¤¬¤³¤Î¤Þ¤Þ¤À¤È smtp auth ¤ò¤¤Á¤ó¤È°·¤¨¤Ê¤¤¤Î¤Ç broken_sasl_auth_clients ¤â yes ¤Ë¤·¤Æ¤ª¤¤¤¿Êý¤¬Îɤ¤¤è¤È¤¤¤¦¤³¤È¤¬½ñ¤¤¤Æ¤¢¤ë¡¥
¤½¤·¤Æ¡¤postfix ¤ËÀßÄê¤òºÆÆɹþ¤ß¤µ¤»¤Æ¤«¤é telnet ¥µ¡¼¥Ð 25 ¤ò¤ä¤ì¤ÐÍͻҤ¬¸«¤¨¤ë¤è¤È¤¤¤¦¤³¤È¤â½ñ¤¤¤Æ¤¢¤ë¡¥
smtpd_sasl_auth_enable = yes
broken_sasl_auth_clients = yes
¤ò postfix ¤Î main.cf ¤Ë½ñ¤¤³¤ó¤Ç¤ª¤³¤¦¡¥
¤½¤Î¸å¡¤postfix ¤ÎÀßÄê¤òºÆÆɹþ¤ß¤µ¤»¤è¤¦¡¥¶ñÂÎŪ¤Ë¤Ï
/usr/local/etc/rc.d/postfix reload
¤È¤¹¤ì¤Ð¤è¤¤¡¥
¤³¤Î¤¢¤ÈÁ°²ó¤ÈƱÍͤË
telnet localhost 25
¤È¤·¤Æ
EHLO localhost
¤È¤¹¤ë¤È
250-¥Û¥¹¥È̾
250-PIPELINING
250-SIZE 10240000
250-VRFY
250-ETRN
250-AUTH LOGIN PLAIN DIGEST-MD5 CRAM-MD5
250-AUTH=LOGIN PLAIN DIGEST-MD5 CRAM-MD5
250-ENHANCEDSTATUSCODES
250-8BITMIME
250 DSN
¤È¤Ê¤ê¡¤250-AUTH ¤Ç»Ï¤Þ¤ëÆó¹Ô¤¬Áý¤¨¤Æ¤¤¤ë¤³¤È¤¬¤ï¤«¤ë¡¥
¤³¤ì¤Ç¡¤postfix ¤¬ smtp auth Âбþ¤Ë¤Ê¤Ã¤¿¤³¤È¤¬¤ï¤«¤ë¡¥
![]() ¤â¤·¤¦¤Þ¤¯¤¤¤Ã¤Æ¤¤¤Ê¤¤¤è¤¦¤Ê¤é¤Ð¤³¤ì¤Þ¤Ç¤Îºî¶È¤ò¸«¤Ê¤ª¤½¤¦¡¥
¤â¤·¤¦¤Þ¤¯¤¤¤Ã¤Æ¤¤¤Ê¤¤¤è¤¦¤Ê¤é¤Ð¤³¤ì¤Þ¤Ç¤Îºî¶È¤ò¸«¤Ê¤ª¤½¤¦¡¥
¼¡¤Ë¡¤¥»¥¥å¥ê¥Æ¥£¤Î¥Ý¥ê¥·¡¼¤Ë¤Ä¤¤¤Æ¤ÎÀâÌÀ¤¬¤¢¤ë¡¥
Postfix SMTP Server policy - SASL mechanism properties
¡¡
The Postfix SMTP server supports policies that limit the SASL mechanisms that it makes available to clients, based on the properties of those mechanisms. The next two sections give examples of how these policies are used.
¡¡
Property Description
noanonymous Don't use mechanisms that permit anonymous authentication.
noplaintext Don't use mechanisms that transmit unencrypted username and password information.
nodictionary Don't use mechanisms that are vulnerable to dictionary attacks.
forward_secrecy Require forward secrecy between sessions (breaking one session does not break earlier sessions).
mutual_auth Use only mechanisms that authenticate both the client and the server to each other.
¡¡
Unencrypted SMTP session
¡¡
The default policy is to allow any mechanism in the Postfix SMTP server except for those based on anonymous authentication:
¡¡
/etc/postfix/main.cf:
# Specify a list of properties separated by comma or whitespace
smtpd_sasl_security_options = noanonymous
¡¡
Important
¡¡
Always set at least the noanonymous option. Otherwise, the Postfix SMTP server can give strangers the same authorization as a properly-authenticated client.
¥Ç¥Õ¥©¥ë¥È¤«¤éÊѤ¨¤ë¤Ë¤·¤Æ¤â¾¯¤Ê¤¯¤È¤â noanonymous ¤ÏÀßÄꤷ¤Æ¤ª¤±¤È¸À¤Ã¤Æ¤¤¤ë¡¥
°ì±þ /usr/local/etc/postfix/main.cf.default ¤ò¸«¤Æ¥Ç¥Õ¥©¥ë¥ÈÃͤò³Îǧ¤¹¤ë¤È³Î¤«¤Ë
smtpd_sasl_security_options = noanonymous
¤È½ñ¤¤¤Æ¤¢¤ë¤Î¤Ç¡¤¤È¤ê¤¢¤¨¤º¤³¤ì¤Ï²¿¤â¤·¤Ê¤¤¤Ç¤âºÇÄã¸Â¤ÎÀßÄê¤Ï½ÐÍè¤Æ¤¤¤ë¤³¤È¤Ë¤Ê¤ë¡¥
¼¡¤Ë TLS/SSL ¤È¤Î¤«¤é¤á¤Æ¤ÎÀßÄê¤Ë¤Ä¤¤¤Æ½ñ¤¤¤Æ¤¢¤ë¡¥
Encrypted SMTP session (TLS)
¡¡
A separate parameter controls Postfix SASL mechanism policy during a TLS-encrypted SMTP session. The default is to copy the settings from the unencrypted session:
¡¡
/etc/postfix/main.cf:
smtpd_sasl_tls_security_options = $smtpd_sasl_security_options
¡¡
A more sophisticated policy allows plaintext mechanisms, but only over a TLS-encrypted connection:
¡¡
/etc/postfix/main.cf:
smtpd_sasl_security_options = noanonymous, noplaintext
smtpd_sasl_tls_security_options = noanonymous
¡¡
To offer SASL authentication only after a TLS-encrypted session has been established specify this:
¡¡
/etc/postfix/main.cf:
smtpd_tls_auth_only = yes
¤³¤ì¤â¥Ç¥Õ¥©¥ë¥È¤Ç¤è¤±¤ì¤Ð²¿¤â¤·¤Ê¤¯¤Æ¤âÎɤ¤¤¬¡¤Â¾¤Ë¤³¤¦¤·¤¿¤±¤ì¤Ð¡Ä¤È¤¤¤¦Î㤬Æó¤Ä½ñ¤¤¤Æ¤¢¤ë¡¥
¤Þ¤¢º£²ó¤Ï¤³¤ì¤â¥Ç¥Õ¥©¥ë¥È¤Ç¤è¤«¤í¤¦¡¥
¼¡¤Ë
Enabling SASL authorization in the Postfix SMTP server
¡¡
After the client has authenticated with SASL, the Postfix SMTP server decides what the remote SMTP client will be authorized for. Examples of possible SMTP clients authorizations are:
¡¡
* Send a message to a remote recipient.
* Use a specific envelope sender in the MAIL FROM command.
¡¡
These permissions are not enabled by default.
¤È¤¢¤ê¡¤Â¾¤Ø¤Î¥á¡¼¥ëžÁ÷¤òµö¤¹¤«¡¤º¹½Ð¿Í̾¤ò¼«Í³¤Ë¤µ¤»¤ë¤«¤É¤¦¤«¤Ë¤Ä¤¤¤ÆÀßÄ꤬ɬÍפʤ³¤È¤¬¤ï¤«¤ë¡¥
¤Þ¤º¡¤
Mail relay authorization
¡¡
The permit_sasl_authenticated restriction allows SASL-authenticated SMTP clients to send mail to remote destinations. Add it to the list of smtpd_recipient_restrictions as follows:
¡¡
/etc/postfix/main.cf:
smtpd_recipient_restrictions =
...
permit_mynetworks
permit_sasl_authenticated
reject_unauth_destination
...
¤È¤¢¤ê¡¤smtp auth ¤Çǧ¾Ú¤µ¤ì¤¿¥æ¡¼¥¶¤Î¥á¡¼¥ë¤ò¾¤Î¥µ¡¼¥Ð¤ËÁ÷¤ë(žÁ÷, relay)¤³¤È¤òµö²Ä¤¹¤ë¤Ë¤Ï permit_sasl_authenticated ¤È¤¤¤¦1¹Ô¤ò postfix ¤Î main.cf ¤Îsmtpd_recipient_restrictions ¤Ë´Þ¤á¤í¡¤¤È¤¤¤¦¤³¤È¤¬¤ï¤«¤ë¡¥
![]() ¤³¤ì¤Ïµö²Ä¤·¤Æ¤ª¤¯¤Î¤¬Ä̾ï¤Î»È¤¤Êý¤À¤í¤¦¤«¤é¡¤½ñ¤Â¤¹¤³¤È¤Ë¤Ê¤ë¡¥
¤³¤ì¤Ïµö²Ä¤·¤Æ¤ª¤¯¤Î¤¬Ä̾ï¤Î»È¤¤Êý¤À¤í¤¦¤«¤é¡¤½ñ¤Â¤¹¤³¤È¤Ë¤Ê¤ë¡¥
¶ñÂÎŪ¤Ë¤Ï¡¤¥Ç¥Õ¥©¥ë¥ÈÃͤò main.cf.default ¤«¤é main.cf ¤Ë¥³¥Ô¡¼¤·¤Æ¤½¤³¤Ë½ñ¤Â¤¹¤³¤È¤Ë¤Ê¤ë¤Î¤Ç
smtpd_recipient_restrictions = permit_mynetworks, permit_sasl_authenticated, reject_unauth_destination
¤È¤¤¤¦1¹Ô(²þ¹Ô¤Ê¤·¤Ë¤·¤Æ¤ª¤¤¤¿¤Û¤¦¤¬ÌµÆñ¤«¤Ê)¤ò½ñ¤¹þ¤à¤³¤È¤Ë¤Ê¤ë¡¥
¼¡¤Ë¡¤
Envelope sender address authorization
¡¡
By default an SMTP client may specify any envelope sender address in the MAIL FROM command. That is because the Postfix SMTP server only knows the remote SMTP client hostname and IP address, but not the user who controls the remote SMTP client.
¡¡
This changes the moment an SMTP client uses SASL authentication. Now, the Postfix SMTP server knows who the sender is. Given a table of envelope sender addresses and SASL login names, the Postfix SMTP server can decide if the SASL authenticated client is allowed to use a particular envelope sender address:
¡¡
/etc/postfix/main.cf:
smtpd_sender_login_maps = hash:/etc/postfix/controlled_envelope_senders
¡¡
smtpd_recipient_restrictions =
...
reject_sender_login_mismatch
permit_sasl_authenticated
permit_mynetworks
reject_unauth_destination
...
¡¡
The controlled_envelope_senders table specifies the binding between a sender envelope address and the SASL login names that own that address:
¡¡
/etc/postfix/controlled_envelope_senders
# envelope sender owners (SASL login names)
john@example.com john@example.com
helpdesk@example.com john@example.com, mary@example.com
postmaster admin@example.com
@example.net barney, fred, john@example.com, mary@example.com
¡¡
With this, the reject_sender_login_mismatch restriction above will reject the sender address in the MAIL FROM command if smtpd_sender_login_maps does not specify the SMTP client's login name as an owner of that address.
¡¡
See also reject_authenticated_sender_login_mismatch and reject_unauthenticated_sender_login_mismatch for additional control over the SASL login name and the envelope sender.
¤È¤¤¤¦´¶¤¸¤Ç smtp auth ¤Î¥æ¡¼¥¶Ì¾¤È¼ÂºÝ¤Ë½Ð¤¹¥á¡¼¥ë¤Îº¹½Ð¿Í̾¤¬°ìÃפ¹¤ë¤«¤É¤¦¤«¤ò¥Á¥§¥Ã¥¯¤¹¤ë¤«¤Ê¤É¤Ë¤Ä¤¤¤Æ½ñ¤¤¤Æ¤¢¤ë¡¥
¤Þ¤¢¤³¤ì¤Ë¤Ä¤¤¤Æ¤Ïº£²ó¤Ï¤³¤³¤Þ¤Ç¸·¤·¤¯¤·¤Ê¤¤¤Ç¤â¤è¤¤¤Î¤Ç¡¤¤³¤³¤Ï¥¹¥¥Ã¥×¤·¤è¤¦¡¥
¼¡¤Ë¡¤ºÙ¤«¤¤¥ª¥×¥·¥ç¥ó3¤Ä¤Ë¤Ä¤¤¤ÆÀâÌÀ¤¬¤¢¤ë¡¥
Additional SMTP Server SASL options
¡¡
Postfix provides a wide range of SASL authentication configuration options. The next section lists a few that are discussed frequently. See postconf(5) for a complete list.
Default authentication domain
¡¡
Postfix can append a domain name (or any other string) to a SASL login name that does not have a domain part, e.g. "john" instead of "john@example.com":
¡¡
/etc/postfix/main.cf:
smtpd_sasl_local_domain = example.com
¡¡
This is useful as a default setting and safety net for misconfigured clients, or during a migration to an authentication method/backend that requires an authentication REALM or domain name, before all SMTP clients are configured to send such information.
Hiding SASL authentication from clients or networks
¡¡
Some clients insist on using SASL authentication if it is offered, even when they are not configured to send credentials - and therefore they will always fail and disconnect.
¡¡
Postfix can hide the AUTH capability from these clients/networks:
¡¡
/etc/postfix/main.cf:
smtpd_sasl_exceptions_networks = !192.0.2.171/32, 192.0.2.0/24
¡¡
Adding the SASL login name to mail headers
¡¡
To report SASL login names in Received: message headers (Postfix version 2.3 and later):
¡¡
/etc/postfix/main.cf:
smtpd_sasl_authenticated_header = yes
¡¡
Note
¡¡
The SASL login names will be shared with the entire world.
![]() °ì¤ÄÌܤϤʤ«¤Ê¤«ÊØÍø¤½¤¦¤À¡¥ÀßÄꤷ¤Æ¤ª¤³¤¦¡¥
°ì¤ÄÌܤϤʤ«¤Ê¤«ÊØÍø¤½¤¦¤À¡¥ÀßÄꤷ¤Æ¤ª¤³¤¦¡¥
¤¿¤À¤·¡¤¤³¤ÎÀßÄê¤Ï postfix ¤¬»È¤¦ sasl ¥Ñ¥¹¥ï¡¼¥É¤Î realm ¤½¤Î¤â¤Î¤ò»ØÄꤹ¤ë¤Î¤Ç¡¤´Ö°ã¤¨¤ë¤Èǧ¾Ú¤¬¤¦¤Þ¤¯¤¤¤«¤Ê¤¯¤Ê¤ë¤Î¤ÇÃí°Õ¤·¤è¤¦¡¥
¶ñÂÎŪ¤Ë¤Ï¡¤º£²ó¤Ï
smtpd_sasl_local_domain = q¤Û¤²¤Û¤².cl.math.sci.osaka-u.ac.jp
¤È¥Û¥¹¥È̾¤ÇÀßÄꤹ¤ë¤³¤È¤Ë¤Ê¤ë¡¥
¤³¤ì¤ÇÀßÄê¤Ï½ªÎ»¤Î¤Ï¤º¡¥
![]() postfix ¤ËÀßÄê¤òºÆÆɹþ¤ß¤µ¤»¤Æ¤ª¤³¤¦¡¥
postfix ¤ËÀßÄê¤òºÆÆɹþ¤ß¤µ¤»¤Æ¤ª¤³¤¦¡¥
SMTP Auth ¤ÎÆ°ºî³Îǧ †
½àÈ÷ †
¸å¤ÇÍѤ¤¤ë¥³¥Þ¥ó¥É mmencode ¤ò¡¤º£¤Î¤¦¤Á¤Ë¥¤¥ó¥¹¥È¡¼¥ë¤·¤Æ¤ª¤³¤¦.
¶ñÂÎŪ¤Ë¤Ï¡¤¤¤¤Ä¤â¤Î¤è¤¦¤Ë portsnap ¤Ç ports ¥³¥ì¥¯¥·¥ç¥ó¤ò¿·¤·¤¯¤·¤Æ¤ª¤¤¤Æ¤«¤é¡¤
psearch & portinstall ¤Ç¥¤¥ó¥¹¥È¡¼¥ë¤¹¤ë¤È¤¤¤¦¼ê½ç¤À¡¥
¼ÂºÝ¤Ë¼ê¤ÇÀܳ¤·¤Æ¤ß¤ë. †
SMTP Auth ¤ÇÀܳ¤¹¤ëºÝ¤Îǧ¾ÚÊýË¡¤Ë¤â¤¤¤¯¤Ä¤«¤¢¤ê¡¤¼«Í³¤ËÀßÄê¤ÇÁª¤Ö¤³¤È¤¬¤Ç¤¤ë.
º£²ó¤Î¥¤¥ó¥¹¥È¡¼¥ë¤Ç¤Ï¾å¤ÇÀßÄꤷ¤¿¤è¤¦¤Ë loginǧ¾Ú, plainǧ¾Ú¡¤Digest-MD5ǧ¾Ú, CRAM-MD5ǧ¾Ú ¤¬»È¤¨¤ë¤è¤¦¤Ë¤Ê¤Ã¤Æ¤¤¤ë¤Ï¤º¤À.
¤½¤³¤Ç¡¤¤³¤Î¤¦¤Á¤Î plainǧ¾Ú¤È CRAM-MD5ǧ¾Ú¤ò»î¤·¤Æ¤ß¤è¤¦.
¤Á¤Ê¤ß¤Ë¡¤plainǧ¾Ú¤Ï´Êñ¤ËÍøÍѤǤ¤ë¤¬°Å¹æ²½¤µ¤ì¤Æ¤¤¤Ê¤¤¤â¤Î¤Ç¡¤CRAM-MD5ǧ¾Ú¤Ï¤½¤ÎµÕ¤È»×¤¨¤Ð¤è¤¤.
¼ê¤Ç SMTP Auth ¤ò»î¤¹ : Plain ǧ¾Ú¤Î¾ì¹ç †
Plain ǧ¾Ú¤Ï¤ªµ¤³Ú¤Ê¥â¥Î¤Ç¡¤SMTP Auth »þ¤Ëʸ»úÎó "\0¥æ¡¼¥¶Ì¾\0¥Ñ¥¹¥ï¡¼¥É"*1¤ò base64 ¤Ç¥¨¥ó¥³¡¼¥É¤·¤¿¤â¤Î¤ò¥µ¡¼¥Ð¤ËÅϤ¹¤È¤¤¤¦´Êñ¤Ê»ÅÁȤߤÀ.
![]() base 64 ¤Ï°Å¹æ²½¤Ç¤Ï¤Ê¤¯¤Æ(¥³¥ó¥Ô¥å¡¼¥¿¤Ç°·¤¦¤Î¤ËÊØÍø¤Ë¤Ê¤ë¤è¤¦¤Ê)ñ¤Ê¤ëÊÑ´¹*2¤Ê¤Î¤Ç¡¤¥»¥¥å¥ê¥Æ¥£¤ÏÁ´¤¯³ÎÊݤµ¤ì¤Ê¤¤. ¤Ä¤Þ¤ê¡¤¥Ñ¥¹¥ï¡¼¥ÉÅù¤ò base64 ¥¨¥ó¥³¡¼¥É¤·¤¿¤â¤Î(¸å½Ò¤Î mmencode ¤ò¤«¤±¤¿¤â¤Î)¤ò¿Í¤Ë¶µ¤¨¤¿¤ê¤·¤Æ¤Ï¤¤¤±¤Ê¤¤.
base 64 ¤Ï°Å¹æ²½¤Ç¤Ï¤Ê¤¯¤Æ(¥³¥ó¥Ô¥å¡¼¥¿¤Ç°·¤¦¤Î¤ËÊØÍø¤Ë¤Ê¤ë¤è¤¦¤Ê)ñ¤Ê¤ëÊÑ´¹*2¤Ê¤Î¤Ç¡¤¥»¥¥å¥ê¥Æ¥£¤ÏÁ´¤¯³ÎÊݤµ¤ì¤Ê¤¤. ¤Ä¤Þ¤ê¡¤¥Ñ¥¹¥ï¡¼¥ÉÅù¤ò base64 ¥¨¥ó¥³¡¼¥É¤·¤¿¤â¤Î(¸å½Ò¤Î mmencode ¤ò¤«¤±¤¿¤â¤Î)¤ò¿Í¤Ë¶µ¤¨¤¿¤ê¤·¤Æ¤Ï¤¤¤±¤Ê¤¤.
![]()
¤µ¤Æ¡¤ÀܳÁ°¤ËÀܳ¤ËɬÍפÊʸ»úÎó¤òºî¤Ã¤Æ¤·¤Þ¤ª¤¦.
¶ñÂÎŪ¤Ë¤Ï¡¤¥³¥Þ¥ó¥É¥é¥¤¥ó¤Ç
printf '\0¥æ¡¼¥¶Ì¾\0¥Ñ¥¹¥ï¡¼¥É' | mmencode
¤È¤¹¤ì¤Ð¤è¤¤.
¥æ¡¼¥¶Ì¾¤È¥Ñ¥¹¥ï¡¼¥É¤Ï¤µ¤¤Û¤É SMTP Auth ÍÑ¤Ë saslpasswd2 ¥³¥Þ¥ó¥É¤ÇÀßÄꤷ¤¿¤â¤Î¤Ç¤¢¤ë.
¤³¤¦¤¹¤ë¤È¡¤'\0¥æ¡¼¥¶Ì¾\0¥Ñ¥¹¥ï¡¼¥É' ¤¬ base64 ¥¨¥ó¥³¡¼¥É¤µ¤ì¤¿Ê¸»úÎ󤬽ÐÎϤµ¤ì¤ë¤Î¤Ç¡¤¤³¤ì¤ò¤É¤³¤«¤ØÊݸ¤·¤Æ¤ª¤³¤¦*3.
¤Á¤Ê¤ß¤Ë¡¤Î㤨¤Ð '\0test\0password' ¤ò mmencode ¤¹¤ë¤È "AHRlc3QAcGFzc3dvcmQ=" ¤È¤Ê¤ë.
![]() ¤¢¤È¤Ï¤¤¤Ä¤â¤Î¤è¤¦¤Ë telnet localhost 25 ¤Ç¼«Á°¤Î MTA ¤ËÀܳ¤·¤Æ¤ß¤ë.
¤¢¤È¤Ï¤¤¤Ä¤â¤Î¤è¤¦¤Ë telnet localhost 25 ¤Ç¼«Á°¤Î MTA ¤ËÀܳ¤·¤Æ¤ß¤ë.
Á°¤Ë¤â¤ä¤Ã¤¿¤è¤¦¤Ë "EHLO localhost" ¤È¤·¤Æ±þÅú¤ò¿Ê¤á¡¤
250-¥Û¥¹¥È̾
250-PIPELINING
250-SIZE 10240000
250-VRFY
250-ETRN
250-AUTH LOGIN PLAIN DIGEST-MD5 CRAM-MD5
250-AUTH=LOGIN PLAIN DIGEST-MD5 CRAM-MD5
250-ENHANCEDSTATUSCODES
250-8BITMIME
250 DSN
¤³¤ÎÃʳ¬¤Ç SMTP Auth ¤Î Plain ǧ¾Ú¤ò»î¤·¤Æ¤ß¤è¤¦.
¶ñÂÎŪ¤Ë¤Ï¡¤¤³¤³¤Ç
AUTH PLAIN Àè¤Û¤Ébase64¥¨¥ó¥³¡¼¥É¤·¤Æºî¤Ã¤¿Ê¸»úÎó
¤ÈÆþÎϤ¹¤ì¤Ð¤è¤¤. Plain ǧ¾Ú¤Ï¤³¤ì¤À¤±¤ÇºÑ¤à.
¤½¤·¤Æ
235 2.7.0 Authentication successful
¤Ê¤É¤È "success" ¤Î°Õ¤¬¥á¥Ã¥»¡¼¥¸¤ÇÊ֤äƤ¯¤ì¤Ð¡¤Ç§¾Ú¤¬Ä̤俤Ȥ¤¤¦¤³¤È¤Ç OK ¤Ç¤¢¤ë.
¤¢¤È¤ÏÁ°¤ÈƱÍÍ¤Ë ^], quit ¤ÇÈ´¤±¤è¤¦.
¤¦¤Þ¤¯¤¤¤«¤Ê¤¤¿Í¤ÏÃúÇ«¤Ë¤³¤ì¤Þ¤Ç¤Îºî¶È¤ò¿¶¤êÊÖ¤í¤¦.
¼ê¤Ç SMTP Auth ¤ò»î¤¹ : CRAM-MD5 ǧ¾Ú¤Î¾ì¹ç †
CRAM-MD5ǧ¾Ú¤ÏÀè¤Î Plainǧ¾Ú¤È°ã¤Ã¤Æ¡¤¥Ñ¥¹¥ï¡¼¥É¤òʿʸ¤ÇÁ÷¤é¤Ê¤¤·Á¼°¤Ç¤¢¤ë. plain ǧ¾Ú¤È°Û¤Ê¤ê¡¤¥Í¥Ã¥È¥ï¡¼¥¯¤òÅðÄ°¤µ¤ì¤Æ¤â¤Þ¤¢°ÂÁ´¤È¤¤¤¨¤è¤¦.
¶ñÂÎŪ¤Ë¤Ï¡¤Àܳ¤¹¤ë¤È¥µ¡¼¥Ð¤¬Å¬Åö¤Êʸ»úÎó¤òÁ÷¤Ã¤Æ¤¯¤ë¤Î¤Ç¡¤¤³¤ì¤ò¥Ñ¥¹¥ï¡¼¥É¤ò¥¡¼¤Ë¤·¤Æ hmac-md5 ¤Ç¥Ï¥Ã¥·¥å¤òµá¤á(¤³¤ì¤¬¥Ñ¥¹¥ï¡¼¥É¤ò°µ½Ì, °Å¹æ²½¤·¤¿¤³¤È¤ËÁêÅö¤¹¤ë), ¥æ¡¼¥¶Ì¾¤È¤¢¤ï¤»¤Æ base64 ¥¨¥ó¥³¡¼¥É¤·¤ÆÁ÷¤êÊÖ¤·¡¤¥µ¡¼¥Ð¤ÇƱÍͤ˺î¤Ã¤¿¥Ï¥Ã¥·¥å¤ÈƱ¤¸¤Ê¤éǧ¾Ú OK ¤È¤¤¤¦´¶¤¸¤Ë¤Ê¤ë.
¤ä¤ä¤³¤·¤¤¤¬¡¤¼Â¤Ï CRAM-MD5 ¤ò¥Æ¥¹¥È¤¹¤ë¤¿¤á¤Î¥¹¥¯¥ê¥×¥È "userdb-test-cram-md5" ¤¬Â¸ºß¤¹¤ë¤Î¤Ç¡¤¤³¤ì¤ò¥¤¥ó¥¹¥È¡¼¥ë¤·¤ÆÍѤ¤¤ì¤Ð¤è¤¤.
¤¿¤À¤·¡¤¤³¤Î¥¹¥¯¥ê¥×¥È¤Ï¸å½Ò¤Î courier-imap ¤Î¥¤¥ó¥¹¥È¡¼¥ë¤Ë¤è¤Ã¤Æ¥¤¥ó¥¹¥È¡¼¥ë¤µ¤ì¤ë¤Î¤Ç¡¤¤½¤Îºî¶È¤ò¤·¤Æ¤«¤éÌá¤Ã¤Æ¤³¤Ê¤¤¤È¤¤¤±¤Ê¤¤.
![]() ¤È¤¤¤¦¤ï¤±¤Ç¡¤½é¤á¤Æ¤³¤³¤òÆɤà¾ì¹ç¤Ï¡¤¸å½Ò¤Î courier-imap ¤Î¥¤¥ó¥¹¥È¡¼¥ë¤Þ¤Ç¥¸¥ã¥ó¥×¤·¡¤¥¤¥ó¥¹¥È¡¼¥ë¤·¤¿¸å¤ËÌá¤Ã¤Æ¤¯¤ë¤³¤È.
¤È¤¤¤¦¤ï¤±¤Ç¡¤½é¤á¤Æ¤³¤³¤òÆɤà¾ì¹ç¤Ï¡¤¸å½Ò¤Î courier-imap ¤Î¥¤¥ó¥¹¥È¡¼¥ë¤Þ¤Ç¥¸¥ã¥ó¥×¤·¡¤¥¤¥ó¥¹¥È¡¼¥ë¤·¤¿¸å¤ËÌá¤Ã¤Æ¤¯¤ë¤³¤È.
°Ê²¼¤Îºî¶È¤Ë¤Ï¥³¥ó¥½¡¼¥ë¤¬Æó¤Ä°Ê¾å¤¢¤Ã¤¿Êý¤¬ÊØÍø¤Ê¤Î¤Ç¡¤X ¤ÇŬÅö¤Êʸ»úüËö¥¨¥ß¥å¥ì¡¼¥¿¤òÆó¤Äµ¯Æ°¤¹¤ë¤Ê¤É¡¤¹©Éפ·¤Æºî¶È¤·¤è¤¦.
¥³¥ó¥½¡¼¥ë¤¬1¤Ä¤·¤«ÍѰդǤ¤Ê¤¤¾ì¹ç¤Ç¤â¡¤¥Þ¥¦¥¹Áàºî¤Ç¥³¥Ô¡¼(º¸¥¯¥ê¥Ã¥¯¤ÇÁªÂò) and ¥Ú¡¼¥¹¥È(¿¿¤óÃ楯¥ê¥Ã¥¯)¤¬²Äǽ¤Ê¾ì¹ç¤¬Â¿¤¤¤Î¤Ç¡¤¥Þ¥¦¥¹Áàºî¤ò»î¤ß¤Æ¤ß¤ë¤È¤è¤¤.
°Ê¹ß¡¤¾õ¶·¤òʬ¤«¤ê¤ä¤¹¤¯¤¹¤ë¤¿¤á¤Ë 2¤Ä¤Îʸ»úüËö¥¨¥ß¥å¥ì¡¼¥¿¤òÍÑ°Õ¤·¤¿¾õ¶·¤òÁÛÄꤷ¡¤¤½¤Î³Æ¡¹¤ÎüËö¾å¤ÇÆ°¤¯¥·¥§¥ë¤ò³Æ¡¹ Shell-A, Shell-B ¤È¤·¤ÆÏäò¿Ê¤á¤è¤¦.
![]() ¤Þ¤º¡¤Shell-A ¤Ç telnet localhost 25 ¤·¤Æ¡¤EHLO localhost ¤ÈÂбþ¤·¤ÆÀè¤ÈƱ¤¸¤è¤¦¤Ë
¤Þ¤º¡¤Shell-A ¤Ç telnet localhost 25 ¤·¤Æ¡¤EHLO localhost ¤ÈÂбþ¤·¤ÆÀè¤ÈƱ¤¸¤è¤¦¤Ë
250-¥Û¥¹¥È̾
250-PIPELINING
250-SIZE 10240000
250-VRFY
250-ETRN
250-AUTH LOGIN PLAIN DIGEST-MD5 CRAM-MD5
250-AUTH=LOGIN PLAIN DIGEST-MD5 CRAM-MD5
250-ENHANCEDSTATUSCODES
250-8BITMIME
250 DSN
¤Þ¤Ç¤¹¤¹¤á¤è¤¦. ¤½¤·¤Æ¤³¤³¤Ç
auth cram-md5
¤ÈÆþÎϤ¹¤ë. ¤¹¤ë¤È¡¤
334 PG5hbmlrYW5vLXNlcnZlcj4=
¤Ê¤É¤È½ÐÎϤ¬Ê֤äƤ¯¤ë.
¤³¤Î PG5hbmlrYW5vLXNlcnZlcj4= ¤¬¥µ¡¼¥Ð¤¬ base64 ¤ÇÁ÷¤Ã¤Æ¤¤¿Ê¸»úÎó*4¤Ç¤¢¤ë¤Î¤Ç¡¤¤³¤ì¤ò¥æ¡¼¥¶¤Î¥Ñ¥¹¥ï¡¼¥É¤ò¥¡¼¤Ë¤·¤Æ hmac-md5 ¤Ç¥Ï¥Ã¥·¥å¤ò·×»»¤·¤Æ¥æ¡¼¥¶Ì¾¤È¤¢¤ï¤»¤Æ base64 ¤ÇÁ÷¤êÊÖ¤»¤Ð¤è¤¤. ¤³¤Îʸ»úÎó¤ÎÀ¸À®¤ÏÌÌÅݤˤߤ¨¤ë¤¬¡¤¤Ê¤ó¤Î¤³¤È¤Ï¤Ê¤¯¤ÆÀè¤Î¥³¥Þ¥ó¥É¤ò»È¤¨¤Ð¤è¤¤.
¶ñÂÎŪ¤Ë¤Ï Shell-B ¤Ç userdb-test-cram-md5 ¤ò¼Â¹Ô¤·¤Æ¡¤°Ê²¼¤Î¤è¤¦¤ËÂбþ¤¹¤ì¤Ð¤è¤¤.
Username? test ¢« (SMTP Auth ¤Ë»È¤¦)¥æ¡¼¥¶Ì¾¤òÆþÎϤ¹¤ë
Password? password ¢« (SMTP Auth ¤Ë»È¤¦)¥Ñ¥¹¥ï¡¼¥É¤òÆþÎϤ¹¤ë
Send: AUTH CRAM-MD5 (or for imap, A AUTHENTICATE CRAM-MD5)
Paste the challenge here:
+ PG5hbmlrYW5vLXNlcnZlcj4= ¢« Shell-A ¤Ç¥µ¡¼¥Ð¤¬Á÷¤Ã¤Æ¤¤¿Ê¸»úÎó¤òÆþÎϤ¹¤ë
Send this response:
dGVzdHVzZXIgY2NiNjc4YmZjZGY1YWRlMGUyYmE2MmM3ODA3OTA1NGI= ¢« ÊÖ¤¹¤Ù¤Ê¸»úÎ󤬽ÐÎϤµ¤ì¤ë
¤È¤Ê¤ê¡¤ºÇ¸å¤ËÊÖÅú¤¹¤Ù¤Ê¸»úÎó¤òÀ¸À®¤·¤Æ¤¯¤ì¤ë.
¤½¤³¤Ç¤³¤Îʸ»úÎó(¤³¤ÎÎã¤Î¾ì¹ç¤Ï dGVzdHVzZXIgY2NiNjc4YmZjZGY1YWRlMGUyYmE2MmM3ODA3OTA1NGI=)¤ò¤µ¤Ã¤¤Î Shell-A ¤Ç¤Îºî¶È¤Î³¤¤Ë ÆþÎϤ¹¤ë.
ǧ¾Ú¤¬Ä̤ì¤Ð¤³¤Î¤¢¤È
235 2.7.0 Authentication successful
¤Ê¤É¤È "success" ¤Î°Õ¤¬¥á¥Ã¥»¡¼¥¸¤ÇÊ֤äƤ¯¤ì¤Ð¡¤Ç§¾Ú¤¬Ä̤俤Ȥ¤¤¦¤³¤È¤Ç OK ¤Ç¤¢¤ë.
¤¢¤È¤ÏÁ°¤ÈƱÍÍ¤Ë ^], quit ¤ÇÈ´¤±¤è¤¦.
¤¦¤Þ¤¯¤¤¤«¤Ê¤¤¿Í¤ÏÃúÇ«¤Ë¤³¤ì¤Þ¤Ç¤Îºî¶È¤ò¿¶¤êÊÖ¤í¤¦.
SMTP over TLS ¤ò»È¤¦ †
SMTP over TLS ¤ÎÀßÄê †
![]() TLS ¤ÎÍøÍѤˤĤ¤¤Æ¤Ï¡¤ÀßÄê¤Î¤Þ¤¨¤Ë¸°¤È¾ÚÌÀ½ñ¤òÍÑ°Õ¤·¤Ê¤¤¤È¤¤¤±¤Ê¤¤.
TLS ¤ÎÍøÍѤˤĤ¤¤Æ¤Ï¡¤ÀßÄê¤Î¤Þ¤¨¤Ë¸°¤È¾ÚÌÀ½ñ¤òÍÑ°Õ¤·¤Ê¤¤¤È¤¤¤±¤Ê¤¤.
ÆóÅÙ¼ê´Ö¤Ê¤Î¤Ç¡¤web server ¤ÎÀßÄê¤Î»þ¤Ëºî¤Ã¤¿¸°¤È¾ÚÌÀ½ñ¤ò¤½¤Î¤Þ¤Þ¥³¥Ô¡¼¤·¤Æ»È¤ª¤¦¡¥
cd /usr/local/etc/postfix cp ../apache22/apache.key ./postfix.key cp ../apache22/apache.crt ./postfix.crt
¥Ñ¡¼¥ß¥Ã¥·¥ç¥ó¤Ë¤âµ¤¤ò¤Ä¤±¤Æ¡¤
chmod 400 postfix.key chmod 400 postfix.crt
¤È¤·¤Æ¤ª¤³¤¦.
¤µ¤Æ¡¤Postfix ¤ÎÀßÄê¤Ï¡¤ËܲȤΥɥ¥å¥á¥ó¥È( http://www.postfix.org/TLS_README.html )¤òÆɤó¤Ç¼«Ê¬¤Ê¤ê¤Ë¼è¼ÎÁªÂò¤¹¤ë¤³¤È¤Ë¤Ê¤ë.
¥µ¡¼¥Ð¤«¥¯¥é¥¤¥¢¥ó¥È¤«¤äǧ¾Ú¤ò¤É¤¦¤¹¤ë¤«¤Ê¤É¿¾¯¤ä¤ä¤³¤·¤¯¤Æ¤è¤¯¤ï¤«¤é¤Ê¤¤¤«¤È»×¤¦¤Î¤Ç¡¤º£²ó¤ÏÀßÄê¤ò½ñ¤¤¤Æ¤·¤Þ¤ª¤¦.
![]() º£²ó¤Ï¡¤ /usr/local/etc/postfix/main.cf ¤Ë
º£²ó¤Ï¡¤ /usr/local/etc/postfix/main.cf ¤Ë
smtpd_tls_cert_file = /usr/local/etc/postfix/postfix.crt
smtpd_tls_key_file = /usr/local/etc/postfix/postfix.key
smtpd_tls_loglevel = 1
smtpd_tls_received_header = yes
smtpd_tls_security_level = may
¡¡
smtp_tls_loglevel = 1
smtp_tls_security_level = may
smtp_tls_note_starttls_offer = yes
¤Ê¤É¤È²Ã¤¨¤ì¤ÐÎɤ¤.
¤¿¤À¤·¡¤¤³¤ì¤Ï·ÐÏ©¤Î°Å¹æ²½¤À¤±¤Ç¤è¤¤¡¤¤È¤¤¤¦ÀßÄê¤Ê¤Î¤Ç¡¤Ç§¾Ú¤Þ¤Ç¤¤Á¤ó¤È¤·¤¿¤¤¿Í¤Ï¥É¥¥å¥á¥ó¥È¤ò¤¤Á¤ó¤ÈÆɤ⤦.
![]() Postfix ¤ÎÀßÄêÊýË¡¤¬¶áǯÊѤï¤Ã¤¿¤¿¤á¡¤web ¾å¤Ç»²¾È¤Ç¤¤ëÀßÄê¤Î¿¤¯¤Ï´û¤Ë¸Å¤¯¡¤¤¢¤Þ¤ê¿ä¾©¤Ç¤¤Ê¤¤¤Î¤Çα°Õ¤¹¤ë¤³¤È.
Postfix ¤ÎÀßÄêÊýË¡¤¬¶áǯÊѤï¤Ã¤¿¤¿¤á¡¤web ¾å¤Ç»²¾È¤Ç¤¤ëÀßÄê¤Î¿¤¯¤Ï´û¤Ë¸Å¤¯¡¤¤¢¤Þ¤ê¿ä¾©¤Ç¤¤Ê¤¤¤Î¤Çα°Õ¤¹¤ë¤³¤È.
¤³¤ÎÊÔ½¸¤¬½ª¤ï¤Ã¤¿¤é¡¤postfix ¤ËÀßÄê¤òºÆÆɹþ¤µ¤»¤ì¤ÐÎɤ¤¡¥
SMTP over TLS ¤ÎÆ°ºî³Îǧ †
![]() telnet localhost 25 ¤Ç³Îǧ¤·¤Æ¤ß¤è¤¦.
telnet localhost 25 ¤Ç³Îǧ¤·¤Æ¤ß¤è¤¦.
¤³¤ì¤Þ¤Ç¤ÈƱÍÍ¤Ë EHLO localhost ¤·¤Æ, ±þÅú¤¬
250-¥Û¥¹¥È̾
250-SIZE 10240000
250-VRFY
250-ETRN
250-STARTTLS ¢« ¤³¤ÎÂбþ¤¬ TLS/SSL ÍѤΤâ¤Î
250-AUTH LOGIN PLAIN DIGEST-MD5 CRAM-MD5
250-AUTH=LOGIN PLAIN DIGEST-MD5 CRAM-MD5
250-ENHANCEDSTATUSCODES
250-8BITMIME
250 DSN
¤Ê¤É¤È¤Ê¤ë.
¾å¤Î¤è¤¦¤Ë "250-STARTTLS" ¤È¤¤¤¦Éôʬ¤¬¤¢¤ì¤Ð¡¤¤È¤ê¤¢¤¨¤º TLS Âбþ¤ÎÆ°ºî¤ò¤·¤Æ¤¤¤ë¤³¤È¤¬¤ï¤«¤ë.
¤¢¤È¤ÏÁ°¤ÈƱÍÍ¤Ë ^], quit ¤ÇÈ´¤±¤è¤¦.
¤³¤ì¤¬½Ð¤Ê¤¤¤è¤¦¤Ê¤é²¿¤«¤ª¤«¤·¤¤¤Î¤Ç¤³¤ì¤Þ¤Ç¤Îºî¶È¤ò¿¶¤êÊÖ¤í¤¦.
![]()
¤µ¤Æ¡¤¤³¤³¤Ç SMTP ¤ÎÆ°ºî¥Á¥§¥Ã¥¯¤ËÊØÍø¤Ê¥Ä¡¼¥ë¤òƳÆþ¤·¤è¤¦. °Ê¹ß¤Î³Îǧºî¶È¤¬³Ú¤Ë¤Ê¤ë.
¤½¤ì¤Ï swaks (Swiss Army Knife SMTP) ¤È¤è¤Ð¤ì¤ë¤â¤Î¤Ç¤¢¤ê¡¤¤³¤ì¤Þ¤Ç¤Î telnet localhost 25 ¤È¤¤¤¦°ìÏ¢¤Îºî¶È¤ò¼«Æ°Åª¤Ë¤ä¤Ã¤Æ¤¯¤ì¤ëÊØÍø¤Ê¤â¤Î¤Ç¤¢¤ë.
¤È¤¤¤¦¤ï¤±¤Ç¤¤¤Ä¤â¤Î¤è¤¦¤Ë(psearch ¤Çõ¤·¤Æ) swaks ¤ò¥¤¥ó¥¹¥È¡¼¥ë¤·¤è¤¦.
portinstall mail/swaks
¤È¤¹¤ì¤Ð¤è¤¤. ¥¤¥ó¥¹¥È¡¼¥ë»þ¤Ë¥ª¥×¥·¥ç¥óÁªÂò²èÌÌ
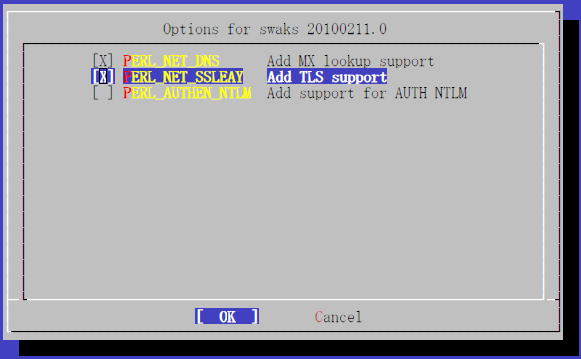
¤¬½Ð¤¿¤é¡¤¾¯¤Ê¤¯¤È¤â "MX lookup support" ¤È "TLS support" ¤È¤ò ON ¤Ë¤·¤Æ¤ª¤¤¤Æ¤«¤é¥¤¥ó¥¹¥È¡¼¥ë¤·¤è¤¦.
NTLM ¤Ïº£²ó¤Ï´Ø·¸¤Ê¤¤¤Î¤Ç³°¤·¤¿¤Þ¤Þ¤Ç¤è¤¤¤À¤í¤¦.
Àè¤Ø¿Ê¤à¤È¡¤p5-Net-DNS ¤Î¥¤¥ó¥¹¥È¡¼¥ë»þ¤Ë IPv6 ¤ò͸ú¤Ë¤¹¤ë¤«¤È¤¤¤¦¥ª¥×¥·¥ç¥ó¤òʹ¤«¤ì¤ë¤¬¡¤¤³¤ì¤Ï³°¤·¤Æ¤ª¤³¤¦¡¥
¤µ¤é¤Ë¡¤p5-Net-SSLeay ¤Î¥¤¥ó¥¹¥È¡¼¥ë»þ¤Ë¥Æ¥¹¥È¤ò¤¹¤ë¤«¤É¤¦¤«Ê¹¤«¤ì¤ë¤³¤È¤¬¤¢¤ë¤¬¡¤¤³¤ì¤Ï "n" ¤Î¤Þ¤Þ¤Ç¹½¤ï¤Ê¤¤.
¤¢¤È¤Ï¥¤¥ó¥¹¥È¡¼¥ë¤¬½ª¤ï¤ë¤Î¤ò¤Þ¤È¤¦.
¥¤¥ó¥¹¥È¡¼¥ë»þ¤ÎºÇ¸å¤Ë¡¤¿ÆÀڤˤâ
Try
`swaks --help'
to list the available options and
`swaks --support'
for a list of capabilities.
¤È¶µ¤¨¤Æ¤¯¤ì¤ë¤Î¤Ç¡¤³Ð¤¨¤Æ¤ª¤³¤¦¡¥
¤µ¤Æ,¤Þ¤º¤Ï¤ª¤µ¤é¤¤¤â·ó¤Í¤Æ¤³¤ì¤Þ¤Ç¤Î¥Æ¥¹¥È¤òºÆ¸½¤·¤Æ¤ß¤è¤¦.
![]() ¤Þ¤º¤Ïñ¤Ë MTA ¤¬Æ°ºî¤·¤Æ¤¤¤ë¤«¤Î³Îǧ¤ò¤·¤è¤¦.
¤Þ¤º¤Ïñ¤Ë MTA ¤¬Æ°ºî¤·¤Æ¤¤¤ë¤«¤Î³Îǧ¤ò¤·¤è¤¦.
swaks --server localhost
¤È¤¹¤ë¤È¡¤¥Æ¥¹¥È¥á¡¼¥ë¤Î°¸Àè¤òʹ¤¤¤Æ¤¯¤ë¤Î¤Ç, ¼«Ê¬¤Î¥¢¥«¥¦¥ó¥È̾¤òÅú¤¨¤è¤¦. ¤¹¤ë¤È
=== Trying localhost:25...
=== Connected to localhost.
<- 220 ¥Û¥¹¥È̾ ESMTP Postfix
-> EHLO ¥Û¥¹¥È̾¤ÎƬÉôʬ
<- 250-¥Û¥¹¥È̾
<- 250-PIPELINING
<- 250-SIZE 10240000
<- 250-VRFY
<- 250-ETRN
<- 250-STARTTLS
<- 250-AUTH LOGIN PLAIN DIGEST-MD5 CRAM-MD5
<- 250-AUTH=LOGIN PLAIN DIGEST-MD5 CRAM-MD5
<- 250-ENHANCEDSTATUSCODES
<- 250-8BITMIME
<- 250 DSN
-> MAIL FROM:<º¹½Ð¿Í@¥Û¥¹¥È̾¤ÎƬÉôʬ>
<- 250 2.1.0 Ok
-> RCPT TO:<°¸Àè¥æ¡¼¥¶Ì¾>
<- 250 2.1.5 Ok
-> DATA
<- 354 End data with <CR><LF>.<CR><LF>
-> Date: Tue, 30 Nov 2010 20:19:53 +0900
-> To: °¸Àè¥æ¡¼¥¶Ì¾
-> From: º¹½Ð¿Í@¥Û¥¹¥È̾¤ÎƬÉôʬ
-> Subject: test Tue, 30 Nov 2010 20:19:53 +0900
-> X-Mailer: swaks v20100211.0 jetmore.org/john/code/swaks/
->
-> This is a test mailing
->
-> .
<- 250 2.0.0 Ok: queued as B8D822865
-> QUIT
<- 221 2.0.0 Bye
=== Connection closed with remote host.
¤È MTA ¤È¤ä¤ê¼è¤ê¤·¤Æ¡¤¤½¤ÎÅÓÃæ·Ð²á¤ò¤¤Á¤ó¤È½ÐÎϤ·¤Æ¤¯¤ì¤ë.
¤¤¤Þ¤Ï¥Æ¥¹¥È¥á¡¼¥ë¤ò¼ÂºÝ¤ËÁ÷¤Ã¤¿¤Ï¤º¤Ê¤Î¤Ç¡¤¥¢¥«¥¦¥ó¥È¤Î¥Û¡¼¥à¥Ç¥£¥ì¥¯¥È¥ê¤Î Maildir/new ¤Ë¥á¡¼¥ë¤¬ÆϤ¤¤Æ¤¤¤ë¤Ï¤º¤Ç¤¢¤ë. ³Îǧ¤·¤Æ¤ß¤è¤¦.
¼¡¤Ë¡¤SMTP Auth ¤Î plainǧ¾Ú¤ò»î¤·¤Æ¤ß¤è¤¦.
¤¿¤À¤·¡¤¤¤¤Á¤¤¤Á¥á¡¼¥ë¤¬ÆϤ¯É¬Íפâ¤â¤¦¤Ê¤¤¤Î¤Ç¡¤Æ°ºî³Îǧ¤Î¤ß¤Ç¥á¡¼¥ë¤ÏÁ÷¤é¤Ê¤¤¤è¤¦¤Ë¤·¤è¤¦.
¤½¤ì¤Ë¤Ï¼¡¤Î¤è¤¦¤Ë¤¹¤ì¤Ð¤è¤¤.
swaks --auth PLAIN --server localhost --quit RCPT
¤¹¤ë¤ÈºÇ½é¤Ë(¼ÂºÝ¤Ë¤ÏÁ÷¤é¤Ê¤¤¤¬)¥Æ¥¹¥È¥á¡¼¥ë¤Î°¸Àè¤òʹ¤¤¤Æ¤¤Æ¡¤¤½¤Î¸å¤Ë SMTP Auth ¤Îǧ¾Ú¤ËɬÍפʥ桼¥¶Ì¾¤È¥Ñ¥¹¥ï¡¼¥É¤òʹ¤¤¤Æ¤¯¤ë¤Î¤ÇÅú¤¨¤è¤¦.
¤½¤·¤Æ¡¤¤½¤Î¸å¤Î¤ä¤ê¤È¤ê¤ÎÅÓÃæ¤Ë
¡Äά¡Ä
-> AUTH PLAIN ¥Ñ¥¹¥ï¡¼¥É¤òbase64²½¤·¤¿¤â¤Î
<- 235 2.7.0 Authentication successful
¡Äά¡Ä
¤È¤¤¤¦¤è¤¦¤Ë Auth plain ¤Ç¤Î SMTP Auth ¤¬¤¦¤Þ¤¯¤¤¤Ã¤¿¡¤¤È¤¤¤¦¤³¤È¤¬³Îǧ¤Ç¤¤ì¤Ð OK ¤À.
¼¡¤Ë SMTP Auth ¤Î CRAM-MD5 ǧ¾Ú¤ò»î¤·¤Æ¤ß¤ë. ¤½¤ì¤Ë¤Ï
swaks --auth CRAM-MD5 --server localhost --quit RCPT
¤È¤¹¤ì¤Ð¤è¤¤. ÆþÎϤϾå¤ÈƱÍͤÀ.
¤½¤·¤Æ¡¤¤½¤Î¸å¤Î¤ä¤ê¤È¤ê¤ÎÅÓÃæ¤Ë
¡Äά¡Ä
-> AUTH CRAM-MD5
<- 334 PDI3NTg4NzIyNTMuNDY4OTgzOUBGcmVlQlNENy5jYXMuY21jLm9zYWthLXUuYWMuanA+
-> cGFvb24gMTgyODJmNzRhNjZhOWMwY2FjN2YzZTliNDQ2NzQ3Y2Y=
<- 235 2.7.0 Authentication successful
¡Äά¡Ä
¤È¤¤¤¦¤è¤¦¤Ë Auth CRAM-MD5 ¤Ç¤Î SMTP Auth ¤¬¤¦¤Þ¤¯¤¤¤Ã¤¿¡¤¤È¤¤¤¦¤³¤È¤¬³Îǧ¤Ç¤¤ì¤Ð OK ¤À.
¤µ¤Æ¡¤¤ä¤Ã¤È´Î¿´¤Î SMTP over TLS ¤ò¥Æ¥¹¥È¤·¤è¤¦. ¤È¤¤¤Ã¤Æ¤â¤³¤³¤Þ¤Ç¤¯¤ì¤Ð¥Æ¥¹¥È¤Ï¤â¤¦´Êñ¤Ç¡¤
swaks -tls --server localhost
¤È¤¹¤ì¤Ð¤è¤¤. ¤¿¤À¤·¡¤Ç°¤Î°Ù¤Ë¥Æ¥¹¥È¥á¡¼¥ë¤ò¼ÂºÝ¤ËÁ÷¤í¤¦¤È¤·¤Æ¤¤¤ë.
¤³¤ì¤ò¼Â¹Ô¤·¤Æ¡¤swaks ¤Î½ÐÎϤ¬
¡Äά¡Ä
-> STARTTLS
<- 220 2.0.0 Ready to start TLS
=== TLS started w/ cipher DHE-RSA-AES256-SHA
¡Äά¡Ä
¤È¤¤¤¦¤è¤¦¤Ë TLS ¤ò»È¤Ã¤Æ̵»ö¤ËÆ°¤¤¤Æ¤¤¤ë¤è¤¦¤Ê¤é¤ÐÂç¾æÉפÀ.
¤â¤Á¤í¤ó, Maildir/new ¤Ë¼ÂºÝ¤Ë¥á¡¼¥ë¤¬ÆϤ¤¤Æ¤¤¤ë¤«¤â¥Á¥§¥Ã¥¯¤·¡¤¤½¤Î¥á¡¼¥ë¤Î¥Ø¥Ã¥ÀÉôʬ¤Ë
(using TLSv1 with cipher DHE-RSA-AES256-SHA (256/256 bits))
¤È¤¤¤¦µ½Ò¤¬¤¢¤ë¤³¤È¤â³Îǧ¤·¤Æ¤ª¤³¤¦.
ºÇ¸å¤Ë¡¤SMTP Auth ¤È SMTP over TLS ¤òÁȤ߹ç¤ï¤»¤Æ¤ß¤è¤¦. SMTP Auth ¤Îǧ¾Ú¤Ï¤Ê¤ó¤Ç¤â¤è¤¤. ¹¥¤¤Ê¤â¤Î¤ò»È¤Ã¤Æ¤ä¤Ã¤Æ¤ß¤è¤¦.
¶ñÂÎŪ¤Ë¤Ï¡¤Î㤨¤Ð¼¡¤Î¤è¤¦¤Ë¤¹¤ì¤Ð¤è¤¤(SMTP Auth ¤Ï¼«Æ°Åª¤ËÁª¤ó¤Ç¤â¤é¤¦ÀßÄê).
swaks --auth -tls --server localhost --quit RCPT
¤³¤³¤Ç½ÐÎϤòÃúÇ«¤ËÆɤó¤Ç¤ß¤è¤¦.
![]() ¤³¤Î½ÐÎϤòÆɤà¤È starttls ¤·¤Æ¤«¤é SMTP Auth¤·¤Æ¤¤¤ë ¤³¤È, ¤Ä¤Þ¤ê¡¤¡Ö°Å¹æ²½¤ò»Ï¤á¤Æ¤«¤é¥Ñ¥¹¥ï¡¼¥É¤ò¤ä¤ê¼è¤ê¤¹¤ë¡×½çÈ֤ˤʤäƤ¤¤ë¤³¤È¤ËÃíÌܤ»¤è.
¤³¤Î½ÐÎϤòÆɤà¤È starttls ¤·¤Æ¤«¤é SMTP Auth¤·¤Æ¤¤¤ë ¤³¤È, ¤Ä¤Þ¤ê¡¤¡Ö°Å¹æ²½¤ò»Ï¤á¤Æ¤«¤é¥Ñ¥¹¥ï¡¼¥É¤ò¤ä¤ê¼è¤ê¤¹¤ë¡×½çÈ֤ˤʤäƤ¤¤ë¤³¤È¤ËÃíÌܤ»¤è.
¤³¤ì¤Ï SMTP over TLS ¤ÈÁȤ߹ç¤ï¤»¤ë¤Ê¤é¤Ðǧ¾Ú(¥Ñ¥¹¥ï¡¼¥É¤Î¤ä¤ê¼è¤ê)¤Ïʿʸ¤Ç¤â°ÂÁ´¤Ê¤Ï¤º¤È¤¤¤¦¤³¤È¤Ç¤¢¤ë.
µÕ¤Ë¸À¤¨¤Ð¡¤over TLS ¤·¤Æ¤¤¤Ê¤¤¤Ê¤é¤Ð¥Í¥Ã¥È¥ï¡¼¥¯¤ò²ð¤·¤Æ Plainǧ¾Ú¤ò»È¤¦¤È´í¤Ê¤¤¤è¤È¤¤¤¦¤³¤È¤Ë¤Ê¤ë
courier-imap ¤Î¥¤¥ó¥¹¥È¡¼¥ë †
¥æ¡¼¥¶°¸¤ËÆϤ¤¤¿¥á¡¼¥ë¤ò MUA ¤ËÅϤ¹¤Î¤Ë¹¤¯»È¤ï¤ì¤Æ¤¤¤ë POP/IMAP ¤Î¥µ¡¼¥Ð¤Ë¤Ä¤¤¤Æ¤Ï¼¡²ó¤Ë¼ø¶È¤Ç°·¤¦¤¬¡¤¤½¤ÎÆâÉô¥Ä¡¼¥ë¤òº£»È¤¦É¬Íפ¬¤¢¤ë¤¿¤á¡¤¤³¤³¤Ç¥¤¥ó¥¹¥È¡¼¥ë¤·¤Æ¤·¤Þ¤ª¤¦¡¥
IMAP ¥µ¡¼¥Ð¤È¤·¤Æ courier-imap ¤¬¹¤¯»È¤ï¤ì¤Æ¤¤¤ë¤Î¤Ç¤³¤ì¤òÍѤ¤¤ë¡¥
¤Ê¤ª¡¤courier-imap ¤ò¥¤¥ó¥¹¥È¡¼¥ë¤¹¤ë¤È°ì½ï¤Ë courier-pop ¤â¥¤¥ó¥¹¥È¡¼¥ë¤µ¤ì¤ë¤Î¤Ç¡¤POP ¥µ¡¼¥Ð¤ò¥¤¥ó¥¹¥È¡¼¥ë¤·¤¿¤¤¡¤¤È¤¤¤¦¤È¤¤Ë courier-imap ¤òÁªÂò¤·¤Æ¤â¤è¤¤.
![]() ¤µ¤Æ¡¤¤¤¤Ä¤â¤Î¤è¤¦¤Ë ports ¥³¥ì¥¯¥·¥ç¥ó¤«¤é¥¤¥ó¥¹¥È¡¼¥ë¤·¤è¤¦.
¤µ¤Æ¡¤¤¤¤Ä¤â¤Î¤è¤¦¤Ë ports ¥³¥ì¥¯¥·¥ç¥ó¤«¤é¥¤¥ó¥¹¥È¡¼¥ë¤·¤è¤¦.
¤¿¤À¤·¡¤imap ¥µ¡¼¥Ð¤Î¥¤¥ó¥¹¥È¡¼¥ë¤ÎÁ°¤Ë courier-authlib(courier-imap ¤Îǧ¾Ú´Ø·¸¤À¤±È´¤½Ð¤·¤¿meta ports) ¤Î¥¤¥ó¥¹¥È¡¼¥ë¤ò¹Ô¤Ã¤Æ¤ª¤¯(¤½¤¦¤·¤Ê¤¤¤È¼Â¼ÁŪ¤Ë»È¤¨¤Ê¤¤).
¤¤¤Ä¤â¤Î¤è¤¦¤Ë
portsnap fetch; portsnap update
¤È¤·¤Æ¤«¤é¡¤psearch ¤Ç courier-authlib ¤òõ¤·¤Æ¤«¤é portinstall ¤ò»È¤Ã¤Æ¥¤¥ó¥¹¥È¡¼¥ë¤·¤è¤¦¡¥
¤Þ¤¢½ñ¤¤¤Æ¤·¤Þ¤¨¤Ð¡¤
portinstall security/courier-authlib
¤È¤¤¤¦¤³¤È¤À¡¥¤³¤Î²áÄø¤ÇɬÍפʾ¤Î¥Ä¡¼¥ë¤â°ì½ï¤Ë¥¤¥ó¥¹¥È¡¼¥ë¤µ¤ì¤ë¤Î¤Ç¡¤¤·¤Ð¤é¤¯ÂԤȤ¦.
¶ñÂÎŪ¤Ë¤Ï¡¤
- devel/sysconftool
- security/courier-authlib-base
- security/courier-authlib
¤¬¥¤¥ó¥¹¥È¡¼¥ë¤µ¤ì¤ë(¤³¤¦¤¤¤¦¾ðÊó¤Ï¸å¤Ç¥í¥°¤òµù¤ëºÝ¤ËɬÍפˤʤ뤳¤È¤¬¤¢¤ë¤Î¤Ç¡¤¼«Ê¬¤Çºî¶È¤¹¤ë¤È¤¤Ï¥á¥â¤·¤Æ¤ª¤³¤¦)
¤Þ¤¿ courier-authlib ¤Î¥¤¥ó¥¹¥È¡¼¥ë¤ÎÃʳ¬¤Ç½Ð¤ë¥ª¥×¥·¥ç¥ó²èÌÌ
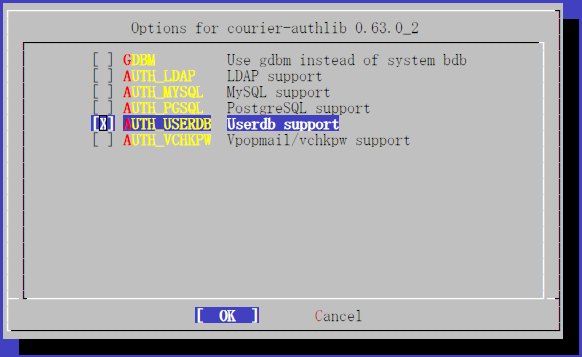
¤Ç¤Ï¤È¤ê¤¢¤¨¤º "Userdb support" ¤òÁª¤ó¤Ç¤ª¤³¤¦. ¤¢¤È¤Ï¥¹¥à¡¼¥º¤Ë¿Ê¤à¤À¤í¤¦.
¼¡¤Ë courier-imap ËÜÂΤò(psearch ¤Çõ¤·¤Æ¤«¤é)
portinstall mail/courier-imap
¤È¤·¤Æ courier-imap ËÜÂΤò¥¤¥ó¥¹¥È¡¼¥ë¤¹¤ë. ºÇ½é¤Ë¥ª¥×¥·¥ç¥óÁªÂò²èÌÌ
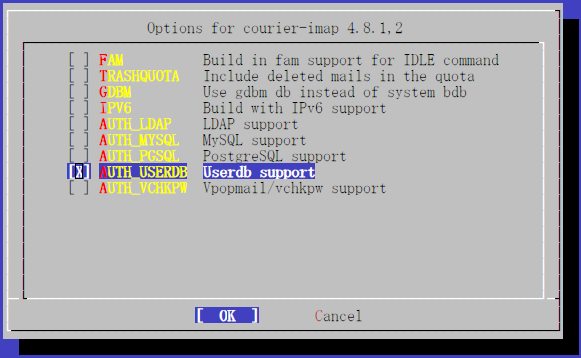
¤¬½Ð¤ë¤¬¡¤Â¿Ê¬¥Ç¥Õ¥©¥ë¥È¤Ç IPv6 ¤¬Áª¤Ð¤ì¤Æ¤¤¤ë¤À¤í¤¦.
IPv6 ¤Ï»È¤ï¤Ê¤¤¤Î¤Ç³°¤·¡¤µÕ¤ËÀè¤ÈƱÍÍ¤Ë "Userdb support" ¤òÁªÂò¤·¤ÆÀè¤Ë¿Ê¤â¤¦.
¤·¤Ð¤é¤¯ÂԤäƤ¤¤ë¤È¥¤¥ó¥¹¥È¡¼¥ë¤¬½ª¤ï¤ë¤À¤í¤¦.
¤µ¤Æ¡¤Ç°¤Î°Ù¤Ë¤¤¤Ä¤â¤Î¤è¤¦¤Ëº£²ó¥¤¥ó¥¹¥È¡¼¥ë¤µ¤ì¤¿Ê£¿ô¤Î¥½¥Õ¥È¤Î¥í¥°¤ò /var/log/ports ¤Î²¼¤«¤éõ¤·¤Æ¤ß¤Æ¡¤¥á¥Ã¥»¡¼¥¸¤òÈ´¤½Ð¤¹¤È¡¤
(devel::sysconftool ¤«¤é ¡Ä ÆäË̵¤·)
(security::courier-authlib-base.log ¤«¤é)
Set WITH_AUTHPIPE_PROG to a program you want to use instead of
authProg for libauthpipe
configure: WARNING: -----------------------------------------------------
configure: WARNING: expect not found - will not be able to change passwds
configure: WARNING: in webmail
configure: WARNING: -----------------------------------------------------
Added group "courier".
Added user "courier".
----------------------------------------------------------------------
Libraries have been installed in:
/usr/local/lib/courier-authlib
¡¡
If you ever happen to want to link against installed libraries
in a given directory, LIBDIR, you must either use libtool, and
specify the full pathname of the library, or use the `-LLIBDIR'
flag during linking and do at least one of the following:
- add LIBDIR to the `LD_LIBRARY_PATH' environment variable
during execution
- add LIBDIR to the `LD_RUN_PATH' environment variable
during linking
- use the `-Wl,-rpath -Wl,LIBDIR' linker flag
¡¡
See any operating system documentation about shared libraries for
more information, such as the ld(1) and ld.so(8) manual pages.
----------------------------------------------------------------------
===> SECURITY REPORT:
This port has installed the following files which may act as network
servers and may therefore pose a remote security risk to the system.
/usr/local/libexec/courier-authlib/authdaemond
¡¡
This port has installed the following startup scripts which may cause
these network services to be started at boot time.
/usr/local/etc/rc.d/courier-authdaemond
¡¡
If there are vulnerabilities in these programs there may be a security
risk to the system. FreeBSD makes no guarantee about the security of
ports included in the Ports Collection. Please type 'make deinstall'
to deinstall the port if this is a concern.
¡¡
For more information, and contact details about the security
status of this software, see the following webpage:
(security::courier-authlib.log ¤«¤é)
configure: WARNING: -----------------------------------------------------
configure: WARNING: expect not found - will not be able to change passwds
configure: WARNING: in webmail
configure: WARNING: -----------------------------------------------------
----------------------------------------------------------------------
Libraries have been installed in:
/usr/local/lib/courier-authlib
¡¡
If you ever happen to want to link against installed libraries
in a given directory, LIBDIR, you must either use libtool, and
specify the full pathname of the library, or use the `-LLIBDIR'
flag during linking and do at least one of the following:
- add LIBDIR to the `LD_LIBRARY_PATH' environment variable
during execution
- add LIBDIR to the `LD_RUN_PATH' environment variable
during linking
- use the `-Wl,-rpath -Wl,LIBDIR' linker flag
¡¡
See any operating system documentation about shared libraries for
more information, such as the ld(1) and ld.so(8) manual pages.
----------------------------------------------------------------------
(mail::courier-imap.log ¤«¤é)
In case you use authpam, you should put the following lines
in your /etc/pam.d/imap
auth required pam_unix.so try_first_pass
account required pam_unix.so try_first_pass
session required pam_permit.so
¡¡
You will have to run /usr/local/share/courier-imap/mkimapdcert to create
a self-signed certificate if you want to use imapd-ssl.
And you will have to copy and edit the *.dist files to *
in /usr/local/etc/courier-imap.
===> SECURITY REPORT:
This port has installed the following files which may act as network
servers and may therefore pose a remote security risk to the system.
/usr/local/libexec/courier-imap/couriertcpd
/usr/local/bin/couriertls
¡¡
This port has installed the following startup scripts which may cause
these network services to be started at boot time.
/usr/local/etc/rc.d/courier-imap-imapd
/usr/local/etc/rc.d/courier-imap-pop3d
/usr/local/etc/rc.d/courier-imap-pop3d-ssl
/usr/local/etc/rc.d/courier-imap-imapd-ssl
¡¡
If there are vulnerabilities in these programs there may be a security
risk to the system. FreeBSD makes no guarantee about the security of
ports included in the Ports Collection. Please type 'make deinstall'
to deinstall the port if this is a concern.
¡¡
For more information, and contact details about the security
status of this software, see the following webpage:
¤È¤¤¤¦¥á¥Ã¥»¡¼¥¸¤¬¸«¤Ä¤«¤ë.
courier-authlib ´ØÏ¢¤Î¥í¥°¥Õ¥¡¥¤¥ë¤ÎÆâÍƤÏÆäËÌäÂê¤Ê¤¤.
courier-imap ¤Î¥í¥°¥Õ¥¡¥¤¥ë¤Ë¤ÏÀßÄê¤Ë´Ø¤ï¤ëÉôʬ¤¬¤¢¤ë¤Î¤Ç½ÅÍפÀ(¾Ü¤·¤¯¤Ï¼¡²ó¸å½Ò¤¹¤ë).
![]() SMTP Auth ¤ÎÅÓÃ椫¤é courier-imap ¤Î¥¤¥ó¥¹¥È¡¼¥ë¤ØÈô¤Ù¡¤¤È¸À¤ï¤ì¤Æ¤³¤³¤ØÍè¤Æ¤¤¤ë¾ì¹ç¤Ï¡¤¸µ¤Î¤È¤³¤í¤ØÌá¤í¤¦.
SMTP Auth ¤ÎÅÓÃ椫¤é courier-imap ¤Î¥¤¥ó¥¹¥È¡¼¥ë¤ØÈô¤Ù¡¤¤È¸À¤ï¤ì¤Æ¤³¤³¤ØÍè¤Æ¤¤¤ë¾ì¹ç¤Ï¡¤¸µ¤Î¤È¤³¤í¤ØÌá¤í¤¦.
¥ì¥Ý¡¼¥È †
ÅÓÃæ¤Ç¡ÖÄ´¤Ù¤è¡×¤È»Ø¼¨¤µ¤ì¤¿»ö¹à¤Ë¤Ä¤¤¤ÆÄ´ºº¤ò¹Ô¤¤¡¤Êó¹ð¤»¤è.
¤â¤Á¤í¤ó³Æ¼«¤Î
- ½ê°(³ØÉô¡¤³Ø²Ê)
- ³ØÀÒÈÖ¹æ
- ³Øǯ
- »á̾
- Æü»þ
- ´Î¿´¤Î¥ì¥Ý¡¼¥ÈÆâÍÆ(ÆÀ¤¿Ãθ«¡¤ºî¶È¤Ë¤Ä¤¤¤Æµ¤¤Å¤¤¤¿¤³¤ÈÅù)
¤ò½ñ¤¯¤Î¤ò˺¤ì¤Ê¤¤¤è¤¦¤Ë.
about Icons, ClipArts †
Some icons in this page are downloadable at ICONFINDER.
The "note" icon ![]() designed by Marco Martin is distributed with the LGPL licence,
designed by Marco Martin is distributed with the LGPL licence,
the "warning" icon ![]() designed by Alexandre Moore with the GPL licence
designed by Alexandre Moore with the GPL licence
and the "triangle" icon ![]() designed by Joseph North is distributed with the Creative Commons (Attribution-Noncommercial-Share Alike 3.0 Unported) licence.
designed by Joseph North is distributed with the Creative Commons (Attribution-Noncommercial-Share Alike 3.0 Unported) licence.
Some clip arts used in this page are downloadable at Open Clip Art Library.
We deeply appreciate their superb works. With licence, they describe that "the actual clipart content on open clipart library is Public domain" in the web.
*1 \0 ¤Ï¥Ì¥ë¥Ð¥¤¥È
*2 ¤Á¤Ê¤ß¤Ë¡¤base64 ¥¨¥ó¥³¡¼¥É¤·¤¿¥Æ¥¥¹¥È¤Ï¡¤"mmencode -u" ¤Ç¸µ¤ËÌ᤹¤³¤È¤¬¤Ç¤¤ë.
*3 ʸ»úüËö¥¨¥ß¥å¥ì¡¼¥¿¤Ë³Ð¤¨¤µ¤»¤Æ¤·¤Þ¤¨¤Ð³Ú¤À¤í¤¦
*4 ¤³¤ì¤ò "mmencode -u" ¤Ë¤«¤±¤ë¤È¼ÂºÝ¤Îʸ»úÎ󤬤狼¤ë
źÉÕ¥Õ¥¡¥¤¥ë: