¼ø¶È»ñÎÁ/Âè09²ó
ǧ¾Ú¥·¥¹¥Æ¥à¤Ë¤Ä¤¤¤Æ°ìÈÌŪ¤ÊÏà †
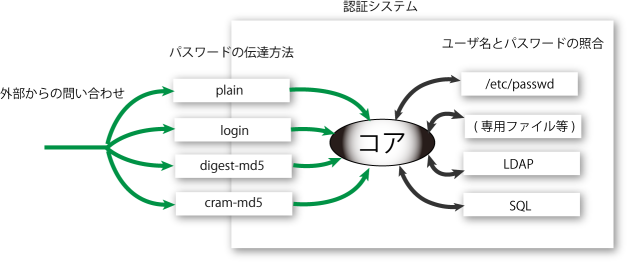
unix ¥µ¡¼¥Ð¤Ë¸Â¤é¤º¡¤¥³¥ó¥Ô¥å¡¼¥¿°ìÈ̤ˡÖǧ¾Ú¡×¤È¤¤¤¦»ÅÁȤߤÏÉԲķç¤Ç¤¢¤ë.
´ðËÜŪ¤Ë¡¤´í¸±¤ÊÎΰè¤Ç¤¢¤ë¥¤¥ó¥¿¡¼¥Í¥Ã¥È¾å¤ò¥Ñ¥¹¥ï¡¼¥É¤ò¤É¤Î¤è¤¦¤Ë¤ä¤ê¤È¤ê¤¹¤ë¤«¡¤¥Ñ¥¹¥ï¡¼¥É¤È¥æ¡¼¥¶Ì¾¤Ê¤É¤Î¾È¹ç¤ò¤É¤Î¤è¤¦¤Ë¹Ô¤¦¤Î¤«¤ÎÆóÅÀ¤Ë¤Ä¤¤¤ÆÍÍ¡¹¤ÊÊýË¡¤¬¤¢¤ê¡¤¤³¤ì¤é¤ò½ÀÆð¤ËÁª¤Ù¤ë¤è¤¦¤Ë¤Ê¤Ã¤Æ¤¤¤ë¤â¤Î¤¬Â¿¤¤.
¤½¤Î¤¿¤á¤Ë½é³Ø¼Ô¤Ë¤Ïº®Í𤬤¢¤ë¤«¤È»×¤¦¤¬¡¤¼ÂºÝ¤Ï¤³¤ÎÆ󥫽ê¤ÎÁªÂò¤À¤È¤¤¤¦¹½¿Þ¤¬Ê¬¤«¤ì¤Ðʬ¤«¤ê¤ä¤¹¤¤¤À¤í¤¦.
¼ÂºÝ¡¤¤ª¤ª¤Þ¤«¤Ë¤Ï¡¤unix ¾å¤Ç¤Î¥½¥Õ¥È¥¦¥§¥¢¤ÏÄ̾ï¤Ï°Ê²¼¤Î¿Þ¤Î¤è¤¦¤Ê¹½Â¤¤ò¤·¤Æ¤¤¤ë¤Î¤Ç¡¤¤³¤Î¹½¿Þ¤òƬ¤Ë¤¤¤ì¤Æ°Ê²¼¤ÎÏäòÆɤá¤Ð¤ï¤«¤ë¤À¤í¤¦.
SMTP Auth ¤ò»È¤¦ †
SMTP Auth ¤ÎÀßÄê(postfix, cyrus sasl2) †
¤è¤ê¼«Í³¤Ë MTA ¤ò»È¤¦¤¿¤á¤Ë SMTP Auth ¤òÍøÍѤ¹¤ë¤³¤È¤òÁÛÄꤷ¤è¤¦.
¤µ¤Æ¡¤¤Þ¤º¤Ï postfix ¤ò¥¤¥ó¥¹¥È¡¼¥ë¤·¤¿¤È¤¤Î¥í¥°¤Ë¤¢¤ë smtp auth ¤Ë´Ø¤¹¤ë¥á¥Ã¥»¡¼¥¸¤òºÆ¥Á¥§¥Ã¥¯¤À.
³ºÅöÉôʬ¤òºÆ·Ç¤¹¤ë¤È¡¤
You can use sasldb2 for authentication, to add users use:
saslpasswd2 -c username
If you want to enable SMTP AUTH with the system Sendmail, read
Sendmail.README
NOTE: This port has been compiled with a default pwcheck_method of
auxprop. If you want to authenticate your user by /etc/passwd,
PAM or LDAP, install ports/security/cyrus-sasl2-saslauthd and
set sasl_pwcheck_method to saslauthd after installing the
Cyrus-IMAPd 2.X port. You should also check the
/usr/local/lib/sasl2/*.conf files for the correct
pwcheck_method.
¤È¤Ê¤Ã¤Æ¤ª¤ê¡¤¤¿¤¤¤·¤¿¤³¤È¤Ï½ñ¤¤¤Æ¤¤¤Ê¤¤.
- smtp auth ¤ò¤Ä¤«¤¦¤Ê¤é¤Ð¡¤¥æ¡¼¥¶¥Ñ¥¹¥ï¡¼¥É¤ò saslpasswd2 ¥³¥Þ¥ó¥É¤ÇÄɲ令è
- ¤³¤Î port ¤Ï¥Ñ¥¹¥ï¡¼¥É¾È¹ç¤È¤·¤Æ pwcheck_method (ÀìÍÑ¥Õ¥¡¥¤¥ë¤Ë¤è¤ë¾È¹ç)µ¡Ç½¤òÄ󶡤¹¤ë¤¬¡¤Â¾¤Î¾È¹çÊýË¡¤ò»È¤¤¤¿¤±¤ì¤Ð¤½¤ì¤ËÂбþ¤¹¤ë port ¤â¥¤¥ó¥¹¥È¡¼¥ë¤»¤è¡Ä
¤È¤¤¤¦¤³¤È¤¬¤ï¤º¤«¤Ë¤ï¤«¤ë¤Î¤ß¤Ç¤¢¤ë*1.
¤µ¤Æ¡¤¤³¤ì¤À¤±¤Ç¤Ï¤É¤¦¤ä¤Ã¤Æ»È¤Ã¤Æ¤è¤¤¤«¤ï¤«¤é¤Ê¤¤¤Î¤Ç¡¤¾ðÊó¤ò¤¤Á¤ó¤ÈÄ´¤Ù¤è¤¦.
¤Þ¤º¤Ï°ì¼¡¾ðÊ󸻤Ȥ¤¤¦¤³¤È¤Ç¡¤ËÜ²È http://www.postfix.org/ ¤Ç³Îǧ¤·¤¿¤¤¡¥
Documentation ¤ò¸«¤ë¤È¡¤³ºÅö¤·¤½¤¦¤Ê¤â¤Î¤¬¤¹¤°¸«¤Ä¤«¤ë.
¶ñÂÎŪ¤Ë¤Ï http://www.postfix.org/SASL_README.html ¤ò¥Á¥§¥Ã¥¯¤¹¤ë¤³¤È¤Ë¤Ê¤ë.
¤¹¤ë¤È¡¤¤Þ¤º¤Ï¼¡¤Î¤è¤¦¤Ë½ñ¤¤¤Æ¤¢¤ë¤È¤³¤í¤¬»²¹Í¤Ë¤Ê¤ë.
Enabling SASL authentication in the Postfix SMTP server
In order to enable SASL support in the Postfix SMTP server:
/etc/postfix/main.cf:
smtpd_sasl_auth_enable = yes
In order to allow mail relaying by authenticated remote SMTP clients:
/etc/postfix/main.cf:
smtpd_recipient_restrictions =
permit_mynetworks
permit_sasl_authenticated
reject_unauth_destination
To report SASL login names in Received: message headers (Postfix version 2.3 and later):
/etc/postfix/main.cf:
smtpd_sasl_authenticated_header = yes
Note: the SASL login names will be shared with the entire world.
Older Microsoft SMTP client software implements a non-standard version of the AUTH protocol syntax, and expects that the SMTP server replies to EHLO with "250 AUTH=mechanism-list" instead of "250 AUTH mechanism-list". To accommodate such clients (in addition to conformant clients) use the following:
/etc/postfix/main.cf:
broken_sasl_auth_clients = yes
¤³¤ì¤òÆɤà¤È¡¤postfix ¤ÎÀßÄê¥Õ¥¡¥¤¥ë¤Ç¤¢¤ë main.cf ¤ò½ñ¤´¹¤¨¤ë¤À¤±¤Ç¤è¤¤¤è¤¦¤À¡¤¤È¤¤¤¦¤³¤È¤¬¤Þ¤º¤ï¤«¤ë.
Â礶¤Ã¤Ñ¤Ë¤Ï
- SASL ¤ò»È¤¤¤¿¤±¤ì¤Ð¡¤¤³¤¦¤·¤í.
- ǧ¾Ú¤µ¤ì¤¿¥ê¥â¡¼¥È¥¯¥é¥¤¥¢¥ó¥È¤Ë¤è¤ë¥á¡¼¥ë¥ê¥ì¡¼¤òµö²Ä¤·¤¿¤±¤ì¤Ð¡¤¤³¤¦¤·¤í.
- ¥á¡¼¥ë¤Î¤ä¤ê¤È¤ê¤Î¥Ø¥Ã¥À¤Ë SASL¥æ¡¼¥¶Ì¾¤òºÜ¤»¤¿¤±¤ì¤Ð¡¤¤³¤¦¤·¤í.
- Microsoft ¤Î¸Å¤¤¥á¡¼¥é¤Ë¤Ïǧ¾Ú¥×¥í¥È¥³¥ë¤Îʸˡ¤Î°ìÉô¤¬¤ª¤«¤·¤¤¤â¤Î¤¬¤¢¤ë¤¬¤³¤ì¤òµö¤·¤Æ¤ä¤ê¤¿¤±¤ì¤Ð¡¤¤³¤¦¤·¤í.
¤È¤¤¤¦4¤Ä¤Î¤³¤È¤¬½ñ¤¤¤Æ¤¢¤ë.
¤É¤ì¤âÆä˰ÛÏÀ¤Ï¤Ê¤¤ÆâÍƤʤΤǡ¤¤½¤Î¤Þ¤Þ½¾¤Ã¤Æ¤è¤¤¤À¤í¤¦.
![]()
¤È¤¤¤¦¤³¤È¤Ç¡¤¤³¤Î»Ø¼¨¤Ë¤·¤¿¤¬¤Ã¤Æ main.cf ¤ò½¤Àµ¤·¤è¤¦.
¤³¤³¤Ç¤ÏÁ´Éô¤Ç 4¤Ä¤Îµ½Ò¤¬²Ã¤ï¤ë¤³¤È¤Ë¤Ê¤ë. ¤³¤ì¤Ï main.cf ¤ÎºÇ¸å¤Ë¸Ç¤á¤Æµ½Ò¤·¤Æ¤âÌäÂê¤Ê¤¤¤Ï¤º¤À.
¤¿¤À¤·¡¤¾å¤ÎʸÃæ¤Î/etc/postfix ¤Ï FreeBSD ¤Ç¤Ï /usr/local/etc/postfix ¤ËÊѹ¹¤µ¤ì¤Æ¤¤¤ë¤Î¤ÇǾÆâ¤ÇÊÑ´¹¤·¤Ê¤¬¤éÆɤ⤦.
![]() "smtp" ¤È "smtpd" (ºÇ¸å¤Ë "d" ¤¬¤Ä¤¤¤Æ¤¤¤ë)¤È¤Ç¤Ï°ÕÌ£¤¬°ã¤Ã¤Æ¤¯¤ë¤Î¤Ç¡¤¥¿¥¤¥×¥ß¥¹¤ò¤·¤Æ¤¤¤Ê¤¤¤«Ãí°Õ¿¼¤¯µ½Ò¤·¤è¤¦.
"smtp" ¤È "smtpd" (ºÇ¸å¤Ë "d" ¤¬¤Ä¤¤¤Æ¤¤¤ë)¤È¤Ç¤Ï°ÕÌ£¤¬°ã¤Ã¤Æ¤¯¤ë¤Î¤Ç¡¤¥¿¥¤¥×¥ß¥¹¤ò¤·¤Æ¤¤¤Ê¤¤¤«Ãí°Õ¿¼¤¯µ½Ò¤·¤è¤¦.
¤µ¤é¤Ë¾åµ»ñÎÁ¤òÆɤ߿ʤà¤È¡¤ "Cyrus SASL configuration for the Postfix SMTP server" ¤Ç»Ï¤Þ¤ëÉôʬ¤â´Ø·¸¤·¤Æ¤¤¤ë¤Î¤ÇÆɤ⤦.
¤¿¤À¤·¡¤postfix (ver.2.5.5,1)¤ä cyrus sasl (ver. 2.1.22_2)¤Î¥Ð¡¼¥¸¥ç¥ó¤Ë¤è¤Ã¤Æ¾ì¹ç¤ï¤±¤¬¤µ¤ì¤Æ¤¤¤ë¤Î¤Ç¡¤´Ø·¸¤¹¤ëÉôʬ¤À¤±¤òÈ´¤½Ð¤·¤ÆŬµ¹È´¿è¤¹¤ë¤È°Ê²¼¤Î¤è¤¦¤Ë¤Ê¤ë.
¤Þ¤º¡¤
Cyrus SASL configuration for the Postfix SMTP server
You need to configure how the Cyrus SASL library should authenticate a remote SMTP client's username and password. These settings must be stored in a separate configuration file.
The name of the configuration file (default: smtpd.conf) will be constructed from a value that the Postfix SMTP server sends to the Cyrus SASL library, which adds the suffix .conf. The value is configured using one of the following variables:
/etc/postfix/main.cf:
smtpd_sasl_path = smtpd
Cyrus SASL searches for the configuration file in /usr/local/lib/sasl2/.
Note: some Postfix distributions are modified and look for the smtpd.conf file in /etc/postfix/sasl.
Note: some Cyrus SASL distributions look for the smtpd.conf file in /etc/sasl2.
¤È¤¤¤¦¤³¤È¤Ç¡¤cyrus sasl2 ¤ÎÀßÄê¥Õ¥¡¥¤¥ë¤Ï /usr/local/lib/sasl2/smtpd.conf ¤Ç¡¤¤Þ¤¿¡¤¤½¤ÎÀßÄê¥Õ¥¡¥¤¥ë¤ò͸ú¤Ë¤¹¤ë¤¿¤á¤Ë postfix ¤ÎÀßÄê¥Õ¥¡¥¤¥ë¤Ë1¹Ô½ñ¤¤³¤ó¤Ç¤ª¤¯É¬Íפ¬¤¢¤ê¤½¤¦¤À.
![]() ¤Þ¤º¤Ï¾å¤Î»Ø¼¨¤Ë½¾¤Ã¤Æ postfix ¤ÎÀßÄê¥Õ¥¡¥¤¥ë main.cf ¤Ë1¹Ô½ñ¤¤³¤â¤¦.
¤Þ¤º¤Ï¾å¤Î»Ø¼¨¤Ë½¾¤Ã¤Æ postfix ¤ÎÀßÄê¥Õ¥¡¥¤¥ë main.cf ¤Ë1¹Ô½ñ¤¤³¤â¤¦.
¤½¤ì¤«¤é¡¤¥Ñ¥¹¥ï¡¼¥É¾È¹çÊýË¡¤ÎÁªÂò¤Ë¤Ä¤¤¤Æ¤¬¼¡¤Ë³¤¤¤Æ½ñ¤«¤ì¤Æ¤¤¤ë.
* To authenticate against the UNIX password database, use: ¢« ¥í¥°¥¤¥ó¥Ñ¥¹¥ï¡¼¥É¤òǧ¾Ú¤Ë»È¤¦¾ì¹ç. º£²ó¤Ï°ã¤¦¤Î¤Çά.
* To authenticate against Cyrus SASL's own password database: ¢« ÀìÍÑ¥Õ¥¡¥¤¥ë¤ò»È¤¦¾ì¹ç. º£²ó¤Ï¤³¤ì¤ò»È¤ª¤¦.
/usr/local/lib/sasl2/smtpd.conf:
pwcheck_method: auxprop
auxprop_plugin: sasldb
mech_list: PLAIN LOGIN CRAM-MD5 DIGEST-MD5
![]() ¤È¤¢¤ë¤Î¤Ç¡¤¾å¤Î¤è¤¦¤Ë smptd.conf ¤òÊÔ½¸¤·¤è¤¦(¤¿¤Ö¤ó¿·µ¬ºîÀ®¤¹¤ë¤³¤È¤Ë¤Ê¤ë).
¤È¤¢¤ë¤Î¤Ç¡¤¾å¤Î¤è¤¦¤Ë smptd.conf ¤òÊÔ½¸¤·¤è¤¦(¤¿¤Ö¤ó¿·µ¬ºîÀ®¤¹¤ë¤³¤È¤Ë¤Ê¤ë).
![]() mech_list ¤ò½ü¤¤¤Æ¼Â¤Ï¤³¤ì¤Ï¥Ç¥Õ¥©¥ë¥È¤Î¤è¤¦¤Ê¤Î¤Ç¡¤smtpd.conf ̵¤·¤Ç¤â°ì±þ¤³¤ì¤«¤é¤Îºî¶È¤Ï²Äǽ¤À¤¬¡¤¤ä¤Ï¤ê¤¤Á¤ó¤Èºî¤Ã¤Æ¤ª¤³¤¦.
mech_list ¤ò½ü¤¤¤Æ¼Â¤Ï¤³¤ì¤Ï¥Ç¥Õ¥©¥ë¥È¤Î¤è¤¦¤Ê¤Î¤Ç¡¤smtpd.conf ̵¤·¤Ç¤â°ì±þ¤³¤ì¤«¤é¤Îºî¶È¤Ï²Äǽ¤À¤¬¡¤¤ä¤Ï¤ê¤¤Á¤ó¤Èºî¤Ã¤Æ¤ª¤³¤¦.
¤½¤ì¤«¤é³¤±¤Æ¡¤
This will use the Cyrus SASL password file (default: /etc/sasldb2), which is maintained with the saslpasswd or saslpasswd2 command (part of the Cyrus SASL software). On some poorly-supported systems the saslpasswd command needs to be run multiple times before it stops complaining. The Postfix SMTP server needs read access to the sasldb file - you may have to play games with group access permissions. With the OTP authentication mechanism, the Postfix SMTP server also needs WRITE access to /etc/sasldb2 or /etc/sasldb (or the back end SQL database, if used).
IMPORTANT: To get sasldb running, make sure that you set the SASL domain (realm) to a fully qualified domain name.
EXAMPLE:
% saslpasswd2 -c -u `postconf -h myhostname` exampleuser
You can find out SASL's idea about the realms of the users in sasldb with sasldblistusers2.
¤È¤¢¤ê¡¤¥æ¡¼¥¶¤Î¥Ñ¥¹¥ï¡¼¥É¤òÅÐÏ¿¤¹¤ëºÝ¤Ë realm(¥Ñ¥¹¥ï¡¼¥É¤Îǧ¾Ú͸ú¾õ¶·Îΰè¤È¤Ç¤â¤¤¤¦¤«)¤ò¤¤Á¤ó¤È¤³¤¦¤ä¤Ã¤Æ»ØÄꤷ¤í¡¤¤È¤¤¤¦Ïäʤɤ¬¤¢¤ë.
![]() ¾å¤Î»Ø¼¨¤Ë½¾¤¤¤Ä¤Ä¡¤smtp auth ÍѤΥ桼¥¶¥Ñ¥¹¥ï¡¼¥ÉÅÐÏ¿¤ò¤·¤è¤¦(ºÇ¸å¤Î "exampleuser" ¤È¤¤¤¦¤Î¤Ï¥æ¡¼¥¶Ì¾¤ËÃÖ¤´¹¤¨¤Æ).
¾å¤Î»Ø¼¨¤Ë½¾¤¤¤Ä¤Ä¡¤smtp auth ÍѤΥ桼¥¶¥Ñ¥¹¥ï¡¼¥ÉÅÐÏ¿¤ò¤·¤è¤¦(ºÇ¸å¤Î "exampleuser" ¤È¤¤¤¦¤Î¤Ï¥æ¡¼¥¶Ì¾¤ËÃÖ¤´¹¤¨¤Æ).
![]() ¤¤Á¤ó¤ÈÅÐÏ¿¤µ¤ì¤¿¤«¡¤sasldblistusers2 ¤È¤¤¤¦¥³¥Þ¥ó¥É¤Ç³Îǧ¤·¤è¤¦.
¤¤Á¤ó¤ÈÅÐÏ¿¤µ¤ì¤¿¤«¡¤sasldblistusers2 ¤È¤¤¤¦¥³¥Þ¥ó¥É¤Ç³Îǧ¤·¤è¤¦.
ÅÐÏ¿¤·¤¿¥æ¡¼¥¶Ì¾@¥Û¥¹¥È̾ userPassword
¤È¤¤¤¦½ÐÎϤ¬½Ð¤ì¤Ð¡¤ÅÐÏ¿¤µ¤ì¤Æ¤¤¤ë¤³¤È¤¬³Îǧ¤Ç¤¤¿¤È¤¤¤¦¤³¤È¤Ë¤Ê¤ë.
¼¡¤Ë¡¤
On the Postfix side, you can have only one realm per smtpd(8) instance, and only the users belonging to that realm would be able to authenticate. The Postfix variable smtpd_sasl_local_domain controls the realm used by smtpd(8):
/etc/postfix/main.cf:
smtpd_sasl_local_domain = $myhostname
¤È¤¢¤ë¤Î¤Ç¡¤realm ¤Ë´Ø¤¹¤ë postfix ¤ÎÀßÄê¤â¤Þ¤¿É¬ÍפÀ.
![]() ¾å¤Î»Ø¼¨¤Ë½¾¤Ã¤Æ postfix ¤ÎÀßÄê¥Õ¥¡¥¤¥ë main.cf ¤Ë1¹Ô½ñ¤¤³¤â¤¦.
¾å¤Î»Ø¼¨¤Ë½¾¤Ã¤Æ postfix ¤ÎÀßÄê¥Õ¥¡¥¤¥ë main.cf ¤Ë1¹Ô½ñ¤¤³¤â¤¦.
¤¢¤È¤Ï¡¤¼¡¤Î¤è¤¦¤ÊÃí°Õ¤¬¤¢¤ë.
IMPORTANT: The Cyrus SASL password verification services pwcheck and saslauthd can only support the plaintext mechanisms PLAIN or LOGIN. However, the Cyrus SASL library doesn't know this, and will happily advertise other authentication mechanisms that the SASL library implements, such as DIGEST-MD5. As a result, if a remote SMTP client chooses any mechanism other than PLAIN or LOGIN while pwcheck or saslauthd are used, authentication will fail. Thus you may need to limit the list of mechanisms advertised by the Postfix SMTP server.
* With Cyrus SASL version 2.1.x or later the mech_list variable can specify a list of authentication mechanisms that Cyrus SASL may offer:
/usr/local/lib/sasl2/smtpd.conf:
mech_list: plain login
For the same reasons you might want to limit the list of plugins used for authentication.
/usr/local/lib/sasl2/smtpd.conf:
pwcheck_method: auxprop
auxprop_plugin: sql
¤³¤ì¤Ï¥Ñ¥¹¥ï¡¼¥É¤ÎÅÁãÊýË¡¤È¾È¹çÊýË¡¤È¤ÎÁȤ߹ç¤ï¤»¤Î¤¦¤Á¡¤»È¤¨¤Ê¤¤¤â¤Î¤¬¤¢¤ë¤Î¤Ç¤½¤ì¤Ç¥È¥é¥Ö¤é¤Ê¤¤¤è¤¦¤Ë»È¤ï¤Ê¤¤ÁȤ߹ç¤ï¤»¤òÀßÄê¥Õ¥¡¥¤¥ë¤Ç¤¤Á¤ó¤È³°¤·¤Æ¤ª¤±¡¤»÷¤¿¤è¤¦¤Ê¤³¤È¤ò¤·¤¿¤±¤ì¤Ð¤³¤¦¤·¤í¡¤¤È¤¤¤¦ÆâÍƤÀ. º£²ó¤ÏÆä˴ط¸¤Ê¤¤.
¤½¤·¤ÆºÇ¸å¤Ë
To run software chrooted with SASL support is an interesting exercise. It probably is not worth the trouble.
¤È¤¢¤ë. ¤Þ¤¢¸À¤Ã¤Æ¤¤¤ë¤È¤ª¤ê¡¤¤¿¤Ö¤ó³ä¤Ë¤¢¤ï¤Ê¤¤¤À¤í¤¦¤«¤éº£²ó¤Ï´Ø·¸¤Ê¤·¤È¤·¤Æ¤ª¤³¤¦.
![]() FreeBSD ¤Ë¤Ï chroot ¤è¤ê¤â¿Ê²½¤·¤¿µ¡Ç½¤Ç¤¢¤ë jail ¤¬¤¢¤ë. chroot, jail ¤Ë¤Ä¤¤¤ÆÃΤé¤Ê¤¤¿Í¤ÏÄ´¤Ù¤Æ¤ª¤¯¤È¤è¤¤¤À¤í¤¦.
FreeBSD ¤Ë¤Ï chroot ¤è¤ê¤â¿Ê²½¤·¤¿µ¡Ç½¤Ç¤¢¤ë jail ¤¬¤¢¤ë. chroot, jail ¤Ë¤Ä¤¤¤ÆÃΤé¤Ê¤¤¿Í¤ÏÄ´¤Ù¤Æ¤ª¤¯¤È¤è¤¤¤À¤í¤¦.
SMTP Auth ¤ÎÆ°ºî³Îǧ †
½àÈ÷ †
¸å¤ÇÍѤ¤¤ë¥³¥Þ¥ó¥É mmencode ¤ò¡¤º£¤Î¤¦¤Á¤Ë¥¤¥ó¥¹¥È¡¼¥ë¤·¤Æ¤ª¤³¤¦.
¶ñÂÎŪ¤Ë¤Ï¡¤¤¤¤Ä¤â¤Î¤è¤¦¤Ë ports ¥³¥ì¥¯¥·¥ç¥ó¤ò¿·¤·¤¯¤·¤Æ¤ª¤¤¤Æ¤«¤é¡¤portinstall
¤¹¤ë¤È¤¤¤¦¼ê½ç¤Ê¤Î¤Ç¡¤
portsnap fetch portsnap update portinstall mmencode
¤È¤¹¤ì¤Ð¤è¤¤.
¼ÂºÝ¤Ë¼ê¤ÇÀܳ¤·¤Æ¤ß¤ë. †
SMTP Auth ¤ÇÀܳ¤¹¤ëºÝ¤Îǧ¾ÚÊýË¡¤Ë¤â¤¤¤¯¤Ä¤«¤¢¤ê¡¤¼«Í³¤ËÀßÄê¤ÇÁª¤Ö¤³¤È¤¬¤Ç¤¤ë.
º£²ó¤Î¥¤¥ó¥¹¥È¡¼¥ë¤Ç¤Ï¾å¤ÇÀßÄꤷ¤¿¤è¤¦¤Ë loginǧ¾Ú, plainǧ¾Ú¡¤Digest-MD5ǧ¾Ú, CRAM-MD5ǧ¾Ú ¤¬»È¤¨¤ë¤è¤¦¤Ë¤Ê¤Ã¤Æ¤¤¤ë¤Ï¤º¤À.
(¥Ç¥Õ¥©¥ë¥È¤Ç¤Ï¤µ¤é¤Ë NTLMǧ¾Ú¤È GSSAPIǧ¾Ú¤¬»È¤¨¤ë¤è¤¦¤Ë¤Ê¤ë¤è¤¦¤À)
¤½¤³¤Ç¡¤¤³¤Î¤¦¤Á¤Î plainǧ¾Ú¤È CRAM-MD5ǧ¾Ú¤ò»î¤·¤Æ¤ß¤è¤¦.
¤Á¤Ê¤ß¤Ë¡¤plainǧ¾Ú¤Ï´Êñ¤ËÍøÍѤǤ¤ë¤¬°Å¹æ²½¤µ¤ì¤Æ¤¤¤Ê¤¤¤â¤Î¤Ç¡¤CRAM-MD5ǧ¾Ú¤Ï¤½¤ÎµÕ¤È»×¤¨¤Ð¤è¤¤.
¼ê¤Ç SMTP Auth ¤ò»î¤¹ : Plain ǧ¾Ú¤Î¾ì¹ç †
Plain ǧ¾Ú¤Ï¤ªµ¤³Ú¤Ê¥â¥Î¤Ç¡¤SMTP Auth »þ¤Ëʸ»úÎó "\0¥æ¡¼¥¶Ì¾\0¥Ñ¥¹¥ï¡¼¥É"*2¤ò base64 ¤Ç¥¨¥ó¥³¡¼¥É¤·¤¿¤â¤Î¤ò¥µ¡¼¥Ð¤ËÅϤ¹¤È¤¤¤¦´Êñ¤Ê»ÅÁȤߤÀ.
![]() base 64 ¤Ï°Å¹æ²½¤Ç¤Ï¤Ê¤¯¤Æ(¥³¥ó¥Ô¥å¡¼¥¿¤Ç°·¤¦¤Î¤ËÊØÍø¤Ë¤Ê¤ë¤è¤¦¤Ê)ñ¤Ê¤ëÊÑ´¹*3¤Ê¤Î¤Ç¡¤¥»¥¥å¥ê¥Æ¥£¤ÏÁ´¤¯³ÎÊݤµ¤ì¤Ê¤¤. ¤Ä¤Þ¤ê¡¤¥Ñ¥¹¥ï¡¼¥ÉÅù¤ò base64 ¥¨¥ó¥³¡¼¥É¤·¤¿¤â¤Î(¸å½Ò¤Î mmencode ¤ò¤«¤±¤¿¤â¤Î)¤ò¿Í¤Ë¶µ¤¨¤¿¤ê¤·¤Æ¤Ï¤¤¤±¤Ê¤¤.
base 64 ¤Ï°Å¹æ²½¤Ç¤Ï¤Ê¤¯¤Æ(¥³¥ó¥Ô¥å¡¼¥¿¤Ç°·¤¦¤Î¤ËÊØÍø¤Ë¤Ê¤ë¤è¤¦¤Ê)ñ¤Ê¤ëÊÑ´¹*3¤Ê¤Î¤Ç¡¤¥»¥¥å¥ê¥Æ¥£¤ÏÁ´¤¯³ÎÊݤµ¤ì¤Ê¤¤. ¤Ä¤Þ¤ê¡¤¥Ñ¥¹¥ï¡¼¥ÉÅù¤ò base64 ¥¨¥ó¥³¡¼¥É¤·¤¿¤â¤Î(¸å½Ò¤Î mmencode ¤ò¤«¤±¤¿¤â¤Î)¤ò¿Í¤Ë¶µ¤¨¤¿¤ê¤·¤Æ¤Ï¤¤¤±¤Ê¤¤.
![]()
¤µ¤Æ¡¤ÀܳÁ°¤ËÀܳ¤ËɬÍפÊʸ»úÎó¤òºî¤Ã¤Æ¤·¤Þ¤ª¤¦.
¶ñÂÎŪ¤Ë¤Ï¡¤¥³¥Þ¥ó¥É¥é¥¤¥ó¤Ç
printf '\0000¥æ¡¼¥¶Ì¾\0000¥Ñ¥¹¥ï¡¼¥É' | mmencode
¤È¤¹¤ì¤Ð¤è¤¤*4.
¥æ¡¼¥¶Ì¾¤È¥Ñ¥¹¥ï¡¼¥É¤Ï¤µ¤¤Û¤É SMTP Auth ÍÑ¤Ë saslpasswd2 ¥³¥Þ¥ó¥É¤ÇÀßÄꤷ¤¿¤â¤Î¤Ç¤¢¤ë.
¤³¤¦¤¹¤ë¤È¡¤'\0¥æ¡¼¥¶Ì¾\0¥Ñ¥¹¥ï¡¼¥É' ¤¬ base64 ¥¨¥ó¥³¡¼¥É¤µ¤ì¤¿Ê¸»úÎ󤬽ÐÎϤµ¤ì¤ë¤Î¤Ç¡¤¤³¤ì¤ò¤É¤³¤«¤ØÊݸ¤·¤Æ¤ª¤³¤¦*5.
¤Á¤Ê¤ß¤Ë¡¤Î㤨¤Ð '\0test\0password' ¤ò mmencode ¤¹¤ë¤È "AHRlc3QAcGFzc3dvcmQ=" ¤È¤Ê¤ë.
![]() ¤¢¤È¤Ï¤¤¤Ä¤â¤Î¤è¤¦¤Ë telnet localhost 25 ¤Ç¼«Á°¤Î MTA ¤ËÀܳ¤·¤Æ¤ß¤ë.
¤¢¤È¤Ï¤¤¤Ä¤â¤Î¤è¤¦¤Ë telnet localhost 25 ¤Ç¼«Á°¤Î MTA ¤ËÀܳ¤·¤Æ¤ß¤ë.
Á°¤Ë¤â¤ä¤Ã¤¿¤è¤¦¤Ë "EHLO localhost" ¤È¤·¤Æ±þÅú¤ò¿Ê¤á¤ë¤È¡¤¼¡¤Î¤è¤¦¤Ë SMTP AUTH ¤¬¤Ç¤¤ë¤è¤È¤¤¤¦É½¼¨¹þ¤ß¤Ç±þÅú¤¬¿Ê¤à¤Ï¤º¤À(250-AUTH ¤Ç»Ï¤Þ¤ë¤Û¤ÜƱ¤¸¹Ô¤¬Æó²ó½Ð¤Æ¤¯¤ë¤Î¤¬ Microsoft ¤Î MUA Âкö¤Ç¤¢¤ë).
250-¥Û¥¹¥È̾
250-PIPELINING
250-SIZE 10240000
250-VRFY
250-ETRN
250-AUTH LOGIN PLAIN DIGEST-MD5 CRAM-MD5
250-AUTH=LOGIN PLAIN DIGEST-MD5 CRAM-MD5
250-ENHANCEDSTATUSCODES
250-8BITMIME
250 DSN
¤³¤ÎÃʳ¬¤Ç SMTP Auth ¤Î Plain ǧ¾Ú¤ò»î¤·¤Æ¤ß¤è¤¦.
¶ñÂÎŪ¤Ë¤Ï¡¤¤³¤³¤Ç
AUTH PLAIN Àè¤Û¤Ébase64¥¨¥ó¥³¡¼¥É¤·¤Æºî¤Ã¤¿Ê¸»úÎó
¤ÈÆþÎϤ¹¤ì¤Ð¤è¤¤. Plain ǧ¾Ú¤Ï¤³¤ì¤À¤±¤ÇºÑ¤à.
¤½¤·¤Æ
235 2.7.0 Authentication successful
¤Ê¤É¤È "success" ¤Î°Õ¤¬¥á¥Ã¥»¡¼¥¸¤ÇÊ֤äƤ¯¤ì¤Ð¡¤Ç§¾Ú¤¬Ä̤俤Ȥ¤¤¦¤³¤È¤Ç OK ¤Ç¤¢¤ë.
¤¢¤È¤ÏÁ°¤ÈƱÍÍ¤Ë ^], quit ¤ÇÈ´¤±¤è¤¦.
¤¦¤Þ¤¯¤¤¤«¤Ê¤¤¿Í¤ÏÃúÇ«¤Ë¤³¤ì¤Þ¤Ç¤Îºî¶È¤ò¿¶¤êÊÖ¤í¤¦.
¼ê¤Ç SMTP Auth ¤ò»î¤¹ : CRAM-MD5 ǧ¾Ú¤Î¾ì¹ç †
CRAM-MD5ǧ¾Ú¤ÏÀè¤Î Plainǧ¾Ú¤È°ã¤Ã¤Æ¡¤¥Ñ¥¹¥ï¡¼¥É¤òʿʸ¤ÇÁ÷¤é¤Ê¤¤·Á¼°¤Ç¤¢¤ë. plain ǧ¾Ú¤È°Û¤Ê¤ê¡¤¥Í¥Ã¥È¥ï¡¼¥¯¤òÅðÄ°¤µ¤ì¤Æ¤â¤Þ¤¢°ÂÁ´¤È¤¤¤¨¤è¤¦.
¶ñÂÎŪ¤Ë¤Ï¡¤Àܳ¤¹¤ë¤È¥µ¡¼¥Ð¤¬Å¬Åö¤Êʸ»úÎó¤òÁ÷¤Ã¤Æ¤¯¤ë¤Î¤Ç¡¤¤³¤ì¤ò¥Ñ¥¹¥ï¡¼¥É¤ò¥¡¼¤Ë¤·¤Æ hmac-md5 ¤Ç¥Ï¥Ã¥·¥å¤òµá¤á(¤³¤ì¤¬¥Ñ¥¹¥ï¡¼¥É¤ò°µ½Ì, °Å¹æ²½¤·¤¿¤³¤È¤ËÁêÅö¤¹¤ë), ¥æ¡¼¥¶Ì¾¤È¤¢¤ï¤»¤Æ base64 ¥¨¥ó¥³¡¼¥É¤·¤ÆÁ÷¤êÊÖ¤·¡¤¥µ¡¼¥Ð¤ÇƱÍͤ˺î¤Ã¤¿¥Ï¥Ã¥·¥å¤ÈƱ¤¸¤Ê¤éǧ¾Ú OK ¤È¤¤¤¦´¶¤¸¤Ë¤Ê¤ë.
¤ä¤ä¤³¤·¤¤¤¬¡¤¼Â¤Ï CRAM-MD5 ¤ò¥Æ¥¹¥È¤¹¤ë¤¿¤á¤Î¥¹¥¯¥ê¥×¥È "userdb-test-cram-md5" ¤¬Â¸ºß¤¹¤ë¤Î¤Ç¡¤¤³¤ì¤ò¥¤¥ó¥¹¥È¡¼¥ë¤·¤ÆÍѤ¤¤ì¤Ð¤è¤¤.
¤¿¤À¤·¡¤¤³¤Î¥¹¥¯¥ê¥×¥È¤Ï¸å½Ò¤Î courier-imap ¤Î¥¤¥ó¥¹¥È¡¼¥ë¤Ë¤è¤Ã¤Æ¥¤¥ó¥¹¥È¡¼¥ë¤µ¤ì¤ë¤Î¤Ç¡¤¤½¤Îºî¶È¤ò¤·¤Æ¤«¤éÌá¤Ã¤Æ¤³¤Ê¤¤¤È¤¤¤±¤Ê¤¤.
![]() ¤È¤¤¤¦¤ï¤±¤Ç¡¤½é¤á¤Æ¤³¤³¤òÆɤà¾ì¹ç¤Ï¡¤¸å½Ò¤Î courier-imap ¤Î¥¤¥ó¥¹¥È¡¼¥ë¤Þ¤Ç¥¸¥ã¥ó¥×¤·¡¤¥¤¥ó¥¹¥È¡¼¥ë¤·¤¿¸å¤ËÌá¤Ã¤Æ¤¯¤ë¤³¤È. ¤¿¤À¤·¡¤courier-imap ¤ÎÀßÄê¤Ï¤·¤Ê¤¤¤ÇÌá¤Ã¤Æ¤¤Æ¤è¤¤.
¤È¤¤¤¦¤ï¤±¤Ç¡¤½é¤á¤Æ¤³¤³¤òÆɤà¾ì¹ç¤Ï¡¤¸å½Ò¤Î courier-imap ¤Î¥¤¥ó¥¹¥È¡¼¥ë¤Þ¤Ç¥¸¥ã¥ó¥×¤·¡¤¥¤¥ó¥¹¥È¡¼¥ë¤·¤¿¸å¤ËÌá¤Ã¤Æ¤¯¤ë¤³¤È. ¤¿¤À¤·¡¤courier-imap ¤ÎÀßÄê¤Ï¤·¤Ê¤¤¤ÇÌá¤Ã¤Æ¤¤Æ¤è¤¤.
°Ê²¼¤Îºî¶È¤Ë¤Ï¥³¥ó¥½¡¼¥ë¤¬Æó¤Ä°Ê¾å¤¢¤Ã¤¿Êý¤¬ÊØÍø¤Ê¤Î¤Ç¡¤X ¤ÇŬÅö¤Êʸ»úüËö¥¨¥ß¥å¥ì¡¼¥¿¤òÆó¤Äµ¯Æ°¤¹¤ë¤Ê¤É¡¤¹©Éפ·¤Æºî¶È¤·¤è¤¦.
¥³¥ó¥½¡¼¥ë¤¬1¤Ä¤·¤«ÍѰդǤ¤Ê¤¤¾ì¹ç¤Ç¤â¡¤¥Þ¥¦¥¹Áàºî¤Ç¥³¥Ô¡¼(º¸¥¯¥ê¥Ã¥¯¤ÇÁªÂò) and ¥Ú¡¼¥¹¥È(¿¿¤óÃ楯¥ê¥Ã¥¯)¤¬²Äǽ¤Ê¾ì¹ç¤¬Â¿¤¤¤Î¤Ç¡¤¥Þ¥¦¥¹Áàºî¤ò»î¤ß¤Æ¤ß¤ë¤È¤è¤¤.
°Ê¹ß¡¤¾õ¶·¤òʬ¤«¤ê¤ä¤¹¤¯¤¹¤ë¤¿¤á¤Ë 2¤Ä¤Îʸ»úüËö¥¨¥ß¥å¥ì¡¼¥¿¤òÍÑ°Õ¤·¤¿¾õ¶·¤òÁÛÄꤷ¡¤¤½¤Î³Æ¡¹¤ÎüËö¾å¤ÇÆ°¤¯¥·¥§¥ë¤ò³Æ¡¹ Shell-A, Shell-B ¤È¤·¤ÆÏäò¿Ê¤á¤è¤¦.
![]() ¤Þ¤º¡¤Shell-A ¤Ç telnet localhost 25 ¤·¤Æ¡¤EHLO localhost ¤ÈÂбþ¤·¤ÆÀè¤ÈƱ¤¸¤è¤¦¤Ë
¤Þ¤º¡¤Shell-A ¤Ç telnet localhost 25 ¤·¤Æ¡¤EHLO localhost ¤ÈÂбþ¤·¤ÆÀè¤ÈƱ¤¸¤è¤¦¤Ë
250-¥Û¥¹¥È̾
250-PIPELINING
250-SIZE 10240000
250-VRFY
250-ETRN
250-AUTH LOGIN PLAIN DIGEST-MD5 CRAM-MD5
250-AUTH=LOGIN PLAIN DIGEST-MD5 CRAM-MD5
250-ENHANCEDSTATUSCODES
250-8BITMIME
250 DSN
¤Þ¤Ç¤¹¤¹¤á¤è¤¦. ¤½¤·¤Æ¤³¤³¤Ç
auth cram-md5
¤ÈÆþÎϤ¹¤ë. ¤¹¤ë¤È¡¤
334 PG5hbmlrYW5vLXNlcnZlcj4=
¤Ê¤É¤È½ÐÎϤ¬Ê֤äƤ¯¤ë.
¤³¤Î PG5hbmlrYW5vLXNlcnZlcj4= ¤¬¥µ¡¼¥Ð¤¬ base64 ¤ÇÁ÷¤Ã¤Æ¤¤¿Ê¸»úÎó*6¤Ç¤¢¤ë¤Î¤Ç¡¤¤³¤ì¤ò¥æ¡¼¥¶¤Î¥Ñ¥¹¥ï¡¼¥É¤ò¥¡¼¤Ë¤·¤Æ hmac-md5 ¤Ç¥Ï¥Ã¥·¥å¤ò·×»»¤·¤Æ¥æ¡¼¥¶Ì¾¤È¤¢¤ï¤»¤Æ base64 ¤ÇÁ÷¤êÊÖ¤»¤Ð¤è¤¤. ¤³¤Îʸ»úÎó¤ÎÀ¸À®¤ÏÌÌÅݤˤߤ¨¤ë¤¬¡¤¤Ê¤ó¤Î¤³¤È¤Ï¤Ê¤¯¤ÆÀè¤Î¥³¥Þ¥ó¥É¤ò»È¤¨¤Ð¤è¤¤.
¶ñÂÎŪ¤Ë¤Ï Shell-B ¤Ç userdb-test-cram-md5 ¤ò¼Â¹Ô¤·¤Æ¡¤°Ê²¼¤Î¤è¤¦¤ËÂбþ¤¹¤ì¤Ð¤è¤¤.
Username? testuser ¢« (SMTP Auth ¤Ë»È¤¦)¥æ¡¼¥¶Ì¾¤òÆþÎϤ¹¤ë
Password? password ¢« (SMTP Auth ¤Ë»È¤¦)¥Ñ¥¹¥ï¡¼¥É¤òÆþÎϤ¹¤ë
Send: AUTH CRAM-MD5 (or for imap, A AUTHENTICATE CRAM-MD5)
Paste the challenge here:
+ PG5hbmlrYW5vLXNlcnZlcj4= ¢« Shell-A ¤Ç¥µ¡¼¥Ð¤¬Á÷¤Ã¤Æ¤¤¿Ê¸»úÎó¤òÆþÎϤ¹¤ë
Send this response:
dGVzdHVzZXIgY2NiNjc4YmZjZGY1YWRlMGUyYmE2MmM3ODA3OTA1NGI= ¢« ÊÖ¤¹¤Ù¤Ê¸»úÎ󤬽ÐÎϤµ¤ì¤ë
¤È¤Ê¤ê¡¤ºÇ¸å¤ËÊÖÅú¤¹¤Ù¤Ê¸»úÎó¤òÀ¸À®¤·¤Æ¤¯¤ì¤ë.
¤½¤³¤Ç¤³¤Îʸ»úÎó(¤³¤ÎÎã¤Î¾ì¹ç¤Ï dGVzdHVzZXIgY2NiNjc4YmZjZGY1YWRlMGUyYmE2MmM3ODA3OTA1NGI=)¤ò¤µ¤Ã¤¤Î Shell-A ¤Ç¤Îºî¶È¤Î³¤¤Ë ÆþÎϤ¹¤ë.
ǧ¾Ú¤¬Ä̤ì¤Ð¤³¤Î¤¢¤È
235 2.7.0 Authentication successful
¤Ê¤É¤È "success" ¤Î°Õ¤¬¥á¥Ã¥»¡¼¥¸¤ÇÊ֤äƤ¯¤ì¤Ð¡¤Ç§¾Ú¤¬Ä̤俤Ȥ¤¤¦¤³¤È¤Ç OK ¤Ç¤¢¤ë.
¤¢¤È¤ÏÁ°¤ÈƱÍÍ¤Ë ^], quit ¤ÇÈ´¤±¤è¤¦.
¤¦¤Þ¤¯¤¤¤«¤Ê¤¤¿Í¤ÏÃúÇ«¤Ë¤³¤ì¤Þ¤Ç¤Îºî¶È¤ò¿¶¤êÊÖ¤í¤¦.
SMTP over TLS ¤ò»È¤¦ †
SMTP over TLS ¤ÎÀßÄê †
TLS ¤ÎÍøÍѤˤĤ¤¤Æ¤Ï¡¤ÀßÄê¤Î¤Þ¤¨¤Ë¸°¤È¾ÚÌÀ½ñ¤òÍÑ°Õ¤·¤Ê¤¤¤È¤¤¤±¤Ê¤¤.
web server ¤ÎÀßÄê¤Î»þ¤Ëºî¤Ã¤¿¸°¤È¾ÚÌÀ½ñ¤ò /etc/ssl ¤Ë(ÈÆÍÑŪ¤Ê̾Á°¤Ëľ¤·¤Æ)°ÜÆ°¤µ¤»¤Æ»È¤¦¤â¤è¤·*7¡¤¿·¤·¤¯ºî¤Ã¤Æ¤â¤è¤¤¤À¤í¤¦.
º£²ó¤Ï¸°¤È¾ÚÌÀ½ñ¤ò¿·¤¿¤Ëºî¤Ã¤Æ(¤ä¤êÊý¤Ï Web ¥µ¡¼¥Ð¤Î¼ø¶È¤Î²ó¤Î TLS/SSL ¤Î¹àÌܤ˽ñ¤¤¤Æ¤¢¤ë) /usr/local/etc/postfix ¤ËÃÖ¤¯¤³¤È¤Ë¤·¤è¤¦. ¤½¤·¤Æ¥Õ¥¡¥¤¥ë̾¤òÎ㤨¤Ð(¸°) postfix.key, (¾ÚÌÀ½ñ) postfix.crt ¤È¤·¤Æ¤ª¤¯.
¤¿¤À¤·¡¤¤³¤Î¥Õ¥¡¥¤¥ë¤¬Â¾¤Î¿Í¤ËÆɤá¤Æ¤·¤Þ¤¦¤Èº¤¤ë¤Î¤Ç¡¤ºî¤Ã¤¿¸å¤¹¤°¤Ë chmod ¤ÇÆɤ߽Ф·¸¢¸Â¤ÎÀßÄê¤ò¤·¤Ê¤¤¤È¤¤¤±¤Ê¤¤.
![]() °Ê²¼¡¤¤½¤Îºî¶È¤ò¹Ô¤ª¤¦.
°Ê²¼¡¤¤½¤Îºî¶È¤ò¹Ô¤ª¤¦.
cd /usr/local/etc/postfix openssl genrsa -out postfix.key 1024 openssl req -new -x509 -days 365 -key postfix.key -out postfix.crt
¾ÚÌÀ½ñºîÀ®»þ¤Ëʹ¤«¤ì¤ë¼ÁÌä¤Î±þÅú¤Ë¤Ä¤¤¤Æ¤Ï°ÊÁ°¤ÈƱ¤¸¤Ç¤è¤¤¤À¤í¤¦.
¤³¤¦¤·¤Æ¾ÚÌÀ½ñÅù¤¬ºîÀ®¤Ç¤¤¿¤é¡¤¤¹¤°¤µ¤Þ
chmod 400 postfix.key chmod 400 postfix.crt
¤È¤·¤Æ¤ª¤³¤¦.
¤µ¤Æ¡¤Postfix ¤ÎÀßÄê¤Ï¡¤ËܲȤΥɥ¥å¥á¥ó¥È(http://www.postfix.org/TLS_README.html)¤òÆɤó¤Ç¼«Ê¬¤Ê¤ê¤Ë¼è¼ÎÁªÂò¤¹¤ë¤³¤È¤Ë¤Ê¤ë.
¥µ¡¼¥Ð¤«¥¯¥é¥¤¥¢¥ó¥È¤«¤äǧ¾Ú¤ò¤É¤¦¤¹¤ë¤«¤Ê¤É¿¾¯¤ä¤ä¤³¤·¤¯¤Æ¤è¤¯¤ï¤«¤é¤Ê¤¤¤«¤È»×¤¦¤Î¤Ç¡¤º£²ó¤ÏÀßÄê¤ò½ñ¤¤¤Æ¤·¤Þ¤ª¤¦.
![]() º£²ó¤Ï¡¤ /usr/local/etc/postfix/main.cf ¤Ë
º£²ó¤Ï¡¤ /usr/local/etc/postfix/main.cf ¤Ë
smtpd_tls_cert_file = /usr/local/etc/postfix/postfix.crt
smtpd_tls_key_file = /usr/local/etc/postfix/postfix.key
smtpd_tls_loglevel = 1
smtpd_tls_received_header = yes
smtpd_tls_security_level = may
smtp_tls_loglevel = 1
smtp_tls_security_level = may
smtp_tls_note_starttls_offer = yes
¤Ê¤É¤È²Ã¤¨¤ì¤ÐÎɤ¤.
¤¿¤À¤·¡¤¤³¤ì¤Ï·ÐÏ©¤Î°Å¹æ²½¤À¤±¤Ç¤è¤¤¡¤¤È¤¤¤¦ÀßÄê¤Ê¤Î¤Ç¡¤Ç§¾Ú¤Þ¤Ç¤¤Á¤ó¤È¤·¤¿¤¤¿Í¤Ï¥É¥¥å¥á¥ó¥È¤ò¤¤Á¤ó¤ÈÆɤ⤦.
![]() Postfix ¤ÎÀßÄêÊýË¡¤¬¶áǯÊѤï¤Ã¤¿¤¿¤á¡¤web ¾å¤Ç»²¾È¤Ç¤¤ëÀßÄê¤Î¿¤¯¤Ï´û¤Ë¸Å¤¯¡¤¤¢¤Þ¤ê¿ä¾©¤Ç¤¤Ê¤¤¤Î¤Çα°Õ¤¹¤ë¤³¤È.
Postfix ¤ÎÀßÄêÊýË¡¤¬¶áǯÊѤï¤Ã¤¿¤¿¤á¡¤web ¾å¤Ç»²¾È¤Ç¤¤ëÀßÄê¤Î¿¤¯¤Ï´û¤Ë¸Å¤¯¡¤¤¢¤Þ¤ê¿ä¾©¤Ç¤¤Ê¤¤¤Î¤Çα°Õ¤¹¤ë¤³¤È.
¤³¤ÎÊÔ½¸¤¬½ª¤ï¤Ã¤¿¤é¡¤postfix ¤ò°ìöÄä»ß¤·¤Æ¤«¤éºÆµ¯Æ°¤¹¤ë.
/usr/local/etc/rc.d/postfix stop /usr/local/etc/rc.d/postfix start
ºÆµ¯Æ°»þ¤Ë²¿¤«¥¨¥é¡¼¤ä·Ù¹ð¤¬½Ð¤Æ¤¤¤Ê¤¤¤«Ãí°Õ¤·¤Æ¤ª¤³¤¦.
SMTP over TLS ¤ÎÆ°ºî³Îǧ †
![]() telnet localhost 25 ¤Ç³Îǧ¤·¤Æ¤ß¤è¤¦.
telnet localhost 25 ¤Ç³Îǧ¤·¤Æ¤ß¤è¤¦.
¤³¤ì¤Þ¤Ç¤ÈƱÍÍ¤Ë EHLO localhost ¤·¤Æ, ±þÅú¤¬
250-¥Û¥¹¥È̾
250-SIZE 10240000
250-VRFY
250-ETRN
250-STARTTLS ¢« ¤³¤ÎÂбþ¤¬ TLS/SSL ÍѤΤâ¤Î
250-AUTH LOGIN PLAIN DIGEST-MD5 CRAM-MD5
250-AUTH=LOGIN PLAIN DIGEST-MD5 CRAM-MD5
250-ENHANCEDSTATUSCODES
250-8BITMIME
250 DSN
¤Ê¤É¤È¤Ê¤ë.
¾å¤Î¤è¤¦¤Ë "250-STARTTLS" ¤È¤¤¤¦Éôʬ¤¬¤¢¤ì¤Ð¡¤¤È¤ê¤¢¤¨¤º TLS Âбþ¤ÎÆ°ºî¤ò¤·¤Æ¤¤¤ë¤³¤È¤¬¤ï¤«¤ë.
¤¢¤È¤ÏÁ°¤ÈƱÍÍ¤Ë ^], quit ¤ÇÈ´¤±¤è¤¦.
¤³¤ì¤¬½Ð¤Ê¤¤¤è¤¦¤Ê¤é²¿¤«¤ª¤«¤·¤¤¤Î¤Ç¤³¤ì¤Þ¤Ç¤Îºî¶È¤ò¿¶¤êÊÖ¤í¤¦.
![]()
¤µ¤Æ¡¤¤³¤³¤Ç SMTP ¤ÎÆ°ºî¥Á¥§¥Ã¥¯¤ËÊØÍø¤Ê¥Ä¡¼¥ë¤òƳÆþ¤·¤è¤¦. °Ê¹ß¤Î³Îǧºî¶È¤¬³Ú¤Ë¤Ê¤ë.
¤½¤ì¤Ï swaks (Swiss Army Knife SMTP) ¤È¤è¤Ð¤ì¤ë¤â¤Î¤Ç¤¢¤ê¡¤¤³¤ì¤Þ¤Ç¤Î telnet localhost 25 ¤È¤¤¤¦°ìÏ¢¤Îºî¶È¤ò¼«Æ°Åª¤Ë¤ä¤Ã¤Æ¤¯¤ì¤ëÊØÍø¤Ê¤â¤Î¤Ç¤¢¤ë.
¤È¤¤¤¦¤ï¤±¤Ç¤¤¤Ä¤â¤Î¤è¤¦¤Ë swaks ¤ò¥¤¥ó¥¹¥È¡¼¥ë¤·¤è¤¦.
portinstall swaks
¤È¤¹¤ì¤Ð¤è¤¤. ¥¤¥ó¥¹¥È¡¼¥ë»þ¤Ë¥ª¥×¥·¥ç¥óÁªÂò²èÌÌ
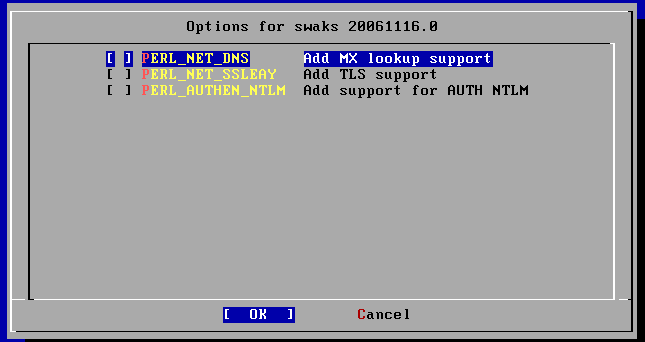
¤¬½Ð¤¿¤é¡¤¾¯¤Ê¤¯¤È¤â "MX lookup support" ¤È "TLS support" ¤È¤ò ON ¤Ë¤·¤Æ¤ª¤¤¤Æ¤«¤é¥¤¥ó¥¹¥È¡¼¥ë¤·¤è¤¦.
NTLM ¤Ïº£²ó¤Ï´Ø·¸¤Ê¤¤¤Î¤Ç³°¤·¤¿¤Þ¤Þ¤Ç¤è¤¤¤À¤í¤¦.
Àè¤Ø¿Ê¤à¤È¡¤¼«Æ°Åª¤ËÆþ¤ë p5-Net-SSLeay ¤Î¥¤¥ó¥¹¥È¡¼¥ë»þ¤Ë¥Æ¥¹¥È¤ò¤¹¤ë¤«¤É¤¦¤«Ê¹¤«¤ì¤ë¤³¤È¤¬¤¢¤ë¤¬¡¤¤³¤ì¤Ï "n" ¤Î¤Þ¤Þ¤Ç¹½¤ï¤Ê¤¤.
¤¢¤È¤Ï¥¤¥ó¥¹¥È¡¼¥ë¤¬½ª¤ï¤ë¤Î¤ò¤Þ¤È¤¦.
¤µ¤Æ, swaks ¤Î»È¤¤Êý¤Ï swaks --help ¤È¤¹¤ë¤È¥Þ¥Ë¥å¥¢¥ë¤¬Æɤá¤ë¤Î¤Ç¤½¤ì¤ò¤ß¤Æ¤â¤é¤¦¤È¤·¤Æ¡¤¤Þ¤º¤Ï¤ª¤µ¤é¤¤¤â·ó¤Í¤Æ¤³¤ì¤Þ¤Ç¤Î¥Æ¥¹¥È¤òºÆ¸½¤·¤Æ¤ß¤è¤¦.
![]() ¤Þ¤º¤Ïñ¤Ë MTA ¤¬Æ°ºî¤·¤Æ¤¤¤ë¤«¤Î³Îǧ¤ò¤·¤è¤¦.
¤Þ¤º¤Ïñ¤Ë MTA ¤¬Æ°ºî¤·¤Æ¤¤¤ë¤«¤Î³Îǧ¤ò¤·¤è¤¦.
swaks --server localhost
¤È¤¹¤ë¤È¡¤¥Æ¥¹¥È¥á¡¼¥ë¤Î°¸Àè¤òʹ¤¤¤Æ¤¯¤ë¤Î¤Ç, ¼«Ê¬¤Î¥¢¥«¥¦¥ó¥È̾¤òÅú¤¨¤è¤¦. ¤¹¤ë¤È
=== Trying localhost:25...
=== Connected to localhost.
<- 220 ¥Û¥¹¥È̾ ESMTP Postfix
-> EHLO freebsd7
<- 250-¥Û¥¹¥È̾
<- 250-PIPELINING
<- 250-SIZE 10240000
<- 250-VRFY
<- 250-ETRN
<- 250-STARTTLS
<- 250-AUTH LOGIN PLAIN DIGEST-MD5 CRAM-MD5
<- 250-AUTH=LOGIN PLAIN DIGEST-MD5 CRAM-MD5
<- 250-ENHANCEDSTATUSCODES
<- 250-8BITMIME
<- 250 DSN
-> MAIL FROM:<º¹½Ð¿Í>
<- 250 2.1.0 Ok
-> RCPT TO:<°¸Àè¥æ¡¼¥¶Ì¾>
<- 250 2.1.5 Ok
-> DATA
<- 354 End data with <CR><LF>.<CR><LF>
-> Date: Tue, 16 Dec 2008 20:17:54 +0900
-> To: °¸Àè¥æ¡¼¥¶Ì¾
-> From: º¹½Ð¿Í
-> Subject: test Tue, 16 Dec 2008 20:17:54 +0900
-> X-Mailer: swaks v20061116.0 jetmore.org/john/code/#swaks
->
-> This is a test mailing
->
-> .
<- 250 2.0.0 Ok: queued as B56D41D19C
-> QUIT
<- 221 2.0.0 Bye
=== Connection closed with remote host.
¤È MTA ¤È¤ä¤ê¼è¤ê¤·¤Æ¡¤¤½¤ÎÅÓÃæ·Ð²á¤ò¤¤Á¤ó¤È½ÐÎϤ·¤Æ¤¯¤ì¤ë.
¤¤¤Þ¤Ï¥Æ¥¹¥È¥á¡¼¥ë¤ò¼ÂºÝ¤ËÁ÷¤Ã¤¿¤Ï¤º¤Ê¤Î¤Ç¡¤¥¢¥«¥¦¥ó¥È¤Î¥Û¡¼¥à¥Ç¥£¥ì¥¯¥È¥ê¤Î Maildir/new ¤Ë¥á¡¼¥ë¤¬ÆϤ¤¤Æ¤¤¤ë¤Ï¤º¤Ç¤¢¤ë. ³Îǧ¤·¤Æ¤ß¤è¤¦.
¼¡¤Ë¡¤SMTP Auth ¤Î plainǧ¾Ú¤ò»î¤·¤Æ¤ß¤è¤¦.
¤¿¤À¤·¡¤¤¤¤Á¤¤¤Á¥á¡¼¥ë¤¬ÆϤ¯É¬Íפâ¤â¤¦¤Ê¤¤¤Î¤Ç¡¤Æ°ºî³Îǧ¤Î¤ß¤Ç¥á¡¼¥ë¤ÏÁ÷¤é¤Ê¤¤¤è¤¦¤Ë¤·¤è¤¦.
¤½¤ì¤Ë¤Ï¼¡¤Î¤è¤¦¤Ë¤¹¤ì¤Ð¤è¤¤.
swaks --auth PLAIN --server localhost --quit RCPT
¤¹¤ë¤ÈºÇ½é¤Ë(¼ÂºÝ¤Ë¤ÏÁ÷¤é¤Ê¤¤¤¬)¥Æ¥¹¥È¥á¡¼¥ë¤Î°¸Àè¤òʹ¤¤¤Æ¤¤Æ¡¤¤½¤Î¸å¤Ë SMTP Auth ¤Îǧ¾Ú¤ËɬÍפʥ桼¥¶Ì¾¤È¥Ñ¥¹¥ï¡¼¥É¤òʹ¤¤¤Æ¤¯¤ë¤Î¤ÇÅú¤¨¤è¤¦.
¤½¤·¤Æ¡¤¤½¤Î¸å¤Î¤ä¤ê¤È¤ê¤ÎÅÓÃæ¤Ë
¡Äά¡Ä
-> AUTH PLAIN ¥Ñ¥¹¥ï¡¼¥É¤òbase64²½¤·¤¿¤â¤Î
<- 235 2.7.0 Authentication successful
¡Äά¡Ä
¤È¤¤¤¦¤è¤¦¤Ë Auth plain ¤Ç¤Î SMTP Auth ¤¬¤¦¤Þ¤¯¤¤¤Ã¤¿¡¤¤È¤¤¤¦¤³¤È¤¬³Îǧ¤Ç¤¤ì¤Ð OK ¤À.
¼¡¤Ë SMTP Auth ¤Î CRAM-MD5 ǧ¾Ú¤ò»î¤·¤Æ¤ß¤ë. ¤½¤ì¤Ë¤Ï
swaks --auth CRAM-MD5 --server localhost --quit RCPT
¤È¤¹¤ì¤Ð¤è¤¤. ÆþÎϤϾå¤ÈƱÍͤÀ.
¤½¤·¤Æ¡¤¤½¤Î¸å¤Î¤ä¤ê¤È¤ê¤ÎÅÓÃæ¤Ë
¡Äά¡Ä
-> AUTH CRAM-MD5
<- 334 PDI3NTg4NzIyNTMuNDY4OTgzOUBGcmVlQlNENy5jYXMuY21jLm9zYWthLXUuYWMuanA+
-> cGFvb24gMTgyODJmNzRhNjZhOWMwY2FjN2YzZTliNDQ2NzQ3Y2Y=
<- 235 2.7.0 Authentication successful
¡Äά¡Ä
¤È¤¤¤¦¤è¤¦¤Ë Auth CRAM-MD5 ¤Ç¤Î SMTP Auth ¤¬¤¦¤Þ¤¯¤¤¤Ã¤¿¡¤¤È¤¤¤¦¤³¤È¤¬³Îǧ¤Ç¤¤ì¤Ð OK ¤À.
¤µ¤Æ¡¤¤ä¤Ã¤È´Î¿´¤Î SMTP over TLS ¤ò¥Æ¥¹¥È¤·¤è¤¦. ¤È¤¤¤Ã¤Æ¤â¤³¤³¤Þ¤Ç¤¯¤ì¤Ð¥Æ¥¹¥È¤Ï¤â¤¦´Êñ¤Ç¡¤
swaks -tls --server localhost
¤È¤¹¤ì¤Ð¤è¤¤. ¤¿¤À¤·¡¤Ç°¤Î°Ù¤Ë¥Æ¥¹¥È¥á¡¼¥ë¤ò¼ÂºÝ¤ËÁ÷¤í¤¦¤È¤·¤Æ¤¤¤ë.
¤³¤ì¤ò¼Â¹Ô¤·¤Æ¡¤swaks ¤Î½ÐÎϤ¬
¡Äά¡Ä
-> STARTTLS
<- 220 2.0.0 Ready to start TLS
=== TLS started w/ cipher DHE-RSA-AES256-SHA
¡Äά¡Ä
¤È¤¤¤¦¤è¤¦¤Ë TLS ¤ò»È¤Ã¤Æ̵»ö¤ËÆ°¤¤¤Æ¤¤¤ë¤è¤¦¤Ê¤é¤ÐÂç¾æÉפÀ.
¤â¤Á¤í¤ó, Maildir/new ¤Ë¼ÂºÝ¤Ë¥á¡¼¥ë¤¬ÆϤ¤¤Æ¤¤¤ë¤«¤â¥Á¥§¥Ã¥¯¤·¡¤¤½¤Î¥á¡¼¥ë¤Î¥Ø¥Ã¥ÀÉôʬ¤Ë
(using TLSv1 with cipher DHE-RSA-AES256-SHA (256/256 bits))
¤È¤¤¤¦µ½Ò¤¬¤¢¤ë¤³¤È¤â³Îǧ¤·¤Æ¤ª¤³¤¦.
ºÇ¸å¤Ë¡¤SMTP Auth ¤È SMTP over TLS ¤òÁȤ߹ç¤ï¤»¤Æ¤ß¤è¤¦. SMTP Auth ¤Îǧ¾Ú¤Ï¤Ê¤ó¤Ç¤â¤è¤¤. ¹¥¤¤Ê¤â¤Î¤ò»È¤Ã¤Æ¤ä¤Ã¤Æ¤ß¤è¤¦.
¶ñÂÎŪ¤Ë¤Ï¡¤Î㤨¤Ð¼¡¤Î¤è¤¦¤Ë¤¹¤ì¤Ð¤è¤¤(SMTP Auth ¤Ï¼«Æ°Åª¤ËÁª¤ó¤Ç¤â¤é¤¦ÀßÄê).
swaks --auth -tls --server localhost --quit RCPT
¤³¤³¤Ç½ÐÎϤòÃúÇ«¤ËÆɤó¤Ç¤ß¤è¤¦.
![]() ¤³¤Î½ÐÎϤòÆɤà¤È starttls ¤·¤Æ¤«¤é SMTP Auth¤·¤Æ¤¤¤ë ¤³¤È, ¤Ä¤Þ¤ê¡¤¡Ö°Å¹æ²½¤ò»Ï¤á¤Æ¤«¤é¥Ñ¥¹¥ï¡¼¥É¤ò¤ä¤ê¼è¤ê¤¹¤ë¡×½çÈ֤ˤʤäƤ¤¤ë¤³¤È¤ËÃíÌܤ»¤è.
¤³¤Î½ÐÎϤòÆɤà¤È starttls ¤·¤Æ¤«¤é SMTP Auth¤·¤Æ¤¤¤ë ¤³¤È, ¤Ä¤Þ¤ê¡¤¡Ö°Å¹æ²½¤ò»Ï¤á¤Æ¤«¤é¥Ñ¥¹¥ï¡¼¥É¤ò¤ä¤ê¼è¤ê¤¹¤ë¡×½çÈ֤ˤʤäƤ¤¤ë¤³¤È¤ËÃíÌܤ»¤è.
¤³¤ì¤Ï SMTP over TLS ¤ÈÁȤ߹ç¤ï¤»¤ë¤Ê¤é¤Ðǧ¾Ú(¥Ñ¥¹¥ï¡¼¥É¤Î¤ä¤ê¼è¤ê)¤Ïʿʸ¤Ç¤â°ÂÁ´¤Ê¤Ï¤º¤È¤¤¤¦¤³¤È¤Ç¤¢¤ë.
µÕ¤Ë¸À¤¨¤Ð¡¤over TLS ¤·¤Æ¤¤¤Ê¤¤¤Ê¤é¤Ð¥Í¥Ã¥È¥ï¡¼¥¯¤ò²ð¤·¤Æ Plainǧ¾Ú¤ò»È¤¦¤È´í¤Ê¤¤¤è¤È¤¤¤¦¤³¤È¤Ë¤Ê¤ë
![]() ¤µ¤é¤Ë;ÎϤ¬¤¢¤ë¤è¤¦¤À¤Ã¤¿¤é²¿¤«¼ê¸µ¤Î MUA ¤Ç starttls ¤ËÂбþ¤¹¤ë¤è¤¦¤ËÀßÄꤷ¤ÆÆ°ºî³Îǧ¤·¤Æ¤ß¤è.
¤µ¤é¤Ë;ÎϤ¬¤¢¤ë¤è¤¦¤À¤Ã¤¿¤é²¿¤«¼ê¸µ¤Î MUA ¤Ç starttls ¤ËÂбþ¤¹¤ë¤è¤¦¤ËÀßÄꤷ¤ÆÆ°ºî³Îǧ¤·¤Æ¤ß¤è.
IMAP/POP ¤ò»È¤¦ †
¤µ¤Æ¡¤¥æ¡¼¥¶°¸¤ËÆϤ¤¤¿¥á¡¼¥ë¤ò MUA ¤ËÅϤ¹¤Î¤Ë¹¤¯»È¤ï¤ì¤Æ¤¤¤ë POP/IMAP ¤Î¥µ¡¼¥Ð¤Ë¤Ä¤¤¤Æ¤â¿¨¤ì¤è¤¦.
¤¤¤Þ¤À¹¤¯»È¤ï¤ì¤Æ¤¤¤ë POP¡¤¥æ¡¼¥¶¤Ë¤È¤Ã¤Æ¤ÏÊØÍø¤À¤¬¥µ¡¼¥Ð¤Ø¤ÎÉéô¤¬¹â¤á¤Î¤¿¤á¤Ë¾¦¶È¥Ù¡¼¥¹¤Ç¤Ï¤Ê¤«¤Ê¤«ÍѤ¤¤é¤ì¤Ê¤¤ IMAP¡¤¤ÈÂç¤Þ¤«¤Ë¸À¤¨¤ë.
¤³¤³¤Ç¤Ï¡¤¾ÍèŪ¤Ê¤³¤È¤â¹Í¤¨¤Æ IMAP ¥µ¡¼¥Ð¤Ë¤Ä¤¤¤Æ³Ø½¬¤·¤Æ¤ß¤è¤¦. ¤Á¤Ê¤ß¤Ë¡¤POP ¥µ¡¼¥Ð¤Ï IMAP ¥µ¡¼¥Ð¤ËÈæ¤Ù¤ì¤Ðñ½ã¤Ê¤Î¤Ç¡¤IMAP ¥µ¡¼¥Ð¤¬°·¤¨¤ì¤ÐPOP ¥µ¡¼¥Ð¤Ë¤Ä¤¤¤Æ¤Ïº¤¤é¤Ê¤¤¤À¤í¤¦.
¤µ¤Æ¡¤IMAP ¥µ¡¼¥Ð¤È¤·¤Æ¤Ï courier-imap ¤¬¹¤¯»È¤ï¤ì¤Æ¤¤¤ë¤Î¤Ç¼ø¶È¤Ç¤â¤³¤ì¤òÍѤ¤¤è¤¦.
¤Ê¤ª¡¤courier-imap ¤ò¥¤¥ó¥¹¥È¡¼¥ë¤¹¤ë¤È°ì½ï¤Ë courier-pop ¤â¥¤¥ó¥¹¥È¡¼¥ë¤µ¤ì¤ë¤Î¤Ç¡¤POP ¥µ¡¼¥Ð¤ò¥¤¥ó¥¹¥È¡¼¥ë¤·¤¿¤¤¡¤¤È¤¤¤¦¤È¤¤Ë courier-imap ¤òÁªÂò¤·¤Æ¤â¤è¤¤.
courier-imap ¤Î¥¤¥ó¥¹¥È¡¼¥ë †
![]() ¤µ¤Æ¡¤¤¤¤Ä¤â¤Î¤è¤¦¤Ë ports ¥³¥ì¥¯¥·¥ç¥ó¤«¤é¥¤¥ó¥¹¥È¡¼¥ë¤·¤è¤¦.
¤µ¤Æ¡¤¤¤¤Ä¤â¤Î¤è¤¦¤Ë ports ¥³¥ì¥¯¥·¥ç¥ó¤«¤é¥¤¥ó¥¹¥È¡¼¥ë¤·¤è¤¦.
¤¿¤À¤·¡¤imap ¥µ¡¼¥Ð¤Î¥¤¥ó¥¹¥È¡¼¥ë¤ÎÁ°¤Ë courier-authlib(courier-imap ¤Îǧ¾Ú´Ø·¸¤À¤±È´¤½Ð¤·¤¿meta ports) ¤Î¥¤¥ó¥¹¥È¡¼¥ë¤ò¹Ô¤Ã¤Æ¤ª¤¯(¤½¤¦¤·¤Ê¤¤¤È¼Â¼ÁŪ¤Ë»È¤¨¤Ê¤¤).
¤¤¤Ä¤â¤Î¤è¤¦¤Ë
portsnap fetch portsnap update portinstall courier-authlib
¤È¤¹¤ë. ɬÍפʾ¤Î¥Ä¡¼¥ë¤â°ì½ï¤Ë¥¤¥ó¥¹¥È¡¼¥ë¤µ¤ì¤ë¤Î¤Ç¡¤¤·¤Ð¤é¤¯ÂԤȤ¦.
¤Þ¤¿ courier-authlib ¤Î¥¤¥ó¥¹¥È¡¼¥ë¤ÎÃʳ¬¤Ç½Ð¤ë¥ª¥×¥·¥ç¥ó²èÌÌ
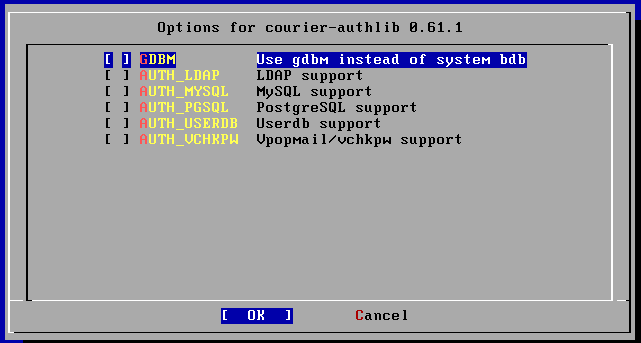
¤Ç¤Ï¤È¤ê¤¢¤¨¤º "Userdb support" ¤òÁª¤ó¤Ç¤ª¤³¤¦. ¤¢¤È¤Ï¥¹¥à¡¼¥º¤Ë¿Ê¤à¤À¤í¤¦.
¼¡¤Ë
portinstall courier-imap
¤È¤·¤Æ courier-imap ËÜÂΤò¥¤¥ó¥¹¥È¡¼¥ë¤¹¤ë. ºÇ½é¤Ë¥ª¥×¥·¥ç¥óÁªÂò²èÌÌ
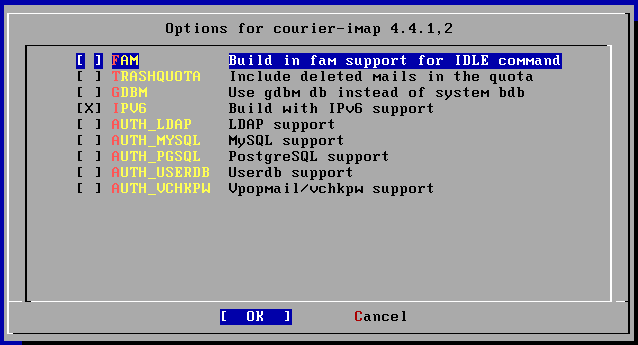
¤¬½Ð¤ë¤¬¡¤Â¿Ê¬¥Ç¥Õ¥©¥ë¥È¤Ç IPv6 ¤¬Áª¤Ð¤ì¤Æ¤¤¤ë¤À¤í¤¦.
IPv6 ¤Ï»È¤ï¤Ê¤¤¤Î¤Ç³°¤·¡¤µÕ¤ËÀè¤ÈƱÍÍ¤Ë "Userdb support" ¤òÁªÂò¤·¤ÆÀè¤Ë¿Ê¤â¤¦.
¤·¤Ð¤é¤¯ÂԤäƤ¤¤ë¤È¥¤¥ó¥¹¥È¡¼¥ë¤¬½ª¤ï¤ë¤À¤í¤¦.
¤µ¤Æ¡¤Ç°¤Î°Ù¤Ë¤¤¤Ä¤â¤Î¤è¤¦¤Ëº£²ó¥¤¥ó¥¹¥È¡¼¥ë¤µ¤ì¤¿Ê£¿ô¤Î¥½¥Õ¥È¤Î¥í¥°¤ò /var/log/ports ¤Î²¼¤«¤éõ¤·¤Æ¤ß¤Æ¡¤¥á¥Ã¥»¡¼¥¸¤òÈ´¤½Ð¤¹¤È¡¤
(security::courier-authlib-base.log ¤«¤é)
configure: WARNING: -----------------------------------------------------
configure: WARNING: expect not found - will not be able to change passwds
configure: WARNING: in webmail
configure: WARNING: -----------------------------------------------------
Added group "courier".
Added user "courier".
This port has installed the following files which may act as network
servers and may therefore pose a remote security risk to the system.
/usr/local/libexec/courier-authlib/authdaemond
This port has installed the following startup scripts which may cause
these network services to be started at boot time.
/usr/local/etc/rc.d/courier-authdaemond
If there are vulnerabilities in these programs there may be a security
risk to the system. FreeBSD makes no guarantee about the security of
ports included in the Ports Collection. Please type 'make deinstall'
to deinstall the port if this is a concern.
For more information, and contact details about the security
status of this software, see the following webpage:
(mail::courier-imap.log ¤«¤é)
In case you use authpam, you should put the following lines
in your /etc/pam.d/imap
auth required pam_unix.so try_first_pass
account required pam_unix.so try_first_pass
session required pam_permit.so
You will have to run /usr/local/share/courier-imap/mkimapdcert to create
a self-signed certificate if you want to use imapd-ssl.
And you will have to copy and edit the *.dist files to *
in /usr/local/etc/courier-imap.
This port has installed the following files which may act as network
servers and may therefore pose a remote security risk to the system.
/usr/local/libexec/courier-imap/couriertcpd
/usr/local/bin/couriertls
This port has installed the following startup scripts which may cause
these network services to be started at boot time.
/usr/local/etc/rc.d/courier-imap-imapd
/usr/local/etc/rc.d/courier-imap-pop3d
/usr/local/etc/rc.d/courier-imap-pop3d-ssl
/usr/local/etc/rc.d/courier-imap-imapd-ssl
If there are vulnerabilities in these programs there may be a security
risk to the system. FreeBSD makes no guarantee about the security of
ports included in the Ports Collection. Please type 'make deinstall'
to deinstall the port if this is a concern.
For more information, and contact details about the security
status of this software, see the following webpage:
¤È¤¤¤¦¥á¥Ã¥»¡¼¥¸¤¬¸«¤Ä¤«¤ë.
Á°¼Ô¤Î¥í¥°¥Õ¥¡¥¤¥ë¤ÎÆâÍƤÏÆäËÌäÂê¤Ê¤¤.
¸å¼Ô¤ÏÀßÄê¤Ë´Ø¤ï¤ëÉôʬ¤¬¤¢¤ë¤Î¤Ç½ÅÍפÀ(¾Ü¤·¤¯¤Ï¸å½Ò¤¹¤ë).
![]() SMTP Auth ¤ÎÅÓÃ椫¤é courier-imap ¤Î¥¤¥ó¥¹¥È¡¼¥ë¤ØÈô¤Ù¡¤¤È¸À¤ï¤ì¤Æ¤³¤³¤ØÍ褿¾ì¹ç¤Ï¡¤¸µ¤Î¤È¤³¤í¤ØÌá¤í¤¦.
SMTP Auth ¤ÎÅÓÃ椫¤é courier-imap ¤Î¥¤¥ó¥¹¥È¡¼¥ë¤ØÈô¤Ù¡¤¤È¸À¤ï¤ì¤Æ¤³¤³¤ØÍ褿¾ì¹ç¤Ï¡¤¸µ¤Î¤È¤³¤í¤ØÌá¤í¤¦.
courier-imap ¤ÎÀßÄê †
¤µ¤Æ¡¤¥¤¥ó¥¹¥È¡¼¥ë¤¬ºÑ¤à¤È /usr/local/etc/authlib ¤Ëǧ¾Ú´Ø·¸¤ÎÀßÄ꤬¡¤/usr/local/etc/courier-imap ¤Ë imap/pop ´Ø·¸¤ÎÀßÄê¥Õ¥¡¥¤¥ëÅù¤¬ÃÖ¤«¤ì¤ë.
¤Þ¤ºÇ§¾Ú´Ø·¸¤òÀ°Íý¤·¤è¤¦.
ǧ¾Úµ¡¹½¤½¤Î¤â¤Î¤ÎÀßÄê¤Ë¤Ä¤¤¤Æ¤Ï /usr/local/etc/authlib ¤ËÀßÄê¥Õ¥¡¥¤¥ë¤òÍÑ°Õ¤·¤Æ±¾¡¹¡Ä¤È¤Ê¤ë¤Î¤À¤¬¡¤º£²ó¤Ï userdb ¤·¤«Áª¤ó¤Ç¤¤¤Ê¤¤¤³¤È¤â¤¢¤Ã¤ÆÆäËÀßÄê¤ÏÉÔÍפʾõÂ֤Ǥ¢¤ë.
![]() ¼¡¤Ë¡¤over TLS/SSL ¤Ç»È¤¦¼«¸Êǧ¾Ú¾ÚÌÀ½ñ(courier-imap ¤Ï¤³¤ì¤òÍפ¹¤ë)¤òºî¤ë.
¼¡¤Ë¡¤over TLS/SSL ¤Ç»È¤¦¼«¸Êǧ¾Ú¾ÚÌÀ½ñ(courier-imap ¤Ï¤³¤ì¤òÍפ¹¤ë)¤òºî¤ë.
Àè¤Ëºî¤Ã¤¿¸°¤È¾ÚÌÀ½ñ¤È¤Ï°ã¤¦µ¡Ç½¤Î¤â¤Î¤Ê¤Î¤Ç¡¤¿·¤¿¤Ëºî¤í¤¦(ÊÑ´¹¤â²Äǽ¤È¤Ï»×¤¦¤¬).
ÊýË¡¤Ï´Êñ¤Ç¡¤¤Þ¤º /usr/local/etc/courier-imap ¤Ë¥µ¥ó¥×¥ë¤È¤·¤Æ¤ª¤¤¤Æ¤¢¤ëimapd.cnf.dist ¤È pop3d.cnf.dist ¤ò¥³¥Ô¡¼¤·¤Æ imapd.cnf ¤È pop3d.cnf ¤È¤¤¤¦¥Õ¥¡¥¤¥ë¤òºî¤ê¡¤Ãæ¤ò¤ß¤Æ [ req_dn ] °Ê²¼¤ÎÉôʬ¤ò¼«Ê¬¤Î¥µ¡¼¥Ð¤Ë¤¢¤ï¤»¤ÆŬÀÚ¤ËÊÔ½¸¤¹¤ë.
¶ñÂÎŪ¤Ë¤Ï
cd /usr/local/etc/courier-imap cp imapd.cnf.dist imapd.cnf cp pop3d.cnf.dist pop3d.cnf chmod u+w *.cnf emacs imapd.cnf emacs pop3d.cnf
¤È¤¤¤¦´¶¤¸¤À. ¤½¤ì¤«¤é¡¤
cd /usr/local/share/courier-imap/ ./mkimapdcert ./mkpop3dcert
¤È¤¹¤ë¤È¡¤/usr/local/share/courier-imap/ ¤Ë imapd.pem, pop3d.pem ¤È¤¤¤¦¼«¸Êǧ¾Ú¾ÚÌÀ½ñ¤¬¤Ç¤¤ë.
¥Õ¥¡¥¤¥ë̾¤â¾ì½ê¤âÆäËÊѹ¹¤òÍפ·¤Ê¤¤¤Î¤Ç¡¤¤³¤ì¤Ç¾ÚÌÀ½ñ¤ÎºîÀ®¤Ï¤ª¤ï¤ê.
¼¡¤Ë¡¤IMAP ËÜÂΤÎÀßÄê¤ò¹Ô¤ª¤¦.
![]() ¤¤¤Ä¤â¤Î¤è¤¦¤ËÇ°¤Î°Ù¥Ð¥Ã¥¯¥¢¥Ã¥×¤ò¤È¤Ã¤Æ¤«¤é.
¤¤¤Ä¤â¤Î¤è¤¦¤ËÇ°¤Î°Ù¥Ð¥Ã¥¯¥¢¥Ã¥×¤ò¤È¤Ã¤Æ¤«¤é.
/usr/local/etc/courier-imap ¤Î imapd ¤È¤¤¤¦¥Õ¥¡¥¤¥ë¤òÊÔ½¸¤·¤Æ¡¤¹àÌܤΠ"IMAP_CAPABILITY" ¤È "IMAP_CAPABILITY_TLS" ¤òǧ¾Ú¤¢¤ê¤Ë½¤Àµ¤¹¤ë.
¶ñÂÎŪ¤Ë¤Ï¡¤
IMAP_CAPABILITY="IMAP4rev1 UIDPLUS CHILDREN NAMESPACE THREAD=ORDEREDSUBJECT THREAD=REFERENCES SORT QUOTA AUTH=CRAM-MD5 AUTH=CRAM-SHA1 AUTH=CRAM-SHA256 IDLE"
IMAP_CAPABILITY_TLS="$IMAP_CAPABILITY AUTH=PLAIN AUTH=LOGIN"
¤ÎÆ󥫽ê¤ò½¤Àµ(²èÌ̤ÎÅÔ¹ç¤ÇÀÞ¤êÊÖ¤·¤Æ¤¤¤ë¤¬¡¤³Æ¡¹ 1¹Ô¤º¤Ä¤Ê¤Î¤ÇÃí°Õ)¤¹¤ì¤Ð¤è¤¤.
³Æ¡¹¡¤¥Ç¥Õ¥©¥ë¥ÈÃͤ«¤éÊѤï¤Ã¤¿Éôʬ¤ò¸«¤ì¤Ð²¿¤ò¤·¤¿¤«¤Ï¤ï¤«¤ë¤À¤í¤¦. ¤Á¤Ê¤ß¤ËÆó¤ÄÌܤκǸå¤Î AUTH=LOGIN ¤Ï(ŬÅö¤À¤¬) MS Âкö¤Ç¤¢¤ë.
¤¢¤È¡¤POP ¥µ¡¼¥Ð¤â»È¤¤¤¿¤¤¤Ê¤é¤Ð¡¤¤È¤ê¤¢¤¨¤ºÆ±ÍÍ¤Ë pop3d ¤È¤¤¤¦¥Õ¥¡¥¤¥ë(ÊÔ½¸¤¹¤ë¤Ê¤é¥Ð¥Ã¥¯¥¢¥Ã¥×¤·¤Æ¤«¤é)¤ÎÃæ¤Î2²Õ½ê¤ò
POP3AUTH="CRAM-MD5 CRAM-SHA1"
POP3AUTH_TLS="LOGIN PLAIN"
¤È½¤Àµ¤·¤Æ¤ª¤±¤Ð¤è¤¤.
¤µ¤Æ¡¤¤¢¤È¤Ï IMAP ¥µ¡¼¥Ð¤Îµ¯Æ°½àÈ÷¤Ç¤¢¤ë¤¬¡¤¤³¤ì¤Ï¾ðÊ󤬤ɤ¦¤Ë¤â¾¯¤Ê¤¤.
¤·¤«¤¿¤Ê¤¤¤Î¤Ç¡¤courier-imap ¥¤¥ó¥¹¥È¡¼¥ë»þ¤Î¥á¥Ã¥»¡¼¥¸¤òÆɤà¤È¡¤ºÇ¸å¤ÎÊý¤Ë
This port has installed the following startup scripts which may cause
¡Äά¡Ä
¤È¤¢¤ë¤Î¤Ç¡¤¼ÂºÝ¤Ï¤³¤ì¤é¤Î¥¹¥¯¥ê¥×¥È¤¬µ¯Æ°Áàºî¤ò¹Ô¤¦¤Î¤À¤È¤¤¤¦¤³¤È¤Ï¤ï¤«¤ë.
¤½¤·¤ÆÇ°¤Î°Ù¤Ë /usr/local/etc/rc.d ¥Ç¥£¥ì¥¯¥È¥ê¤òÇÁ¤¤¤Æ¤ß¤ë¤È¡¤¤³¤ì¤é¤Ï³Î¤«¤Ë¤¢¤ê¡¤¤«¤Ä¡¤Â¾¤Ë courier-authdaemond ¤È¤¤¤¦¥Õ¥¡¥¤¥ë¤â¤¢¤ê, ¤³¤ì¤âƱÍͤÎÌò³ä¤òô¤¦¤³¤È¤¬¿ä¬¤Ç¤¤ë.
¤½¤³¤Ç¤³¤ì¤é¤Î¥Õ¥¡¥¤¥ë¤Î¤¦¤Á¡¤IMAP ¥µ¡¼¥Ð¤Îµ¯Æ°¤Ë´ØÏ¢¤·¤½¤¦¤Ê¥¹¥¯¥ê¥×¥È "courier-authdaemond", "courier-imap-imapd", "courier-imap-imapd-ssl" ¤Î3¤Ä¤òľ¤ËÆɤó¤Ç¤ß¤è¤¦.
¤¹¤ë¤È¡¤Î㤨¤Ð courier-imap-imapd ¤Ë¤Ï
# Define these courier_imap_imapd_* variables in one of these files:
# /etc/rc.conf
# /etc/rc.conf.local
# /etc/rc.conf.d/courier_imap_imapd
#
# DO NOT CHANGE THESE DEFAULT VALUES HERE
courier_imap_imapd_enable=${courier_imap_imapd_enable-"NO"}
¤È½ñ¤¤¤Æ¤¢¤ê¡¤¤É¤¦¤ä¤é /etc/rc.conf ¤Ë courier_imap_imapd_enable ¤ÎÆâÍƤòµ½Ò¤¹¤ì¤ÐÎɤµ¤½¤¦¤À¤È¤¤¤¦¤³¤È¤¬¿ä¬¤Ç¤¤ë.
ƱÍͤ˾£²¤Ä¤Î¥¹¥¯¥ê¥×¥È¥Õ¥¡¥¤¥ë¤Ë¤âµ½Ò¤¬¤¢¤ê¡¤¤³¤ì¤é¤òÁí¹ç¤¹¤ë¤È /etc/rc.conf ¤Ë
# for IMAP
courier_authdaemond_enable="YES"
courier_imap_imapd_enable="YES"
courier_imap_imapd_ssl_enable="YES"
¤Ê¤É¤È½ñ¤¹þ¤à¤Î¤¬Îɤµ¤½¤¦¤À¤È¤¤¤¦¤³¤È¤¬¿ä¬¤Ç¤¤ë.
![]() ¾å¤Î¤è¤¦¤Ë½ñ¤¹þ¤ß¡¤Ç°¤Î°Ù¤Ë¥ê¥Ö¡¼¥È¤·¤Æ¤ª¤³¤¦.
¾å¤Î¤è¤¦¤Ë½ñ¤¹þ¤ß¡¤Ç°¤Î°Ù¤Ë¥ê¥Ö¡¼¥È¤·¤Æ¤ª¤³¤¦.
¤½¤Î¸å¡¤lsof ¤Ê¤É¤òÍѤ¤¤Æ imapd ¤¬Æ°¤¤¤Æ¤¤¤ë¤³¤È¤ò³Îǧ¤·¤è¤¦. Î㤨¤Ð
lsof -i4 | grep -i imap
¤È¤·¤Æ½ÐÎϤò¤ß¤ë¡¤¤Ê¤É¤Ç¤¢¤ë.
imapd ¤¬Æ°¤¤¤Æ¤¤¤Ê¤¤¤è¤¦¤Ê¤é¤Ð¤â¤¦°ìÅÙÀßÄê¤ò¸«Ä¾¤½¤¦.
IMAP ÍѤΥ桼¥¶¾ðÊó¤ÎÅÐÏ¿ †
º£²ó¤Ï userdb ¤Ç¥Ñ¥¹¥ï¡¼¥É¾È¹ç¤ò¹Ô¤¦¤è¤¦¤Ë¥¤¥ó¥¹¥È¡¼¥ë¤·¤¿¤Î¤Ç, IMAP ÍѤ˥桼¥¶¾ðÊó¤òÅÐÏ¿¤·¤Æ¤ª¤«¤Ê¤¤¤È¤¤¤±¤Ê¤¤.
![]()
¶ñÂÎŪ¤Ë¤Ï¼¡¤Î½çÈ֤Ǻî¶È¤ò¹Ô¤¨¤Ð¤è¤¤.
¤è¤ê¾Ü¤·¤¯ÃΤꤿ¤¤¼Ô¤Ï¡¤http://www.courier-mta.org/FAQ.html ¤Ê¤É¤ò»²¾È¤Î¤³¤È.
- ¤Þ¤º¶õ¤Î¥Ç¥£¥ì¥¯¥È¥ê /usr/local/etc/userdb ¤òºîÀ®¤¹¤ë.
cd /usr/local/etc mkdir userdb chmod 700 ./userdb
¤Ê¤É¤È¤¹¤ì¤Ð¤è¤¤. - (¥Ñ¥¹¥ï¡¼¥É°Ê³°¤Î)¥æ¡¼¥¶¾ðÊó¤òÅÐÏ¿¤¹¤ë
- /etc/passwd ¤«¤éºî¤ëÊýË¡
´û¤Ë¥·¥¹¥Æ¥à¤Î¥æ¡¼¥¶¤Ç¤â¤¢¤ë¤Ê¤é¤Ð´Êñ¤Ç¤ª¤¹¤¹¤á. ¤³¤Á¤é¤Ç¤ä¤í¤¦.
pw2userdb ¥³¥Þ¥ó¥É¤òÍѤ¤¤Æcd /usr/local/etc/userdb/ pw2userdb | grep ¥æ¡¼¥¶Ì¾ >> ./users
¤È¤¹¤ì¤Ð¤è¤¤. - Îí¤«¤éºî¤ëÊýË¡.
userdb ¥³¥Þ¥ó¥É¤ÇľÀܤ¤¤í¤¤¤í»ØÄꤹ¤ëÊýË¡. ¤Á¤ç¤¤ÌÌÅÝ.userdb "john@example.com" set home=/home/vmail \ mail=/home/vmail/Maildir-john-example uid=UUU gid=GGG"
¤Ê¤É¤È¤¹¤ëÊýË¡.
- /etc/passwd ¤«¤éºî¤ëÊýË¡
- ¥Ñ¥¹¥ï¡¼¥É¤òÀßÄꤹ¤ë.
cd /usr/local/etc/userdb userdbpw -hmac-md5 | userdb users/¥æ¡¼¥¶Ì¾ set hmac-md5pw
¤È¤¹¤ì¤Ð¤è¤¤. ¤³¤Î hmac-md5 ¤È¤¤¤¦¤Î¤¬ CRAM-MD5 ¤ÇÍøÍѤµ¤ì¤ë.
¤¦¤Þ¤¯¤¤¤Ã¤Æ¤¤¤ë¤«¤É¤¦¤«¡¤users ¥Õ¥¡¥¤¥ë¤òÆɤó¤Ç³Îǧ¤·¤Æ¤ª¤³¤¦. - Äɲá¤Êѹ¹²Õ½ê¤ò͸ú¤Ë¤¹¤ë.
makeuserdb
¤È¤¹¤ì¤Ð¤è¤¤.
¤Ç¤Ï¤³¤³¤Ç¾å¤Î¼ê½ç¤Ë¤·¤¿¤¬¤Ã¤Æ IMAP ÍѤΥ桼¥¶¾ðÊó¤òÅÐÏ¿¤·¤Æ¤ª¤³¤¦.
![]() ¤³¤Î¼ê½ç¤Ï¤¤¤«¤Ë¤âÌÌÅݤÀ¤·¡¤´Ö°ã¤¨¤ä¤¹¤½¤¦¤Ç¿´ÇÛ¤À.
¤³¤Î¼ê½ç¤Ï¤¤¤«¤Ë¤âÌÌÅݤÀ¤·¡¤´Ö°ã¤¨¤ä¤¹¤½¤¦¤Ç¿´ÇÛ¤À.
¤½¤³¤Ç¡¤¼ÂºÝ¤Ë courier-imap ¤ò»È¤¦¾ì¹ç¤Ë¤Ï ports ¤«¤é courierpasswd ¤ò¥¤¥ó¥¹¥È¡¼¥ë¤·¤Æ¤³¤ì¤ò»ÈÍѤ·¤¿Êý¤¬¤è¤¤¤À¤í¤¦.
courier-imap ¤ÎÆ°ºî³Îǧ †
SMTP Auth ¤Î»þ¤ÈƱÍͤˡ¤2¤Ä¤Îʸ»úüËö¥¨¥ß¥å¥ì¡¼¥¿¤òÍÑ°Õ¤·¤ÆÆ°ºî³Îǧ¤ò¹Ô¤¦.
¤¿¤À¤·¡¤Æ°ºî³Îǧ¤Ç¤â¤¿¤Ä¤¤¤Æ¤¤¤ë¤È courier-imap ¥µ¡¼¥Ð¤¬Àܳ¤òÀڤäƤ·¤Þ¤¦¤Î¤Ç¡¤¤³¤ì¤Ë;͵¤ò»ý¤¿¤»¤Æ¤ª¤¤¿¤¤.
![]() ¤½¤Î¤¿¤á¤Î½àÈ÷¤òÀè¤Ë¤·¤Æ¤ª¤³¤¦. ¶ñÂÎŪ¤Ë¤Ï¡¤/usr/local/etc/courier-imap/imapd ¥Õ¥¡¥¤¥ë¤Î
¤½¤Î¤¿¤á¤Î½àÈ÷¤òÀè¤Ë¤·¤Æ¤ª¤³¤¦. ¶ñÂÎŪ¤Ë¤Ï¡¤/usr/local/etc/courier-imap/imapd ¥Õ¥¡¥¤¥ë¤Î
IMAP_IDLE_TIMEOUT=60
¤È¤¤¤¦Éôʬ¤¬¡Ö60ÉÃÈ¿±þ¤¬¤Ê¤±¤ì¤ÐÀÚÃǡפȤ¤¤¦°ÕÌ£¤Ê¤Î¤Ç¡¤¤³¤Î 60 ¤òŬÅö¤ËÁý¤ä¤·¤Æ¤ª¤±¤Ð¤è¤¤.
Î㤨¤Ð 180 ¤°¤é¤¤¤Ë¤¹¤ì¤ÐÌäÂê¤Ê¤¤¤À¤í¤¦.
¤Ê¤ª¡¤¤³¤Î¥Õ¥¡¥¤¥ë¤òÊÔ½¸¤·¤¿¤é courier-imap ¥µ¡¼¥Ð¤ò°ìöÄä¤á¤ÆºÆÅÙÆ°¤«¤µ¤Ê¤¤¤È¤¤¤±¤Ê¤¤¤Î¤Ç¤½¤¦¤·¤Æ¤ª¤³¤¦.
¶ñÂÎŪ¤Ë¤Ï
/usr/local/etc/rc.d/courier-imap-imapd stop /usr/local/etc/rc.d/courier-imap-imapd start
¤È¤·¤Æ¤ª¤±¤Ð¤è¤¤.
![]() ¤µ¤Æ¡¤¤Ç¤Ï SMTP Auth ¤Î»þ¤ÈƱ¤¸¤è¤¦¤Ë¥Æ¥¹¥È¤·¤Æ¤ß¤è¤¦.
¤µ¤Æ¡¤¤Ç¤Ï SMTP Auth ¤Î»þ¤ÈƱ¤¸¤è¤¦¤Ë¥Æ¥¹¥È¤·¤Æ¤ß¤è¤¦.
Shell-A ¤Ç¡¤telnet localhost 143 ¤È¤¹¤ë¤È
Trying 127.0.0.1...
Connected to localhost.
Escape character is '^]'.
* OK [CAPABILITY IMAP4rev1 UIDPLUS CHILDREN NAMESPACE THREAD=ORDEREDSUBJECT THREAD=REFERENCES SORT QUOTA AUTH=CRAM-MD5 AUTH=CRAM-SHA1 AUTH=CRAM-SHA256 IDLE ACL ACL2=UNION STARTTLS] Courier-IMAP ready. Copyright 1998-2008 Double Precision, Inc. See COPYING for distribution information.
¤Ê¤É¤È¸À¤Ã¤Æ¤¯¤ë. ¤³¤³¤Ç¡¤
a authenticate cram-md5
¤ÈÆþÎϤ¹¤ë¤È
+ PG5hbmlrYS1pbWFwQHNlcnZlcj4=
¤Ê¤É¤È¥µ¡¼¥Ð¤«¤éʸ»úÎó¤¬Á÷¤é¤ì¤Æ¤¯¤ë.
¤³¤Îʸ»úÎó PG5hbmlrYS1pbWFwQHNlcnZlcj4= ¤ËÂФ·¤Æ¡¤Àè¤Û¤É¤ÈƱÍÍ¤Ë Shell-B¤Ç userdb-test-cram-md5 ¥³¥Þ¥ó¥É¤ò»È¤Ã¤ÆÊÖÅúÍÑʸ»úÎó¤òºî¤ë.
Î㤨¤Ð¼¡¤Î¤è¤¦¤Ë¤Ê¤ë¤À¤í¤¦.
Username? testuser ¢« IMAP ÍѤËÅÐÏ¿¤·¤¿¥æ¡¼¥¶Ì¾
Password? password ¢« IMAP ÍѤËÅÐÏ¿¤·¤¿¥Ñ¥¹¥ï¡¼¥É
Send: AUTH CRAM-MD5 (or for imap, A AUTHENTICATE CRAM-MD5)
Paste the challenge here:
+ PG5hbmlrYS1pbWFwQHNlcnZlcj4= ¢« º£¤Îʸ»úÎó¤òÄ¥¤êÉÕ¤±¤ë
Send this response:
dGVzdHVzZXIgYjlkMDA5MzQ4YmVjMzlkNzcwMWU4MWRiZWE3NmZhN2M= ¢« ·ë²Ì¤¬Ê֤äƤ¯¤ë
¤³¤ÎºÇ¸å¤Îʸ»úÎó dGVzdHVzZXIgYjlkMDA5MzQ4YmVjMzlkNzcwMWU4MWRiZWE3NmZhN2M= ¤¬ IMAP ¥µ¡¼¥Ð¤Ë½Ð¤¹¤Ù¤ÊÖ»ö¤Ë¤Ê¤ë¤Î¤Ç¡¤¤³¤ì¤ò Shell-A ¤Ç¤Îºî¶È¤Î³¤¤ËÄ¥¤êÉÕ¤±¤ÆÊÖÅú¤È¤¹¤ë.
¤½¤·¤Æ
a OK LOGIN Ok.
¤È¤Ê¤ì¤Ð¡¤IMAP ¥µ¡¼¥Ð¤Îǧ¾Ú¤¬Ä̤俤Ȥ¤¤¦¤³¤È¤Ë¤Ê¤ê¡¤Æ°ºî¤¬³Îǧ¤Ç¤¤¿¤³¤È¤Ë¤Ê¤ë*8.
¤Ê¤ª¡¤POP ¥µ¡¼¥Ð¤òΩ¤Á¾å¤²¤¿¤Ê¤é¤ÐƱÍͤ˥ƥ¹¥È¤¬²Äǽ¤Ç¤¢¤ë.
¤½¤ÎºÝ¤Ï
telnet localhost 110
¤È¤¹¤ë¤È¡¤
Trying 127.0.0.1...
Connected to localhost.
Escape character is '^]'.
+OK Hello there.
¤È¤Ê¤ë¤Î¤Ç¡¤¤³¤³¤Ç
capa
¤ÈÆþÎϤ¹¤ë¤È
SASL CRAM-MD5 CRAM-SHA
STLS
TOP
USER
LOGIN-DELAY 10
PIPELINING
UIDL
IMPLEMENTATION Courier Mail Server
.
¤È±þÅú¤¬Ê֤äƤ¯¤ë.
¤³¤³¤Ç
auth cram-md5
¤ÈÆþÎϤ¹¤ë¤È
+ PG5hbmlrYS1pbWFwQHNlcnZlcj4=
¤Ê¤É¤È¥µ¡¼¥Ð¤«¤éʸ»úÎó¤¬Á÷¤é¤ì¤Æ¤¯¤ë¤Î¤Ç¡¤
¤³¤ì¤Ë userdb-test-cram-md5 ¥³¥Þ¥ó¥É¤ÇÊÖÅúÍÑʸ»úÎó¤òºîÀ®¤·¤ÆÄ¥¤êÉÕ¤±¤ë¤È
+OK logged in.
¤Èǧ¾Ú¤µ¤ì¤ë¤È¤¤¤¦Î®¤ì¤Ë¤Ê¤ë.
![]() ;͵¤¬¤¢¤ì¤ÐŬÅö¤Ê MUA ¤Ç IMAP ¥µ¡¼¥Ð¤ËÀܳ¤·¤Æ¤ß¤è¤¦.
;͵¤¬¤¢¤ì¤ÐŬÅö¤Ê MUA ¤Ç IMAP ¥µ¡¼¥Ð¤ËÀܳ¤·¤Æ¤ß¤è¤¦.
¤µ¤é¤Ë;͵¤¬¤¢¤ì¤Ð¡¤IMAP over TLS/SSL ÀßÄê¤Ç¥µ¡¼¥Ð¤ËÀܳ¤·¤Æ¤ß¤è¤¦.
¥ì¥Ý¡¼¥È †
ÅÓÃæ¤Ç¡ÖÄ´¤Ù¤è¡×¤È»Ø¼¨¤µ¤ì¤¿»ö¹à¤Ë¤Ä¤¤¤ÆÄ´ºº¤ò¹Ô¤¤¡¤Êó¹ð¤»¤è.
¤Þ¤¿¡¤ËÜÆü¹Ô¤Ã¤¿ºî¶È¤Ë¤Ä¤¤¤ÆÊó¹ð¤»¤è.
¤â¤Á¤í¤ó³Æ¼«¤Î
- ½ê°(³ØÉô¡¤³Ø²Ê)
- ³ØÀÒÈÖ¹æ
- ³Øǯ
- »á̾
- Æü»þ
- ´Î¿´¤Î¥ì¥Ý¡¼¥ÈÆâÍÆ(ÆÀ¤¿Ãθ«¡¤ºî¶È¤Ë¤Ä¤¤¤Æµ¤¤Å¤¤¤¿¤³¤ÈÅù)
¤ò½ñ¤¯¤Î¤ò˺¤ì¤Ê¤¤¤è¤¦¤Ë.
about Icons †
Some icons in this page are downloadable at ICONFINDER.
The "note" icon designed by Marco Martin is distributed with the LGPL licence
and the "warning" icon designed by Alexandre Moore with the GPL licence.
*1 Ç°¤Î°Ù¤Ë saslpasswd2 ¥³¥Þ¥ó¥É¤Î¥Þ¥Ë¥å¥¢¥ë¤ò¸«¤ë¤È¡¤Â¾¤Ë sasldblistusers2 ¤È¤¤¤¦¥³¥Þ¥ó¥É¤¬¤¢¤ë¡¤¤È¤¤¤¦¤³¤È¤¬Â¾¤Ëʬ¤«¤ë¤°¤é¤¤¤«.
*2 \0 ¤Ï¥Ì¥ë¥Ð¥¤¥È
*3 ¤Á¤Ê¤ß¤Ë¡¤base64 ¥¨¥ó¥³¡¼¥É¤·¤¿¥Æ¥¥¹¥È¤Ï¡¤"mmencode -u" ¤Ç¸µ¤ËÌ᤹¤³¤È¤¬¤Ç¤¤ë.
*4 \0000 ¤È¤Ê¤Ã¤Æ¤¤¤ë¤È¤³¤í¤Ï \0 ¤Ç¤â¤è¤¤¤Î¤À¤¬¡¤¥Ñ¥¹¥ï¡¼¥É¤Î1ʸ»úÌܤ¬¿ô»ú¤À¤Ã¤¿¤ê¤¹¤ë¤È¤¦¤Þ¤¯¤¤¤«¤Ê¤¤¤Î¤Ç¡¤Ç°¤Î°Ù¤Ë¤³¤¦¤·¤Æ¤¢¤ë.
*5 ʸ»úüËö¥¨¥ß¥å¥ì¡¼¥¿¤Ë³Ð¤¨¤µ¤»¤Æ¤·¤Þ¤¨¤Ð³Ú¤À¤í¤¦
*6 ¤³¤ì¤ò "mmencode -u" ¤Ë¤«¤±¤ë¤È¼ÂºÝ¤Îʸ»úÎ󤬤狼¤ë
*7 ¤³¤Î¾ì¹ç¤Ï¤â¤Á¤í¤ó apache ¤ÎÀßÄê¤âľ¤µ¤Ê¤¤¤È¤¤¤±¤Ê¤¤
*8 ¤³¤³¤Ç¤Ï ^] ¤È¤·¤Æ¤«¤é quit ¤È¤¹¤ì¤ÐÈ´¤±¤é¤ì¤ë
źÉÕ¥Õ¥¡¥¤¥ë: